Palo Alto
Passive+, Passive or Active?
Knocknoc orchestrates Palo Alto and Panorama devices in a number of ways; actively, passively or a combination known as passive+. This allows Administrators to configure the appropriate level of trust, network access and orchestration design permissions depending on the environment. A high-volume Internet facing environment may suit Passive+ mode best, with an air-gap network benefitting from the one-way nature of Passive mode, with another more suited to Active orchestration. These are all options that can be deployed to suit your needs, including a combination being utilized on the same device(s) at once.
Passive+ (Passive EDL retrieval, with an active refresh) - Knocknoc's offers a passive integration for firewalls that support an External Dynamic Lists (EDL) or external IP/host address list. This feature allows your firewalls to pull the list of authenticated users IP addresses which can then be used as the source (or destination) of a pre-existing firewall policy. However, as firewalls typically poll every 5 minutes, this can leave users waiting for access. With Passive+ mode, the EDL is used in conjunction with an "active" trigger, which refreshes the EDL so it is typically within a second to log in, even when a Panorama is involved. In addition, the Palo Alto "User-ID" for each users session can be optionally added to the Palo/Pano environment by selecting this in the Knocknoc configuration.
Passive - The firewalls poll the Knocknoc server and consume the trusted IP address list, mapping these to an EDL. The drawback of this feature is that the list can only be fetched every 5 minutes within the Panorama/Palo Alto environment. The benefits are no agent or API access is required. The User-ID information requires the API and it's not possible to use this via a passive EDL.
Active - Knocknoc's Palo Alto orchestration capability utilises the Palo API to actively manage the device, inserting and removing IP addresses as part of the Knocknoc Grant process. This is an active, near-real-time approach that provides a good user experience. Older versions of Palo Alto devices can take time to "commit" the changes to the device which is a Palo constraint. If commit speeds are a problem, using the Passive+ approach can offer better speeds for older devices or for large groups of users logging in at similar times.
Palo firewall and/or Panorama
If you're using Panorama, Passive+ is a good option as API access is needed to the Panorama but not the underlying firewalls, making deployment easier. A combination of Passive+ and Active can also be used for finite access, which is suitable in a geographically distributed environment. This can also be split to send instructions to a "local" firewall(s) but update the Panorama with User-ID information for central oversight or in the case of long-distance latency/network-reliability concerns.
Prefer video?
End to end walk through of Panorama and Palo Alto integration.
Option 1 - Passive+ mode
In Passive+ mode, Palo Alto firewalls poll Knocknoc via a secure path and download a list of IP addresses added after users authentication. This list populate an "external dynamic list" (EDL), which is then used within a pre-configured firewall policy. Additionally, because this polling occurs every 5 minutes, Knocknoc (via an orchestration agent) triggers this refresh dynamically based on a user login, so the 5 minute polling window is reduced to 0-2 seconds, from a user logging in to the firewall having the IP address information, including when managed via a Panorama.
To achieve this, the Passive+ configuration within Knocknoc creates an "EDL" and configures a "refresh the EDL" active call for a Knocknoc Agent.
The Palo Alto firewall "reads" the EDL from the Knocknoc Server (connection is from each individual firewall, even when using a Panorama) - with an active "refresh the EDL" API call being made from an orchestration Agent - to the Palo Alto device to optimize the rule refresh period. This ensures a fast response time for users logging in, but still supports hundreds/thousands of simultaneous user logins without pressure on any Palo/Pano device in the access provisioning chain.
- Configure the Knocknoc Server: Set up a Passive+ Knoc, noting some configuration data is required from the Palo Alto environment.
- EDL Configuration: Configure the Palo/Pano; 1. Configure the EDL 2. Allow limited API access to refresh the EDL via a least-privilege api-user-role and api-user.
- Security Policy Rule: Create a firewall policy in the Palo/Pano referencing the dynamic address/group being managed by Knocknoc.
- Log in/out: Confirm EDL consumption!
Knoc configuration
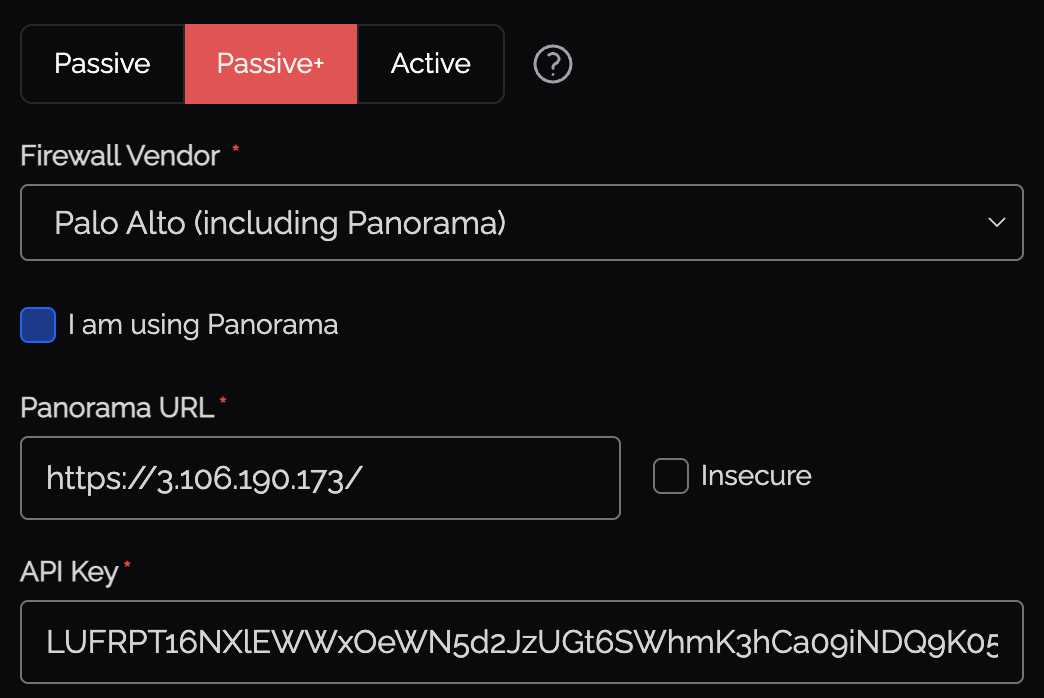
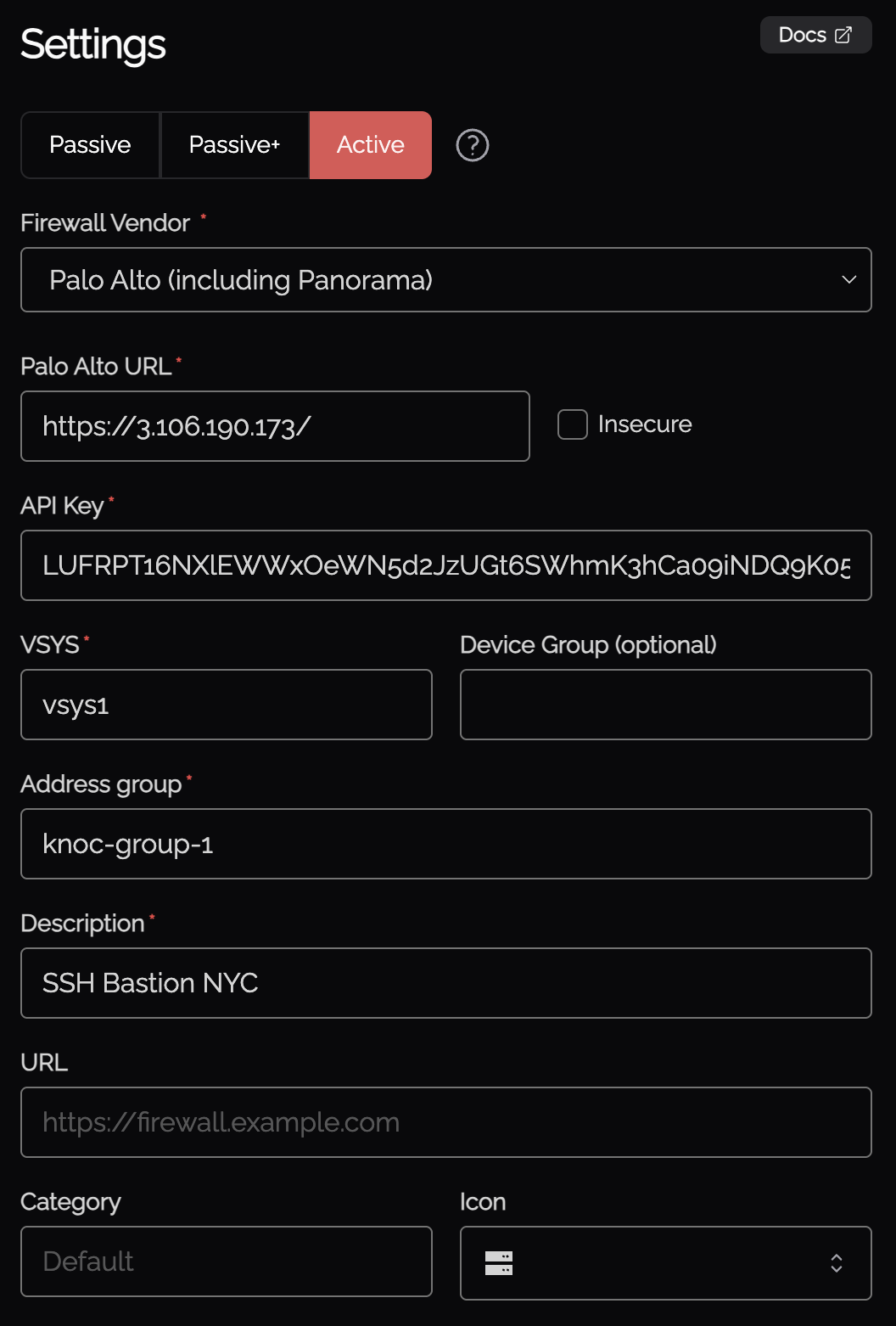
Select the "Firewalls / Appliances" Knoc configuration, selecting "Passive+"
Throughout this document you'll be given everything you need to enter the relevant information, there will be hyperlinks below for where you can find it. Some options include:
- If you are using a Panorama - select this option.
- Provide the URL to the Palo Alto/Panorama device
- Select "Insecure" if the TLS/SSL certificate is not signed by a trusted CA
- Provide the API key - this is obtained after creating the user role and user in the Palo device. See below.
- Provide the "EDL" name configured in the Palo device.
- If you're using a Virtual System (VSYS), you will need to provide this.
- To utilise the User ID mapping functionality within Palo Alto, select the "Map user to address" option. If you want to send the User-ID information to a different device (if orchestrating a local firewall, but sending User-ID to a separate Panorama, for example), select "Use an alternative".
- The API Key is required to refresh the EDL (and optionally update the User ID mapping), see below for obtaining this.
- We also recommend setting up an API role and dedicated account, to reduce permissions and operate in least-privilege, and to avoid a password/user change breaking your integration. This can be followed below.
- We also recommend setting up an API role and dedicated account, to reduce permissions and operate in least-privilege, and to avoid a password/user change breaking your integration. This can be followed below.
Palo Alto API key creation
The Palo Alto API key is required to trigger a poll-refresh (in Passive+ EDL mode), or to manage addresses and address groups if you're using Active mode. If you do not want your orchestration agent to talk to your firewall or Panorama, you can use Passive mode.
Firstly a least-privilege "role" is created, along with a "user" which is then linked to the new role. This is recommended over using an Admin user or role, reducing harm should the key be compromised. An Admin account is not required.
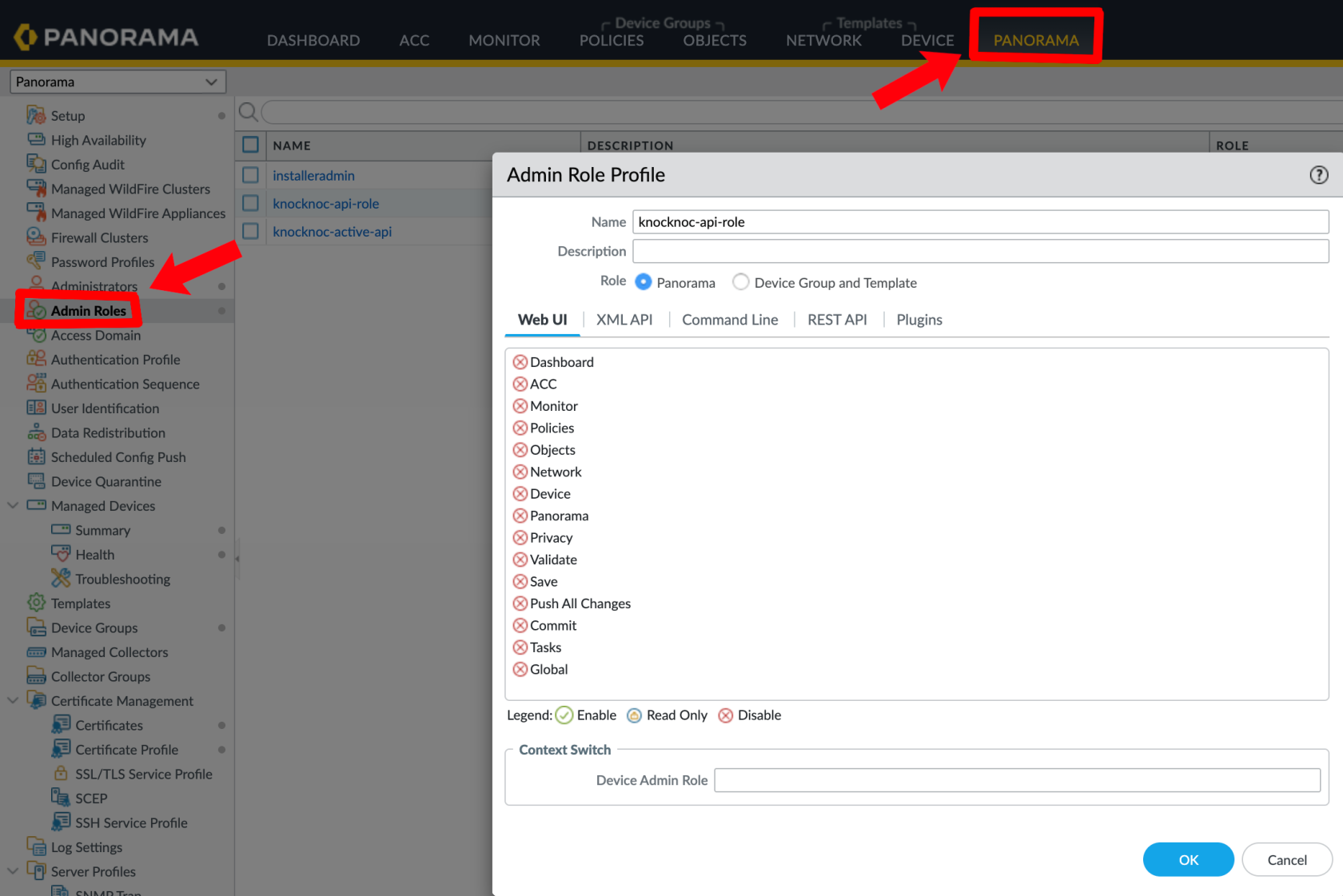
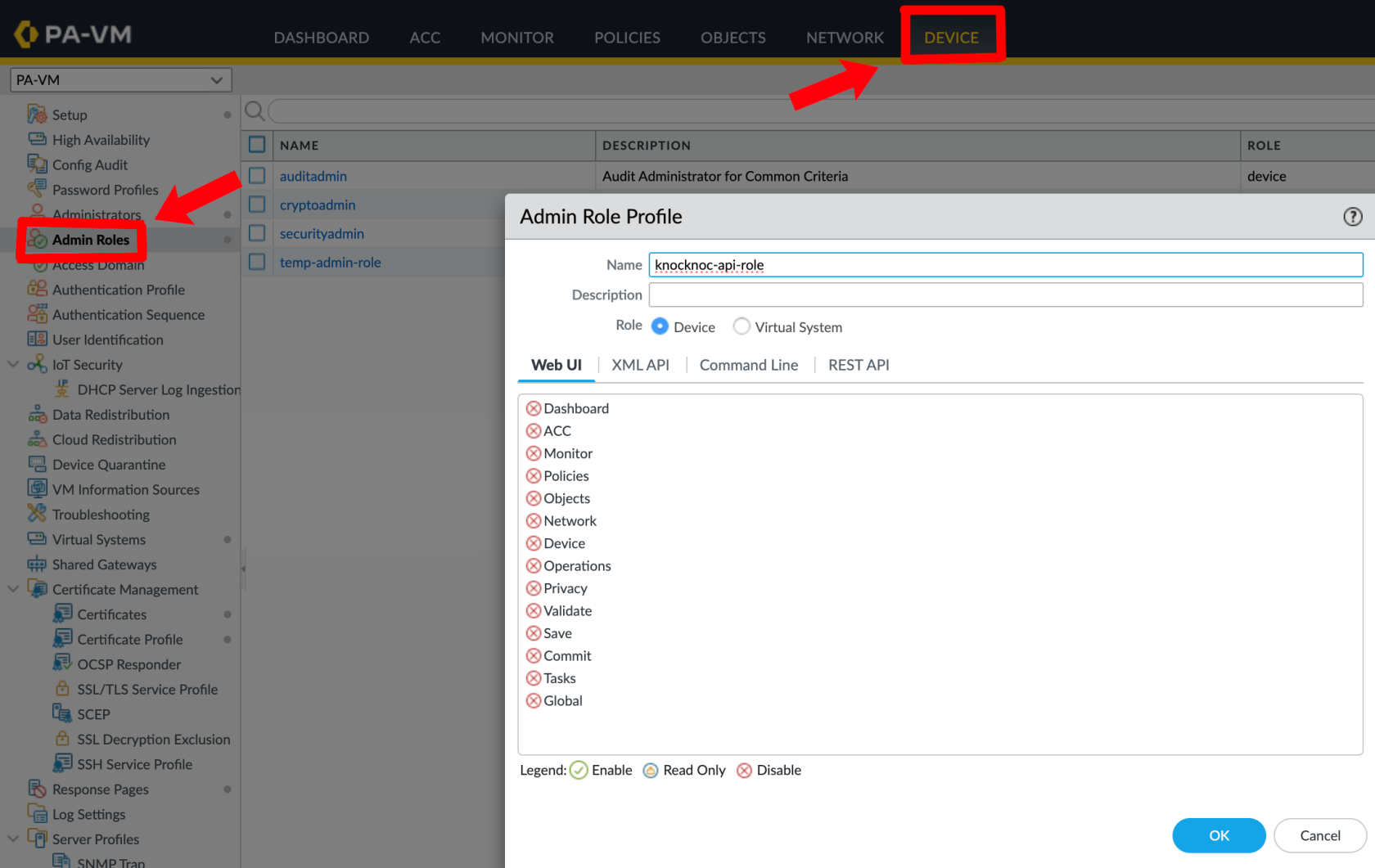
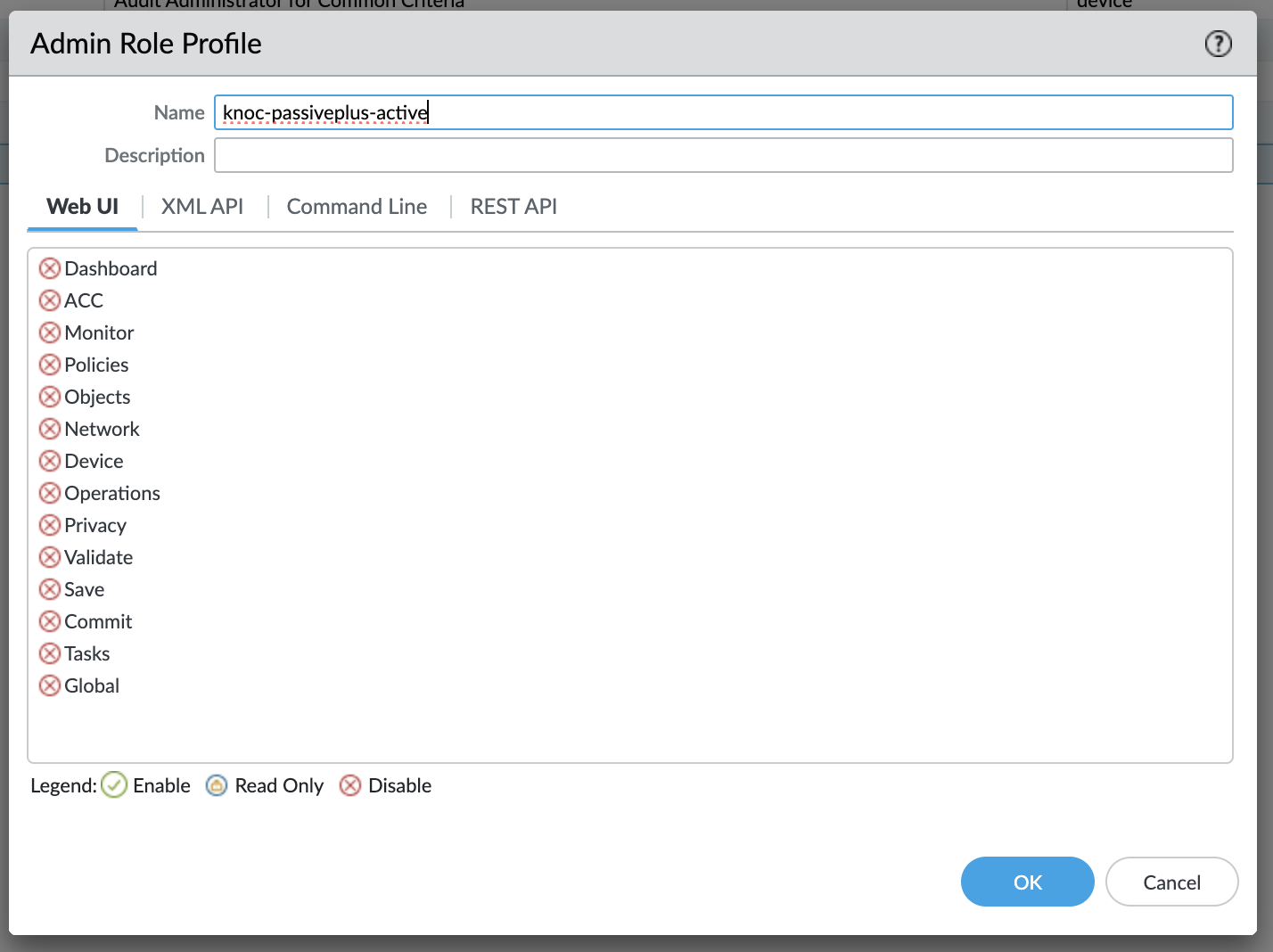
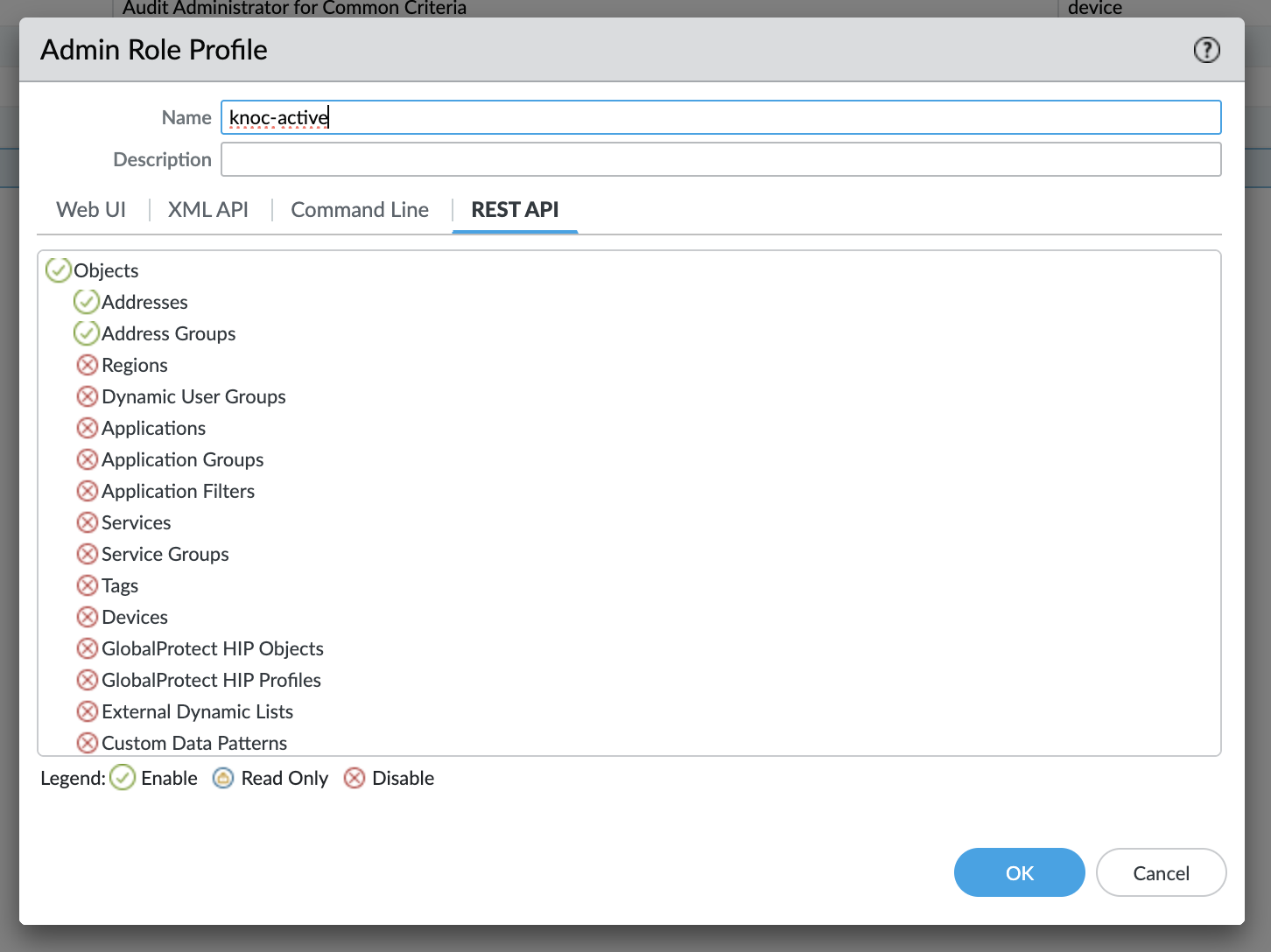
On the Palo Alto or Panorama device, use the Admin Role -> Profile, create a new profile and grant these permissions only.
These are the permissions required (only):
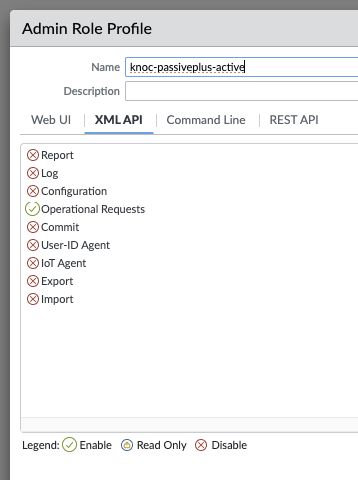
- XML API: Operational Requests
- REST API: External Dynamic Lists
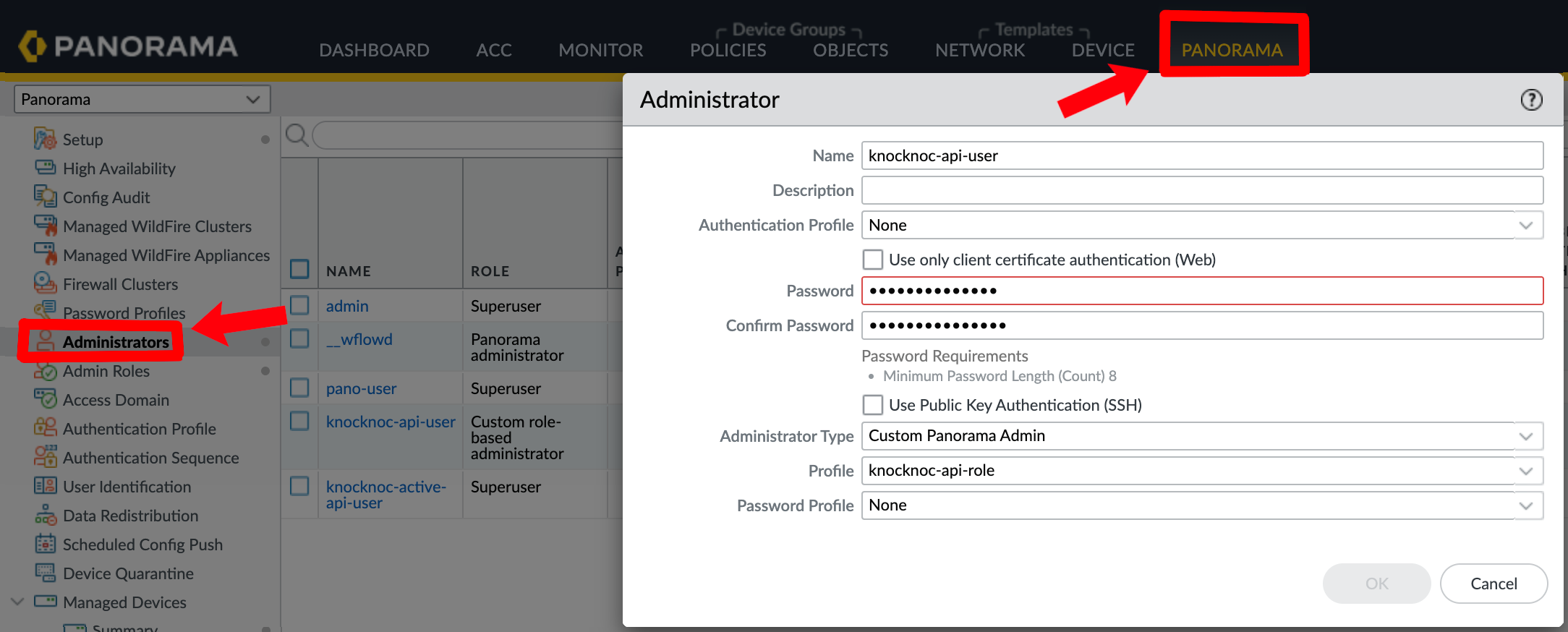
Now you have your role, create your user by going to Palo / Pano Administrators,
Panorama - Panorama --> Administrators --> Add
OR
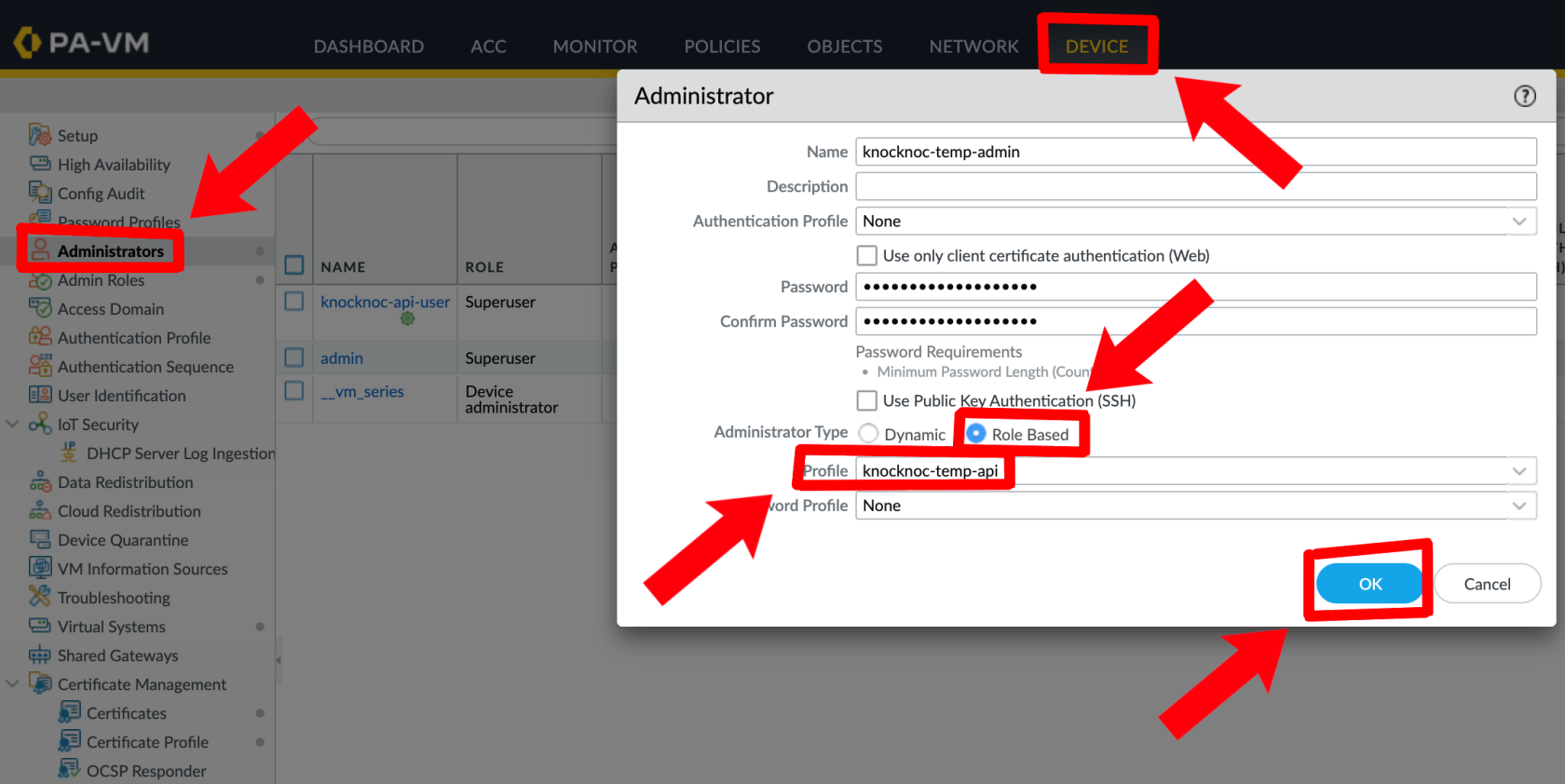
Palo Alto - Device --> Administrators --> Add
Now you have created the role, linked the user, and set a password, you need to interact with the Palo API to generate the API key. The orchestration agent has a utility for performing this action.
Log in to your orchestration agent host, execute knocker enable panos:
/opt/knocknoc-agent/knocker/knocker enable panos
Follow the prompts, as below:
$ /opt/knocknoc-agent/knocker/knocker enable panos
Enabling backend panos on this machine.
Note: Some operations may require sudo rights.
PAN-OS Integration Setup
Please provide the following information:
PAN-OS Hostname or IP: 13.236.94.186
Enter Username: knocknoc-api
Enter Password:
Generating API key for user 'knocknoc-api' on host '13.236.94.186'...
Successfully retrieved API key.
API Key: LUFRPT0vR...BlVHc9PQ==
Please save this key securely. It will not be saved in the config.
You can use this key to authenticate API requests.Once you have this base64 blob/API key, save it somewhere safe.
Be sure to copy any terminating equals (==) signs.
