Firewall Manager access (IT MSP)
An IT managed services provider maintained multiple Fortinet firewalls on behalf of customers, often responding to urgent service desk requests requiring 24/7 access. These firewalls were deployed across various locations and managed by multiple members of the network team.
Due to security concerns, access to manage these firewalls was restricted to several office/static IP addresses deemed trustworthy. However, remote access remained necessary, including for select customers who self-managed their firewall/rules. To facilitate remote firewall management, a VPN was exposed to the Internet. This approach introduced unnecessary attack surface and another Internet-exposed asset/entry point. It also presented challenges related to authorization as the VPN was shared with MSP staff and select customers.
The goal: Enable remote firewall management from trusted IP addresses on the Internet, linked to an authorized Entra group login, eliminating the need for an Internet-exposed VPN nor requiring on-premise network access.
The result: Firewall management users seamlessly logged in using the Entra external client connector. This solution accommodated both MSP staff and external customers, allowing secure login to the appropriate firewall for management tasks. All access was logged, and multi-factor authentication was implemented without adding complexity or making significant changes to the existing Fortinet configurations.
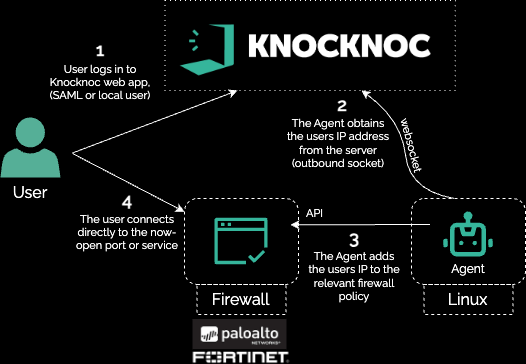
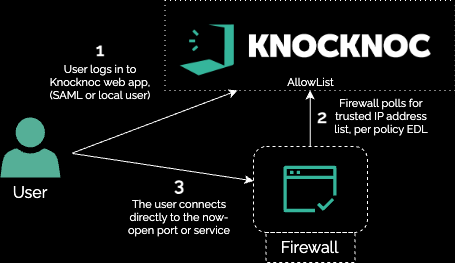
Technical how: In this example half the Fortinet firewalls were 'actively' managed by Knocknoc, with the other half 'passively' orchestrated. This allowed authorized firewall managers to securely manage the firewall devices when required, but presented zero attack surface to the broader Internet, and did not require a VPN whatsoever allowing that device to be deprecated.
Shown below is the Active orchestration model:
The other devices utilized the Passive mode: