Allowlist (EDLs)
The Allowlist backend makes a list of active IP address grants available via the Knocknoc server API. This allows integration with appliances or clients that can be configured to poll a URL without the need for a Knocknoc agent to be deployed. This is sometimes known as "External Dynamic List" feature within firewalls.
Devices supporting EDLs (+ many others)
- Palo Alto External Dynamic Lists (EDL)
- Fortinet External Connectors
- Juniper SRX, SonicWall DEAG
- F5 BigIP devices (IP intelligence)
- Cisco Firepower (Dynamic Attributes Connector)
- PfSense, many others
- Custom web applications, scripts, git-foo implementations, etc
When to use an EDL?
EDLs are an easy way to passively integrate Knocknoc, however have some drawbacks.
On one hand they are an efficient way to add thousands of IP addresses to a consuming firewall device, on the other, the polling period can be minutes resulting in a poor user experience. This can be improved by utilizing the "passive+" mode within Knocknoc, which Palo Alto supports - read more here.
Pros
- Any device that can poll for a list of IP addresses can integrate with Knocknoc - a good solution for unidirectional network environments or assets deep in an organisation.
- Does not require a Knocknoc Agent to be installed whatsoever.
- Many thousands of IP addresses can be managed with little impact on the orchestrated firewall.
Cons
- Polling is typically time-based not event based, this may see a user waiting for access after logging in - depending on the poll interval supported by the infrastructure or appliance.
- Slow user login experience, given the above.
- Doesn't benefit from "User ID" and other active capabilities the firewall may offer.
See below on how these can be incorporated in to major vendors via external lists:
- Fortigate (Fortinet): Fortinet Knocknoc how-to or the Vendor documentation
