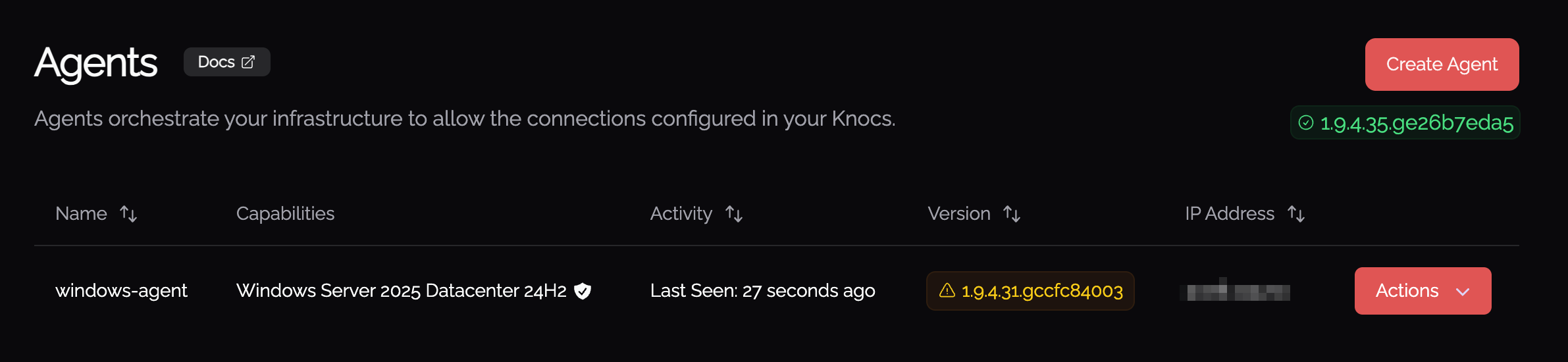
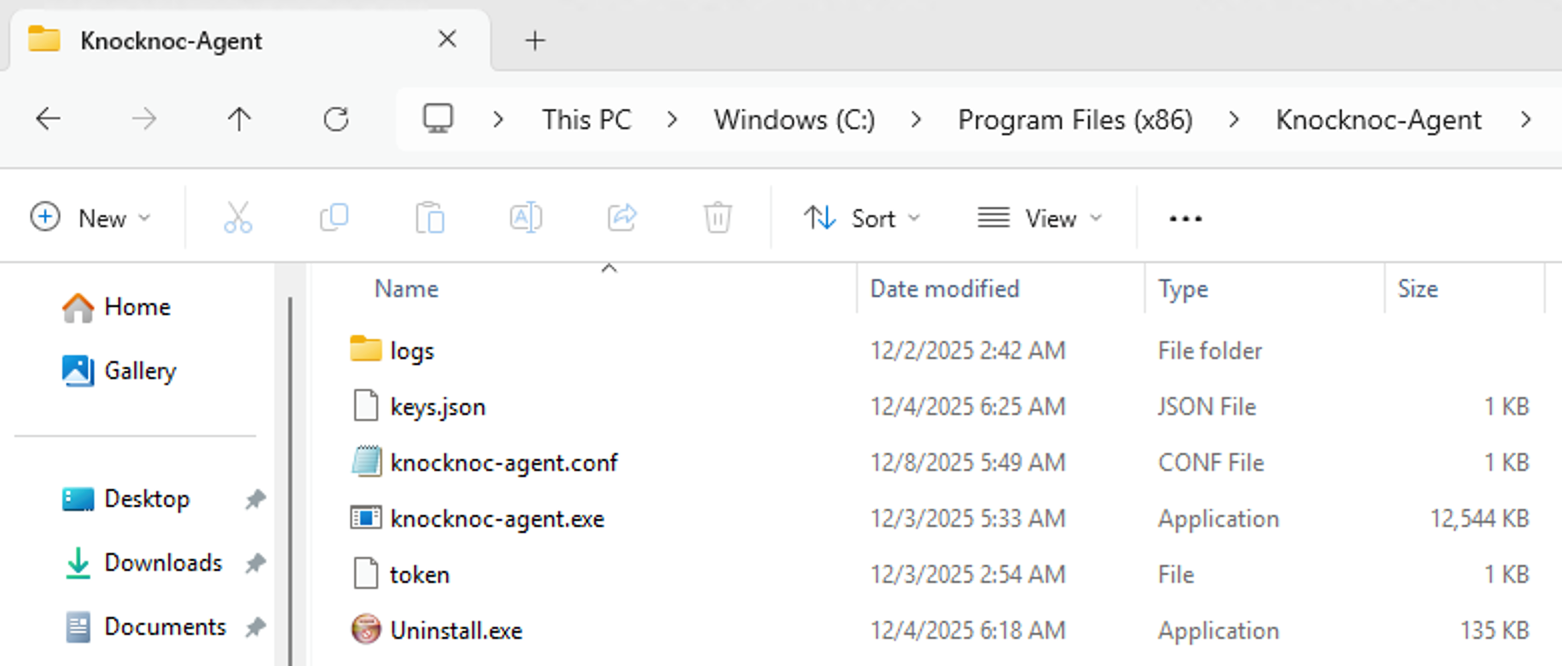
Windows Agent Installation
On a Windows machine as an Admin, download and install the Orchestration Agent. It will install as a service by default. You then provide token information to connect to your Knocknoc Server for centralized management.
