FortiOS, FortiProxy, Palo Alto, or SSL VPN
Protect your existing Fortigate or Palo assets from direct internet or internal exposure by introducing Knocknoc.
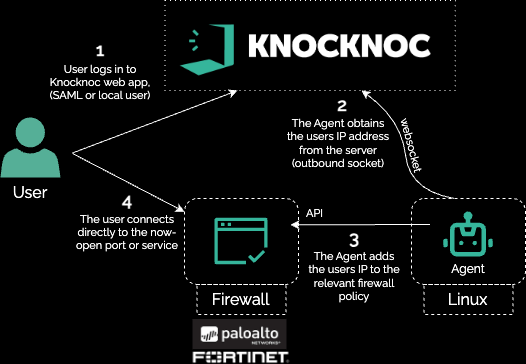
Remote management and administration interfaces, VPN services/ports or any service offered can be protected, requiring a centralised login prior to presenting network exposure. A quick way to support remote management without the Internet exposure risk, removes the threat of zero-days as it is simply invisible prior to logging in to Knocknoc, which opens access just in time.
This can be achieved in multiple ways through active or passive firewall orchestration , effectively adding network application whitelisting only after a successful authorized user login to the network edge.
Shown below is the direct-orchestration model, where Knocknoc adds the trusted/authenticated IP address to the relevant policy on the Fortinet, exposing the VPN services to an IP address only after they have successfully authenticated.
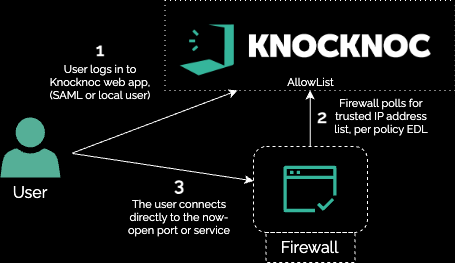
Alternatively an agentless deployment can be established using the AllowList feature:
This can be combined in a passive-allowlist model along with an API call which updates the policies (causing a live poll), giving you the best of both worlds - low privilege API access along with a polled allowlist. We call this Passive+
This can be used to remove the attack surface of VPN services/protocols prior to centralized login or prevent asset exposure to zero-day attacks as they simply inaccessible.
If you need to urgently reduce direct exposure of your Fortigate, Palo or other appliances, please talk to us.
Passive, Active or a combination
Passive - Knocknoc's Allowlist features provides a passive integration with firewalls that support a External Dynamic Lists or EDLs. This feature allows the firewall to pull from the Knocknoc server a list of IPs of authenticated users, in the correct group/for the assigned firewall policy. The drawback of this feature is that the list can only be fetched every 5 minutes.
Active - Knocknoc's Palo Alto orchestration capability utilises the Palo API to actively manage the device, inserting and removing IP addresses as part of the Knocknoc Grant process. This is an active, near-real-time approach that provides the best user experience. Older versions of Palo Alto devices can take time to "commit" the changes to the device which is a Palo constraint. If commit speeds are a problem, using the Passive+ approach can offer better speeds for older devices.
Passive+ (Passive with an Active sync) - the Passive EDL can be utilised in conjunction with an Active API hit to trigger a live refresh from the EDL. This shortens the time taken for polling, and can outperform Active rule management due to the Commit process of the Palo framework.