SAML with OKTA
The following example assumes your Knocknoc instance is located at https://demo.knoc.cloud. Wherever you see that, please substitute it for your own instance URL.
Setting Up the IdP
Create an Application
- Click Create App Integration
- Select SAML 2.0
- Set an App name. (e.g Knocknoc)
- Optional: Upload a logo.
- Click Next.
- Click OK
- Enter the Single sign-on URL (e.g https://demo.knoc.cloud/api/saml/acs)
- Leave Use this for Recipient URL and Destination URL ticked.
- Enter the Audience URL (SP Entity ID URL e.g https://demo.knoc.cloud/api/saml/metadata)
- Leave Default Relay State blank
- Set Name ID Format as Persistent
- Set Application user as Okta Username
- Click Show advanced settings
- Upload your own certificate, one can be created on a Linux machine using the following command.
openssl req -new -x509 -days 3650 -nodes -subj /CN=Knocknoc/ -out user-demo-knoc-cloud.crt -keyout user-demo-knoc-cloud.key - Leave other options default
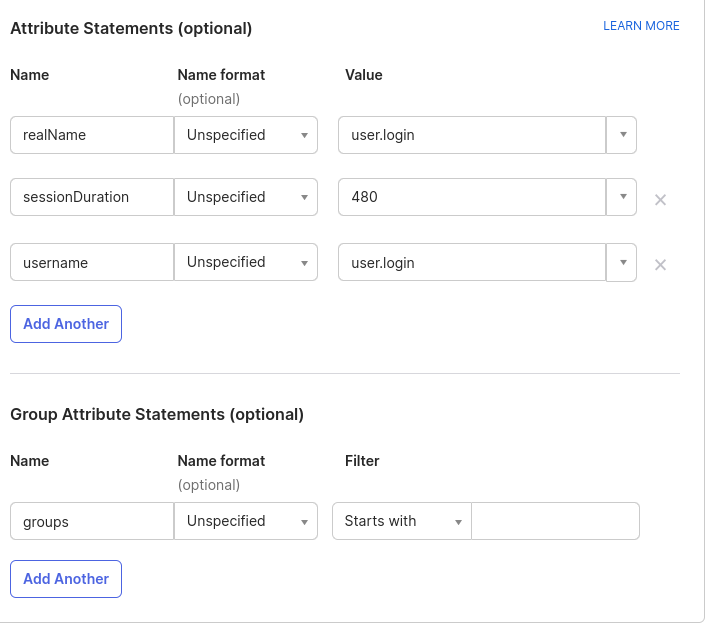
- Add an Attribute statement with the following settings
SAML Signing Certificates
- Delete the original certificate, it is likely SHA1 where the newly generated one is SHA2
- View the IDP metadata and save it as an XML file.
Assignments
- Assign the Application to your users.
- Enable the option to send Groups, to allow the users to be automatically assigned to the correct ACLs.
Knocknoc SAML Config
- Login In the Knocknoc admin interface.
- Click on Settings on the left.
- For the SAMLMetaDataFile, upload the xml file you downloaded from OKTA.
- For the SAMLCertFile, upload the certificate (.crt) file created in the previous section.
- For the SAMLKeyFile, upload the key (.key) file created in the previous section.
- For the SAMLMetadataUrl, paste the Metadata Details, Metadata URL from the Okta control panel.
- Click Save.
Final Testing
Assuming you granted your own user permission to one or more Knocknoc groups in OKTA, you should now be able to login to Knocknoc using SSO.
- Browse to https://demo.knoc.cloud
- There should now be an "SSO Login" button.
- Click this, if you are not already authenticated to your IdP you should now be directed to the IdP login page. Note: If you are already authenticated you'll simply be redirected to an authenticated Knocknoc session.
- If ACLs have already been added you should also see these now say Granted.
If this all works, congratulations! You've successfully run the SAML gauntlet.