This is not installed by end users for access. This orchestration agent controls access but is not required by end users.
Requirements
- Supported Windows version (e.g. Windows Server 2016+ or Windows 10/11 Pro/Enterprise)
- Knocknoc Agent version 25.12 or later
- Local admin rights on the Windows server where the agent will run
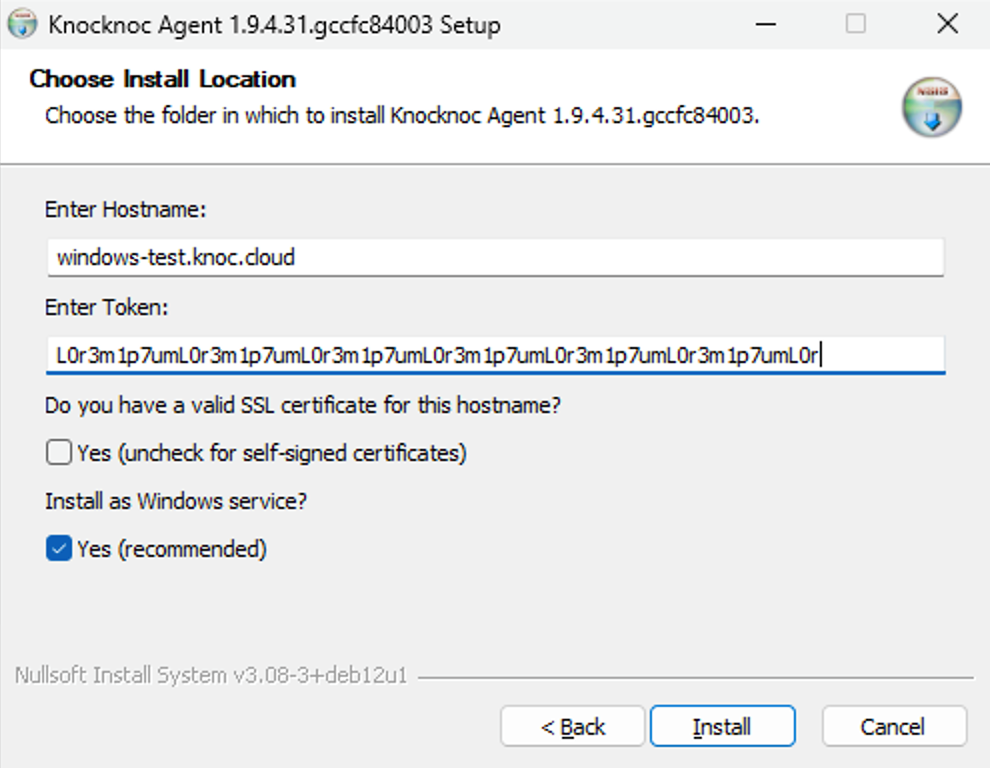
Installing the Agent
- Download the Windows Knocknoc agent from here.
- Follow the installation process.
- Log in to your Knocknoc Server, eg: https://myserver.example.org/admin/
- Create an Agent
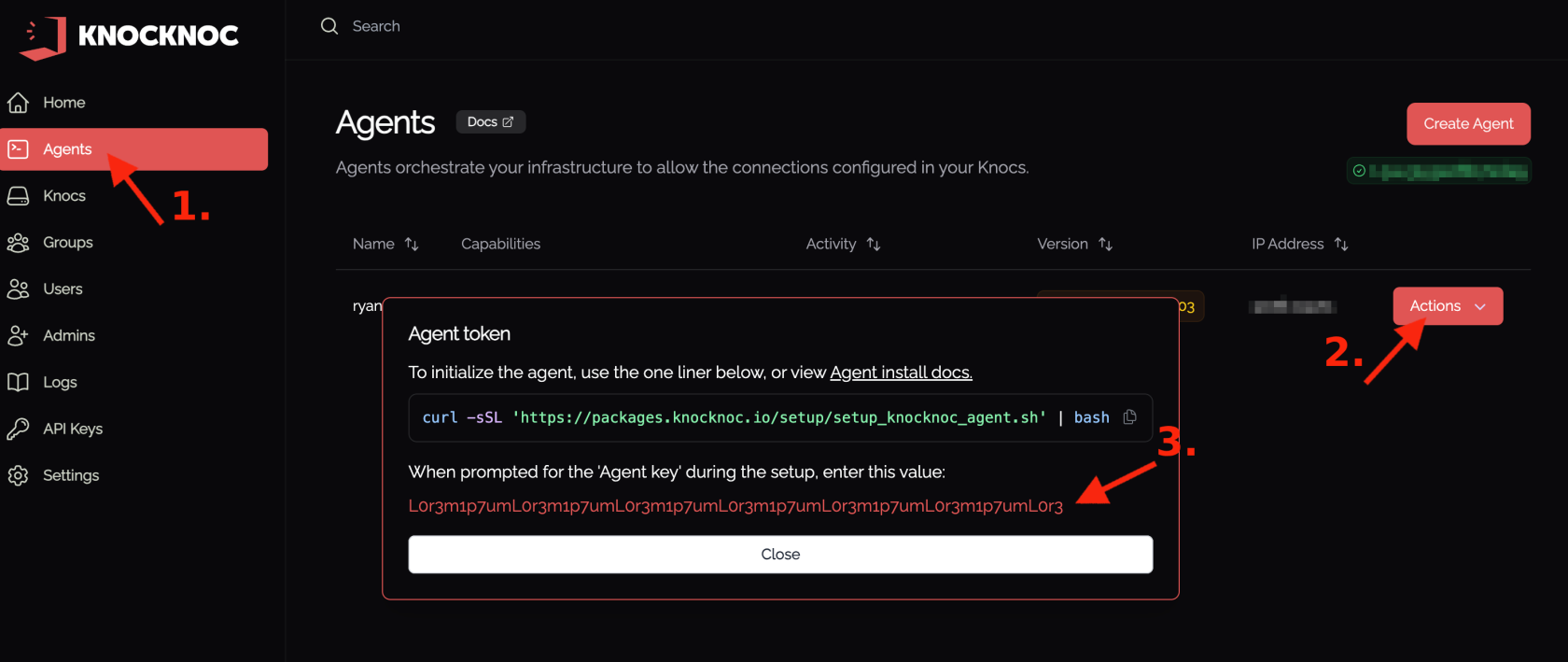
- Copy the token for the Windows Agent. You can obtain the token again as an Admin if needed.
- Copy the URL of your Knocknoc Server
- You are now ready to provide this to the Windows installer
- Lastly, confirmation that it's up and running.
You're now ready!
You have two major options with the Windows Orchestration Agent.
- Control the local Windows firewall. Enable just-in-time RDP access, or exposure of other ports/services on the LAN.
- Control third-party firewalls, like a Fortinet, Palo/Sonicwall/Cisco/Sophos, an AWS EC2 SG or an Azure asset.
Controlling the Windows firewall using Knocknoc creates internal micro-segmentation opportunities for just-in-time network allowlisting, without your Windows Servers exposing inbound WinRM to centralized controlling systems.
Configuration options
After installation, the Windows agent configuration lives at:
`C:\Program Files (x86)\Knocknoc-Agent\knocknoc-agent.conf`Host = 'your-knocknoc-server.example.org'
Token = '<your-agent-token>'
Insecure = true
WindowsLogLocation = 'C:\Program Files (x86)\Knocknoc-Agent\logs'
WindowsRulePrefix = 'kn_'
LogLevel = "trace"Key settings
- Host
The hostname of your Knocknoc instance (cloud or self‑hosted). Append :port if you're not using 443. - Token
The agent token copied from the admin portal when registering the Windows host.
If rotated in the portal, update it here and restart the Knocknoc Agent service. - Insecure
Whentrue, the agent skips strict TLS validation (for example when using self‑signed certificates in a lab).
For production, set this tofalseand use a valid certificate wherever possible. - WindowsLogLocation
Folder where the agent writes its logs, default:C:\Program Files (x86)\Knocknoc-Agent\logs
Check this directory first when troubleshooting agent or firewall behaviour. You can update this to any location on the machine that you like, possibly one that is friendlier for your log collection jobs.
The logs in this directory will rotate automatically daily, or if they reach 500 mb.
The rotated files will have format <logfilename>-2006-01-02-15-04-05-<reason>.log
The rotated files will be retained for 60 days. - WindowsRulePrefix
The windows agent will read the rules from the firewall and provide them to the server for the admin to choose from. By default it will get all rules for ports [3389, 22, 80, 443, 21] with protocol TCP.
The agent will also pass any rules that have the prefix as defined in the config file, enabling your own rules to surface for use automatically. This also makes it easy to search for and distinguish rules that you have created for Knocknoc, inside the Windows Defender Firewall console. - LogLevel
Controls verbosity of the agent logs (e.g."info","debug","trace").
Use"trace"when debugging; revert to"info"or"warn"in normal operation to reduce noise.
After editing knocknoc-agent.conf, restart the Knocknoc Agent Windows service for changes to take effect.
High-availability / multi-web configuration
The Agent should connect to each web node, to ensure no loss of responsiveness during a partial web/server outage event and to not miss an access grant.
Adjust your Agent configuration to point to both servers, as below:
#Hosts = [
# { Host = "knocknoc1.example.com", Insecure = false },
# { Host = "knocknoc2.example.com:8756", Insecure = false }
# ]
# single web node configuration
#Host = "knocknoc.example.com:8756"
#Insecure = false
# multi-web node configuration
#Hosts = [
# { Host = "knocknoc1.example.com", Insecure = false },
# { Host = "knocknoc2.example.com:8756", Insecure = false }
# ]
I've locked myself out of RDP!
Default deny is a wonderful thing, the best place to be - except when you lock yourself out. Thankfully Knocknoc has a break-glass control if you need. See more here.