- PAN OS (Palo Alto): Palo Knocknoc how-to or the Vendor 1, Vendor 2.
- PfSense: Vendor docs
- Sonicwall: Vendor docs
- Checkpoint: Vendor docs
Other platforms are supported, however talk to us about our native/API integrations as these offer many benefits over the time-based polling approach.
Improving the EDL user-experience with "Passive+" mode
Knocknoc supports two modes of EDLs, Passive and Passive+.
Passive publishes the EDL for consumption, with the timing of consumption entirely up to the firewalls scheduled polling frequency.
Passive+ publishes the EDL, but also interactively hits an API on the firewall device requesting the EDL be refreshed. This shortens the time between publishing and consumption, resulting in a faster user/grant experience whilst still benefiting from the EDL approach.
Overall process
- Configure the Knocknoc Server: Set up a Passive Knoc.
- EDL Configuration: Configure the device to point the EDL to the Knocknoc distribution server.
- Security Policy Rule: Create a policy referencing the dynamic address and other relevant parameters to suit your intended firewall policy.
Knoc configuration
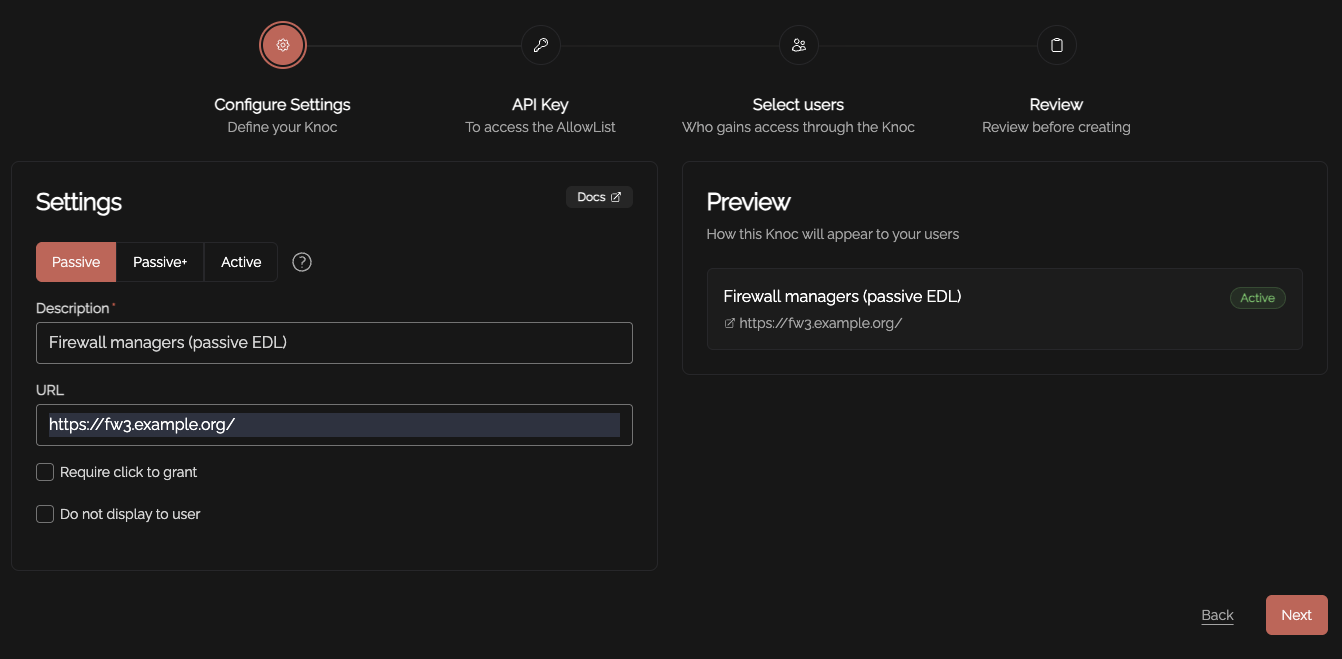
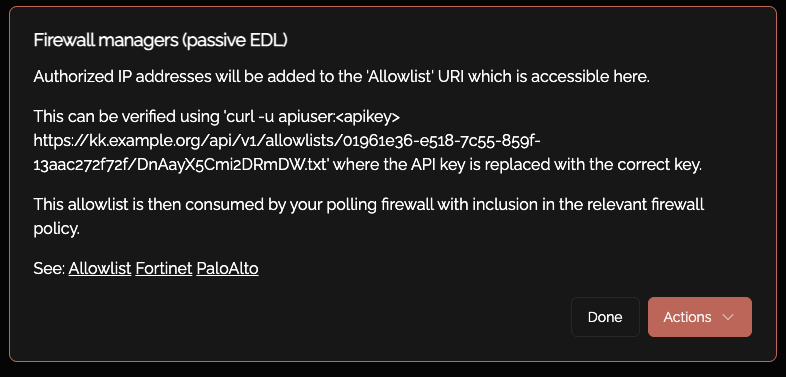
Create a Knoc under Firewalls/Appliances. Select Passive. Note that no Agent is required for this configuration as the Server is publishing/hosting the Allowlist.
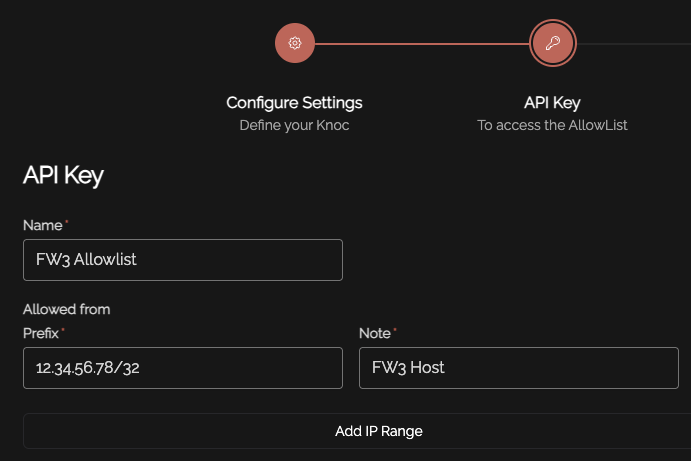
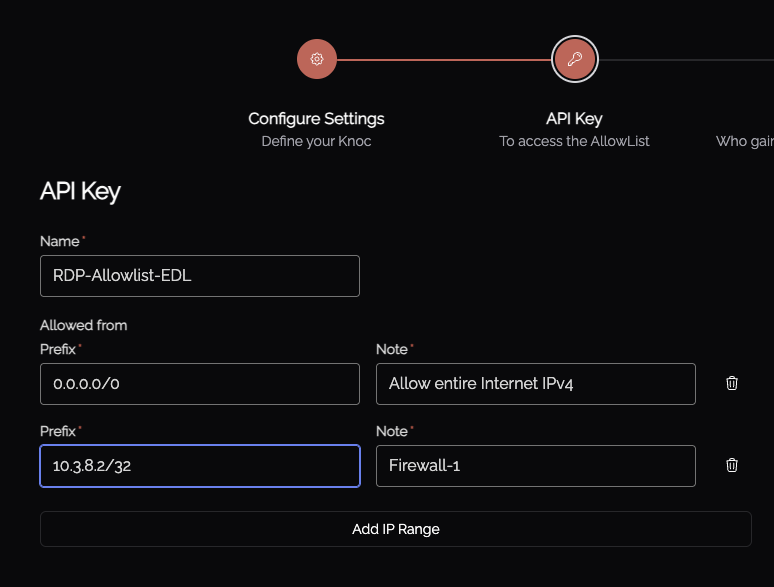
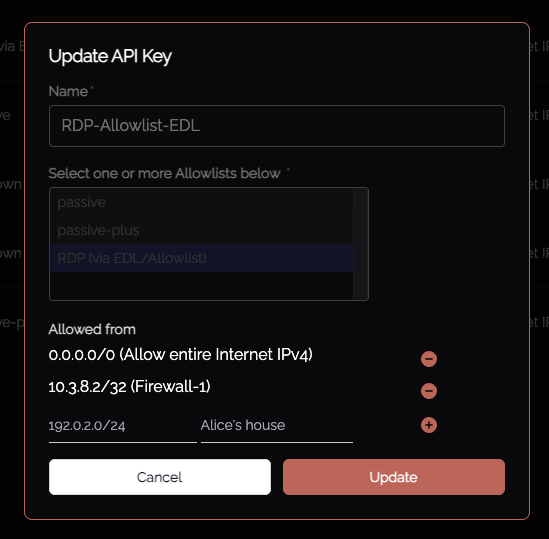
Set an API key name, and define any IP allowlisting restrictions on the API key-use. Naturally we recommend removing the "entire Internet" rules.
Be mindful of the IP address restrictions, by default it will allow the entire v4/v6 Internet.
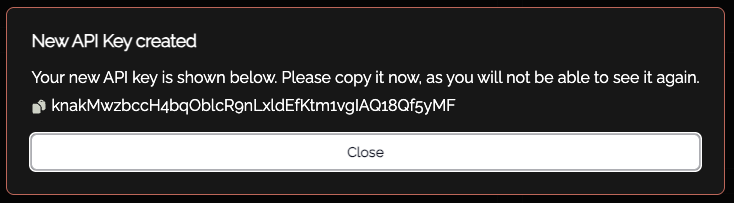