Alternatively the official Palo documentation suggests using Curl: curl -H "Content-Type: application/x-www-form-urlencoded" -X POST "https://firewall/api/?type=keygen" -d 'user=<user>&password=<password>'
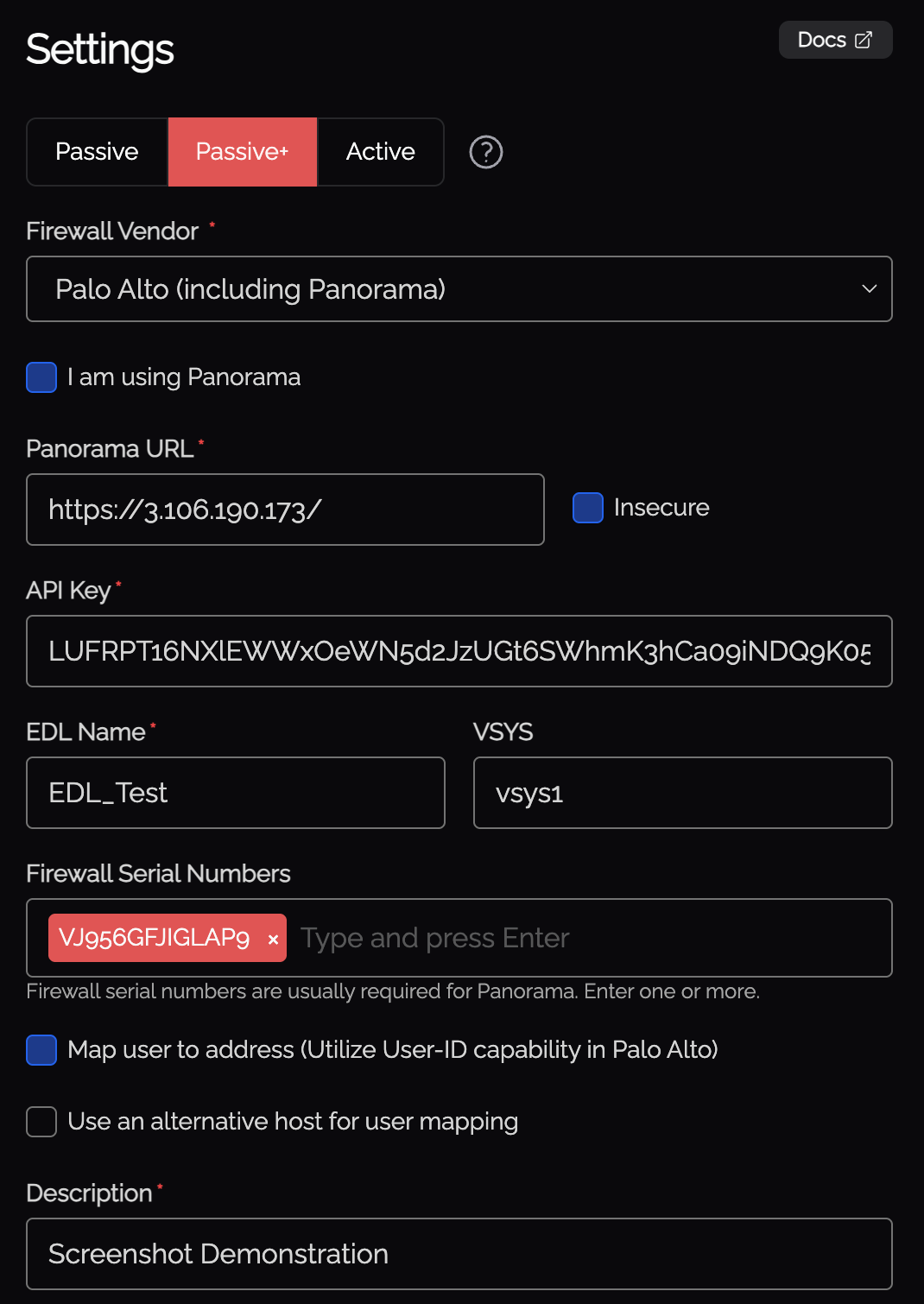
Place the API key in Knoc, you should have something similar to the screenshot below
Complete the remaining data as required, and click Next.
EDL Access Key
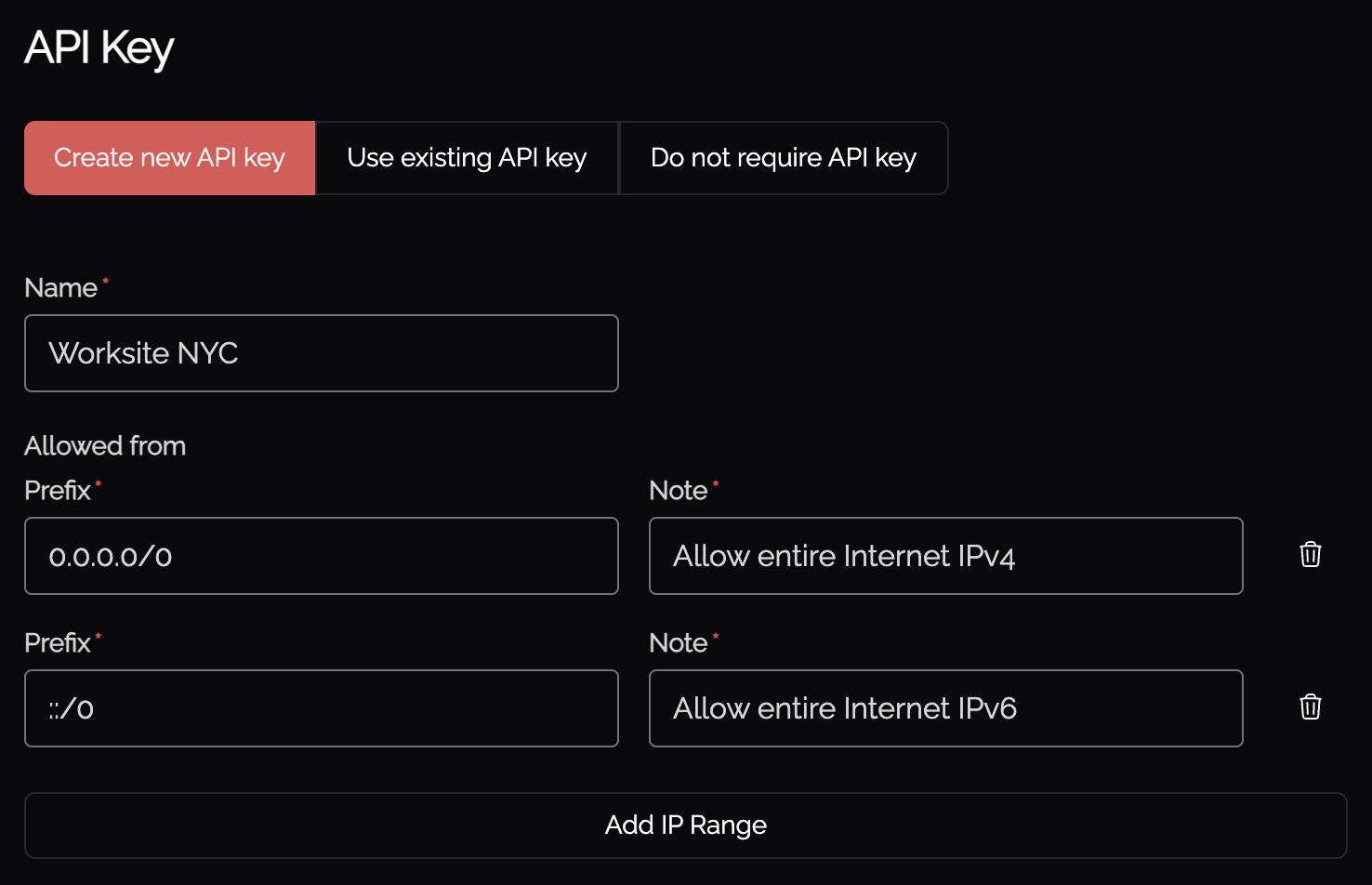
Your Knocknoc Server publishes the EDL for collection, which requires an incoming API key or username/password to be provided by the Palo Alto firewall device (even when using a Panorama), to ensure the confidentiality of the IP address lists.
This is an API Key within the Knoc creation flow as outlined below.
Noting this key becomes the users password, in the case of Palo Alto. You can opt for no password, or to re-use an existing key, along with restricting by IP address source, who can present and use the key for access.
- Define an API key name - this can be re-used across EDLs.
- Set any IP allowlisting restrictions - this is the IP of the firewall. Note the firewall will be polling/retrieving the EDL, even with a Panorama in place. Naturally we recommend removing the "entire Internet" rules and being more specific. These IP restrictions can be edited later through the API keys section.
Be mindful of the IP address restrictions, by default it will allow the entire v4/v6 Internet.
The next steps occur in your Palo Alto devices.
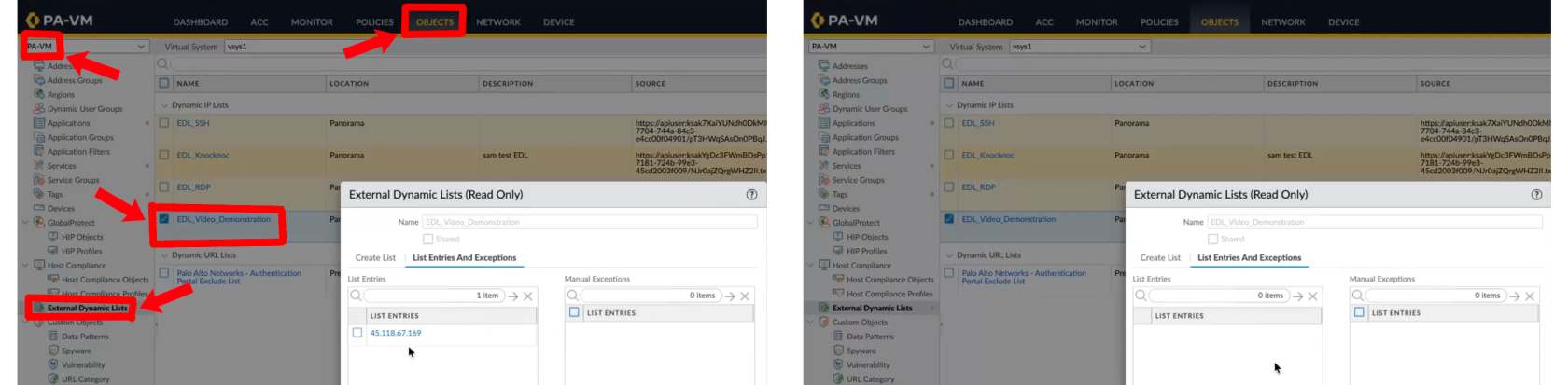
Configuring the External Dynamic List (EDL)
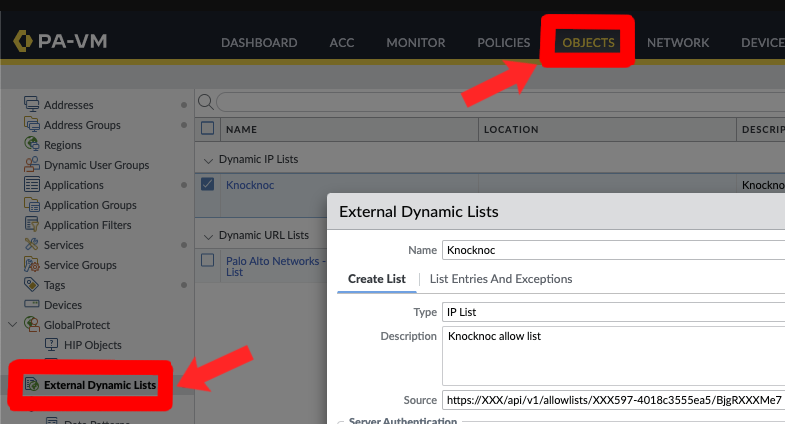
- Log in to the Palo Alto or Panorama
- Under Objects, External Dynamic Lists, click Add+ for a new list.
- Create a name for the list, noting this is per Knoc - allowing a per-policy list, for example "FirewallManagers" and "SSH" may be two Knoc's that map to different firewall policies.
We will fill in the source later - leave this tab open as we finish the API integration first which will give us the 'Source'.
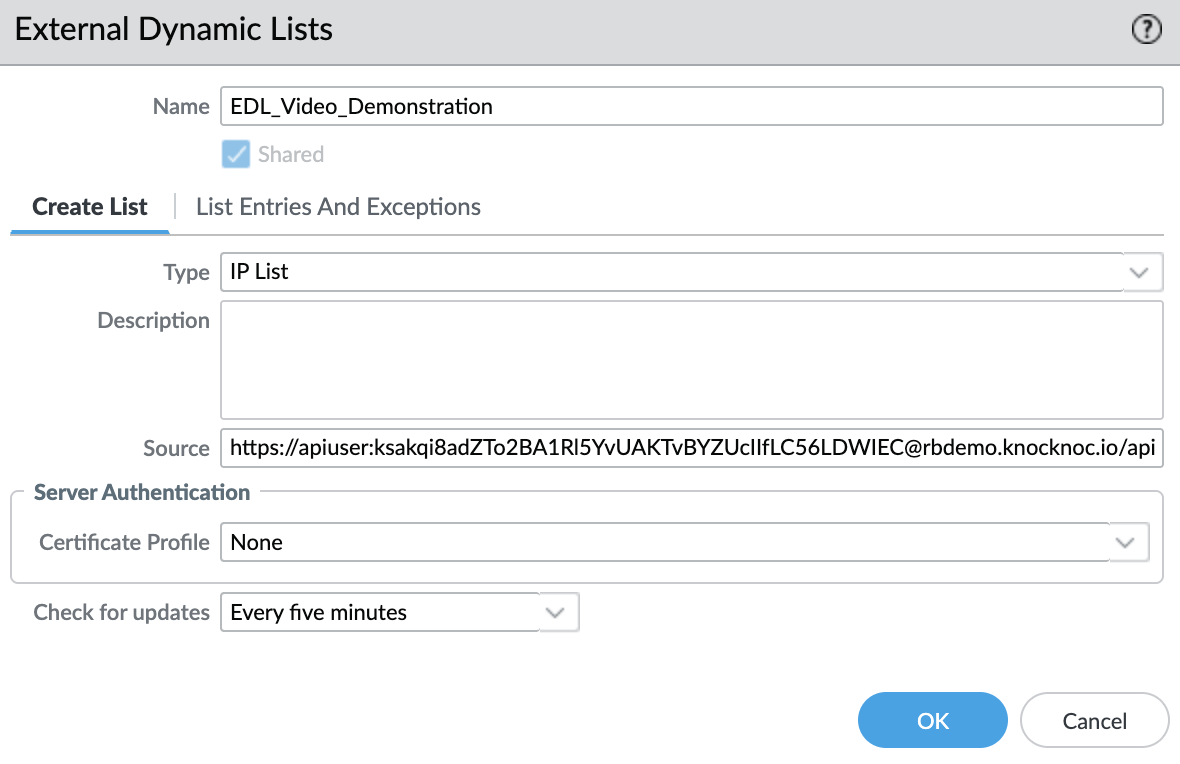
EDL Access URL
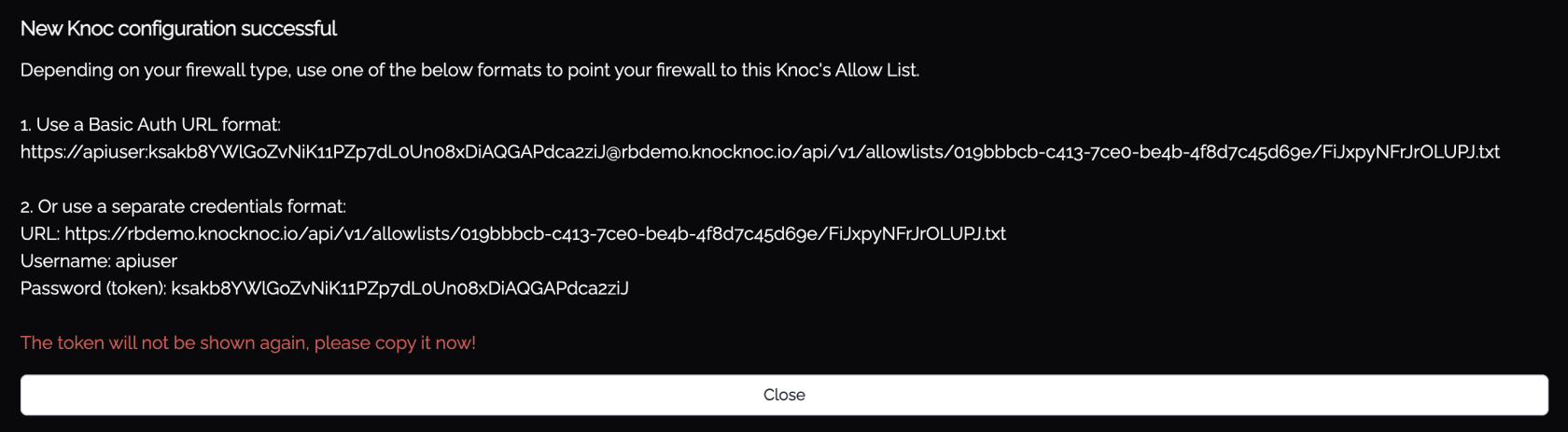
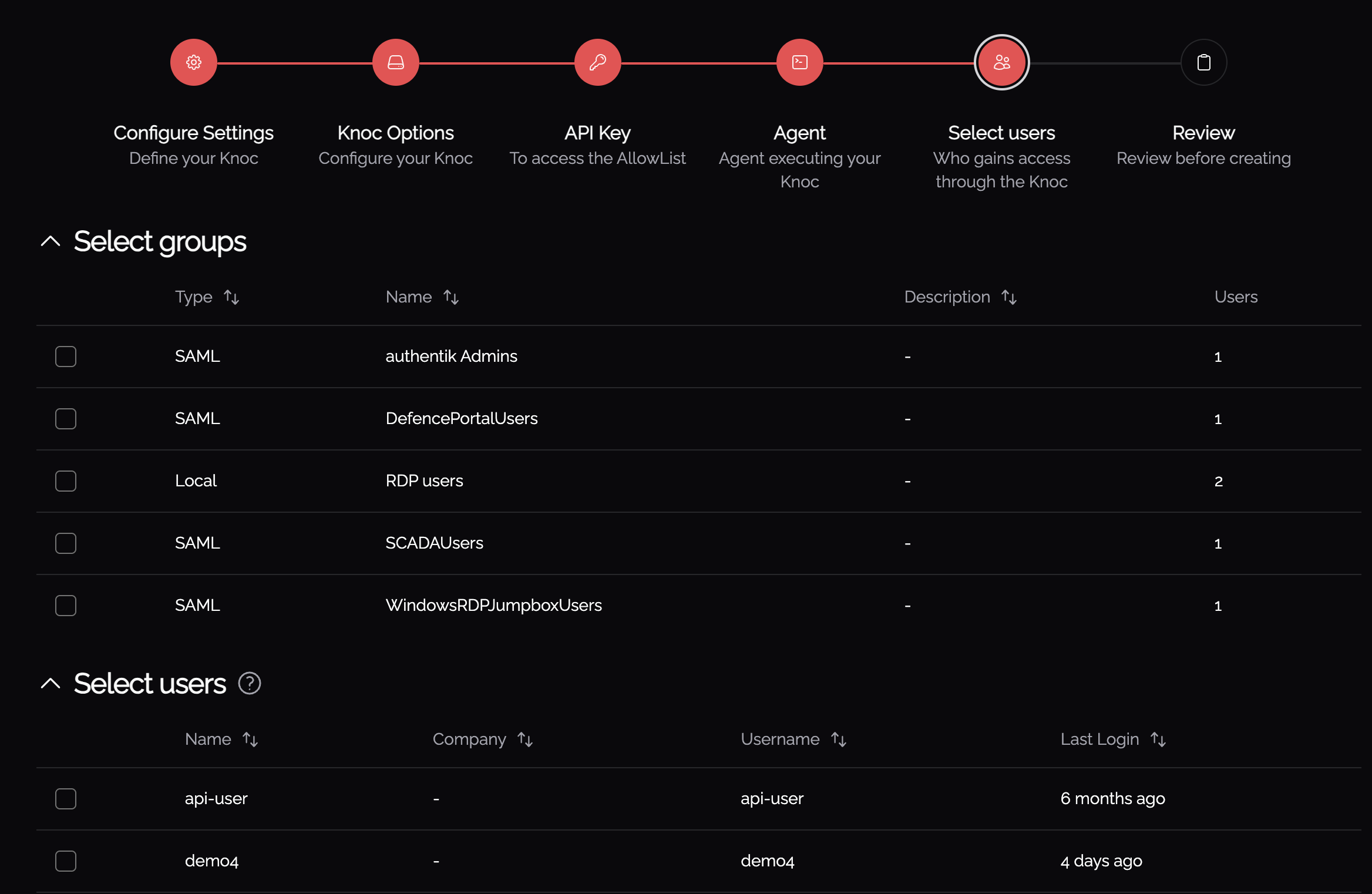
Back in Knocknoc, assign the relevant users/groups to the Knoc, and submit the final configuration.
You will now be presented with data similar to the below:
You have two options with Palo Alto, either using the "1. Use a Basic Auth URL format" option or "2 Use separate credentials".
The option-1 basic auth url is simpler and does not require a ca-profile to be configured, this is the most convenient.
The Basic Auth URL can be copied from the above and pasted into the 'Source' for the EDL, within Palo Alto.
The password/token will not be displayed again from within Knocknoc. Be sure to copy it!
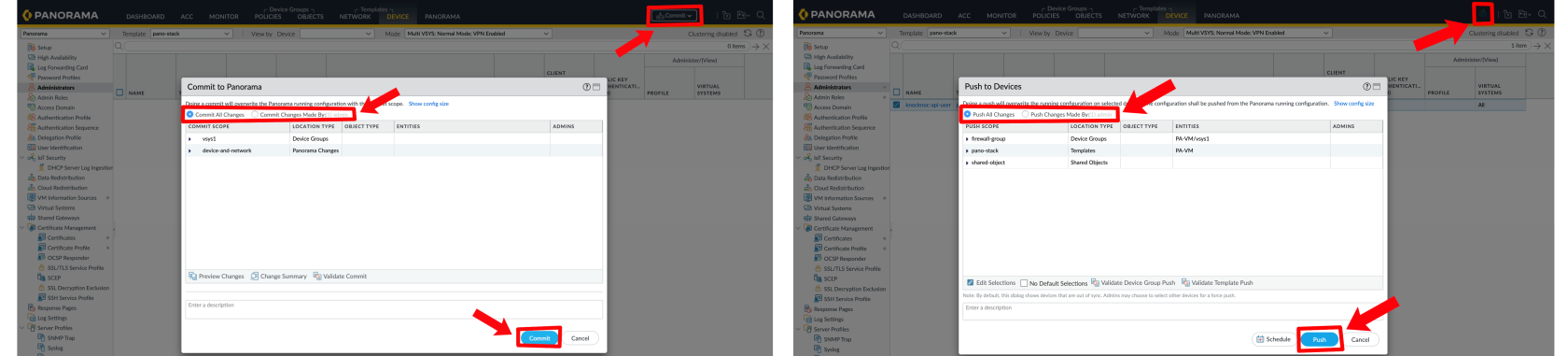
Save and Commit this to your Palo Alto environment.
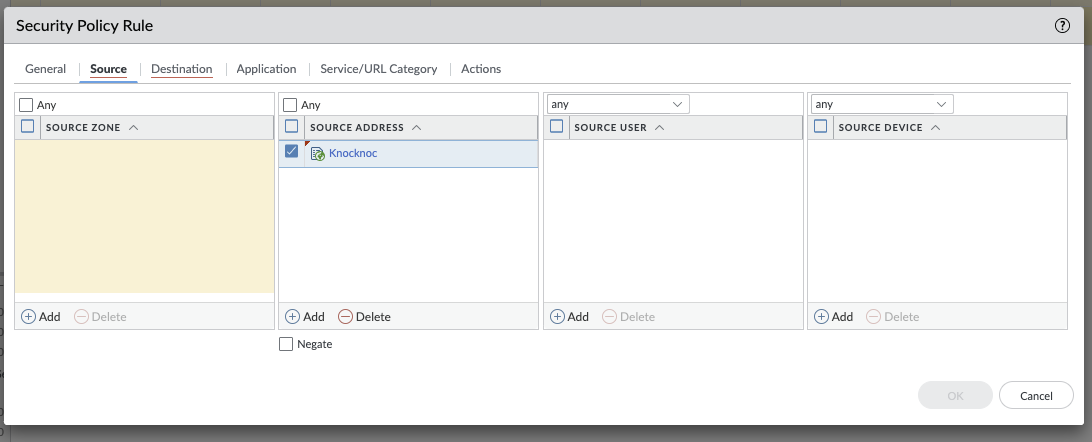
Using the Dynamic Address in Firewall Rules
The EDL can be selected within the Source Address section. This is effectively a dynamically updated list of authenticated and authorised users IP addresses. You can inspect the EDL contents in a number of ways. Remember to set your Source Zone and Destination Zones.
You're now good to go! To test as a user, ensure you assign them and or their group to the knoc as seen below.
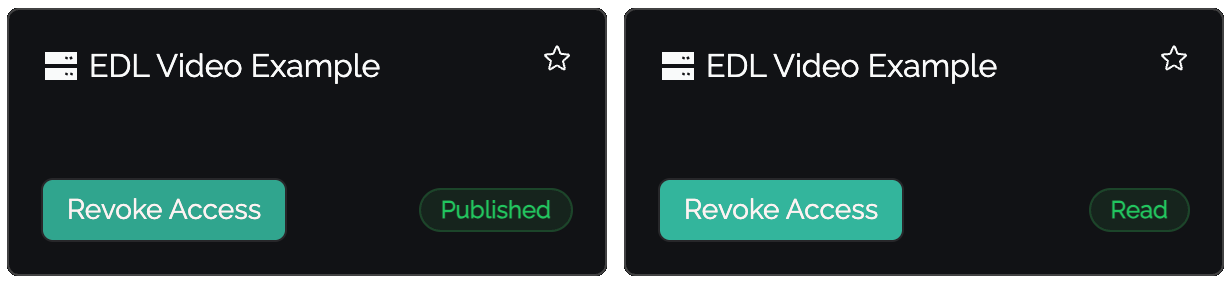
To test as a user, make sure to visit their access page. When a user is requesting access they'll see 'Published', meaning the request has been sent, and 'Read' when it has been processed and accepted and can now access the application.
Importantly to see IP's being added and removed, you have to be in your Palo specifically and not your Pano.
If you are having issues remember to commit with Panorama / Palo Alto, and push to the devices.
Passive+ Checklist
✅ Your Knoc has the correct settings;
- ✅ If you're using Panorama you've ticked that box
- ✅ Your URL matches correctly to what you've entered into the Knoc's settings
- ✅ If you're using an insecure URL, you've ticked 'insecure'
✅ You've added in the correct API Key
- ✅ You've created the custom role with the appropriate permissions
- Minimum perms for the role include:
- XML API: Operational Requests
- REST API: External Dynamic Lists
- Minimum perms for the role include:
- ✅ Matching API admin to the API role
- ✅ You've made the API key with the correct IP, username, and password with the appropriate role added
✅ The EDL Name is correct and has been made WITH the API source added from the end at the creation of the Knoc
✅ The dynamic address in firewall rule has been configured to reference the source EDL
Option 2 - Passive mode
If you prefer to utilize Passive mode, follow the below.
- Configure the Knocknoc Server: Set up a Passive Knoc.
- EDL Configuration: Configure the Palo to point the EDL to the Knocknoc server. You also need to extract the server CA/chain for the Palo to verify the server.
- Security Policy Rule: Create a firewall policy in the Palo referencing the dynamic address/group being managed by Knocknoc.
Knoc configuration
Create a Knoc under Firewalls/Appliances. Select Passive. Note that no Agent is required for this configuration as the Server is publishing/hosting the Allowlist.
Passive Checklist
✅ Your Knoc has the correct settings, having chosen the correct URL of choice
Option 3 - Active (API) mode
Active will update the address group for each users requested access grant, this will update the access list immediately.
- Configure the Knocknoc Server: Set up an Active Knoc, noting some configuration data is required from the Palo Alto environment.
- Security Policy Rule: Create a firewall policy in the Palo referencing the dynamic address/group being managed by Knocknoc.
Knoc configuration
Select the "Firewalls / Appliances" Knoc configuration, selecting "Passive+" or "Active"
Follow the prompts, as below, entering the API key as created above:
Select the Agent you want to execute the Knoc from. We recommend deploying an Agent adjacent to the Palo devices and remove external attack surface on the Palo.
Active API permissions
For Active, the API configuration is the exact same as Passive+, except with these permissions below:
REST API: Addresses, Address Groups
Active Checklist
✅ Your Knoc has the correct settings;
- ✅ If you're using Panorama you've ticked that box
- ✅ Your URL matches correctly to what you've entered into the Knoc's settings
- ✅ If you're using an insecure URL, you've ticked 'insecure'
✅ You've added in the correct API Key
- ✅ You've created the custom role with the appropriate permissions
- Minimum perms for the role include:
- REST API: Addresses, Address Groups
- REST API: Addresses, Address Groups
- Minimum perms for the role include:
- ✅ Matching API admin to the API role
- ✅ You've made the API key with the correct IP, username, and password with the appropriate role added
✅ The EDL Name is correct and has been made WITH the API source added from the end at the creation of the Knoc
✅ The dynamic address in firewall rule has been configured to reference the source EDL
User experience and EDLs
When your user logs in they will see "Published" alongside the relevant access item. This means their IP address or access information has been "published" and is awaiting consumption by the relevant firewall/system.
One the firewall/system polls or "reads" the EDL, the state will change from Published to Read, signalling to the user their access has been established on the relevant back-end environment.
API role/permissions
| Knocknoc/Palo orchestration mode | API access and permissions required |
| Passive | No API access is required |
| Passive+ | XML: Operational Requests |
|
Passive+ with "map user ID" enabled |
XML: Operational Requests, UserID Agent |
| Active | REST API: Addresses, Address Groups |
|
Active with "map user ID" enabled |
XML: User-ID Agent REST API: Addresses, Address Groups |
Troubleshooting
If you're experiencing errors the first step is checking the Agent logs, permissions or user-access tokens may be invalid or incorrect.
Is the EDL configured? Has the change been committed to the Panorama or Palo Alto device?
Do you get errors on the Agent?
If you're finding that Passive+ is taking too long, you can tune the retries using these settings in the Agent config file:
PanosRetry = 16
PanosWait = 2
Where Retry is the number of re-tries, and Wait is the number of seconds to wait between retries.
A note on EDL and HTTPS CAs
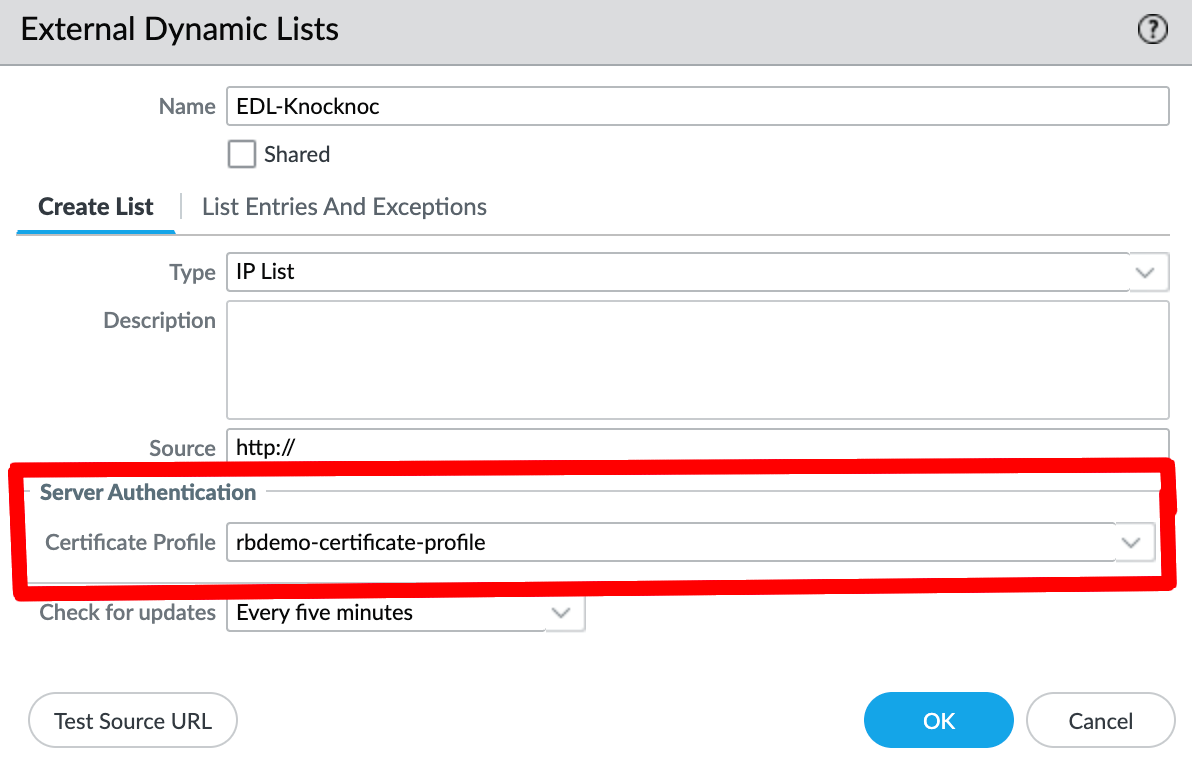
Whilst the EDL method utilizes HTTPS, using the https://username:token/ method may not adequately validated TLS/SSL certificate authorities. To utilize strict mode, use a CA profile as below:
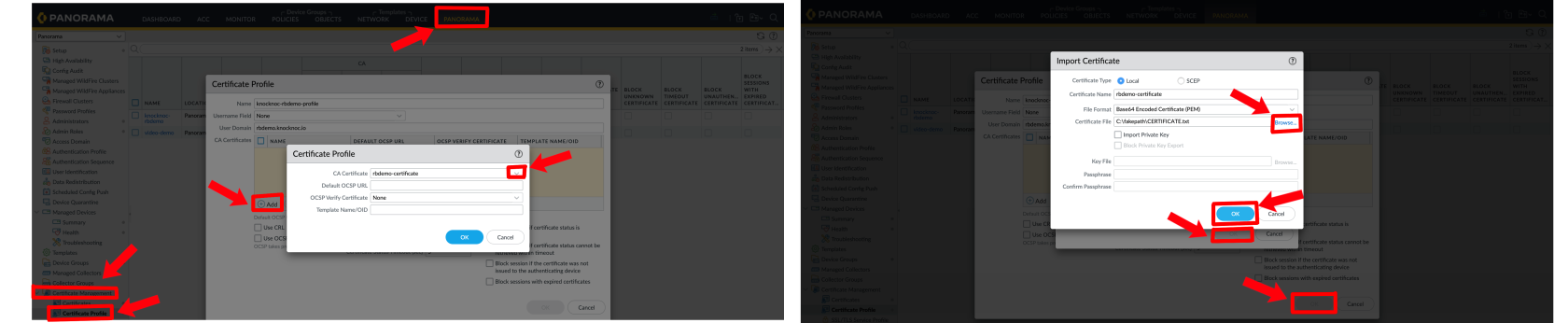
Panorama - Certificate Manager --> Certificate Profile --> Add --> Add --> CA Certificate Dropdown Menu --> Certificate File Browse --> Commit
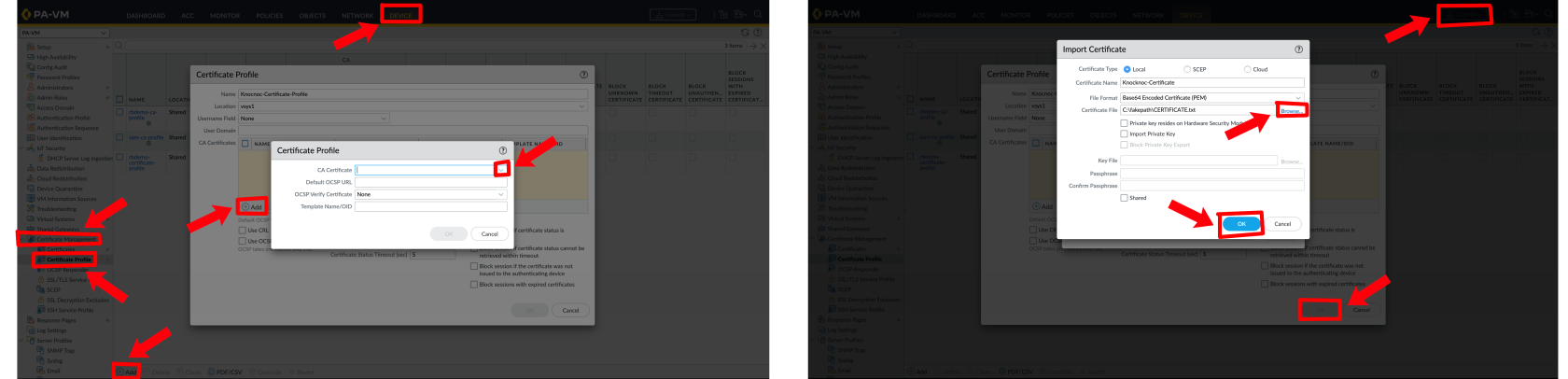
Palo Alto - