VPN and ransomware
Use case: Removing VPN ransomware risk from stolen credentials
A mid-size business relied on Internet-exposed VPN appliances to provide extranet access for staff, contractors, and business partners. Due to legacy constraints, some external users still used single-factor credentials.
After stolen credentials led to a ransomware incident, the security team acted fast—deploying KnocKnoc to protect the VPN edge by orchestrating an existing in-line firewall.
The goal: eliminate Internet exposure of the VPN without changing network architecture or requiring client software—critical for the diverse, distributed user base.
The result: no exposed VPN, no user installation required, no routing changes, and a dramatically reduced attack surface.
A beneficial byproduct of the process was that all VPN user access permissions were reviewed, with many uplifted and migrated to their Entra External list allowing MFA to be enforced.
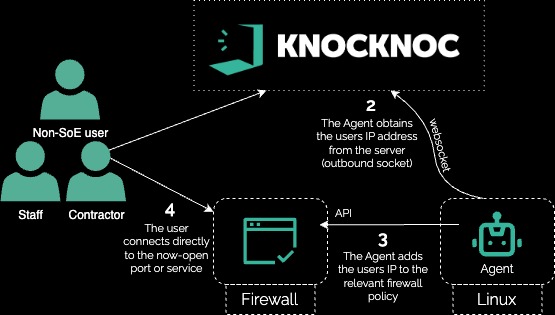
Technical how:
In this example, an existing in-line Firewall appliance was orchestrated to protect the VPN and expose the services just-in-time to authenticated and authorized users.