Copy the API key/token that is displayed, you will not be able to recover this after it has been shown.
Copy the API key and store this for future use.
You now need the unique and random URI published per-Knoc, to be added to the consuming firewall/system.
Copy/paste the URL from the relevant Knoc.
You can also see the URI for this Passive Allowlist/EDL by clicking on the Knoc:
Testing the EDL
You can test the EDL including authentication using Curl as below:
curl https://demo.knocknoc.io/api/v1/allowlists/XXX -u apikey:secrettoken
Note that some vendors/platforms built-in testing functionality does not utilise the authentication information if provided (including Palo Alto), so you will always get an error. It is recommended you use the curl command above or other testing tool such as Postman that supports authentication.
User experience and EDLs
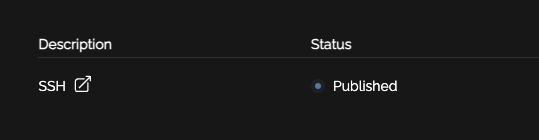
When your user logs in they will see "Published" alongside the relevant access item. This means their IP address or access information has been "published" and is awaiting consumption by the relevant firewall/system.
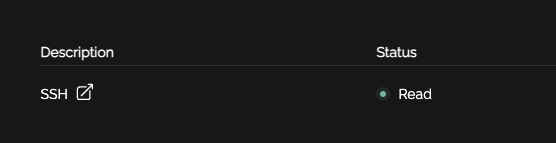
One the firewall/system polls or "reads" the EDL, the state will change from Published to Read, signalling to the user their access has been established on the relefvant back-end environment.
Allowlist / EDL Security
EDLs are published for consumption on the Knocknoc server.
To access the EDL contents you must:
- Know the EDL UUID and randomly-generated path/location, and
- Provide a valid API key within the authentication header that matches the particular EDL, and
- Be in the IP source-address allowlist, configured for that EDL/API Key within Knocknoc.
Note that IP restrictions are managed within the related API key. This is defined on Knoc creation, but can also be adjusted via the API Keys section: