LDAP troubleshooting tips
The Knocknoc server will need to be able to contact your LDAP server on port 389 or 636. This is determined by the LDAP URL in the Settings:
ldap://myldap.domain.com - this format says port 389
ldaps://myldap.domain.com - this format is port 636
Please make sure the firewall and routing allow your Knocknoc server to connect to LDAP on these ports.
The ideal security model for LDAP (if you must use it) is really port 389 with StartTLS enabled, which is a tickbox you should select. StartTLS is a little more resistant to man-in-the-middle attacks, however it all depends on your risk profile.
StartTLS with certificate verification is preferred, if you have an internal CA, or no DNS or for whatever reason, you can skip TLS verification with StartTLS as well. This is less ideal, but still better than no TLS.
LDAPS can have even more complications with CAs and certs being required. Knocknoc support are happy to assist should you require some assistance.
Active Directory
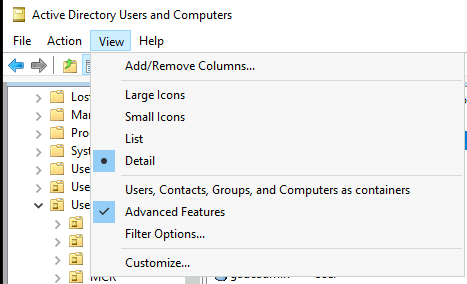
If you want to find your Active Directory CN, so you can configure a user with it, there are many ways to do so, but a quick way is to simply enable Advanced Features in the Active Directory Users and Computers snap-in, and then there will be an Attribute Editor tab for each user.
Then right click the user, Choose Attribute Editor, and scroll down to Distinguished Name. Copy that value into the Knocknoc User LDAP properties.
Knocknoc attempts to bind to LDAP as the user, with the password supplied. Hence, no dedicated bind user is required.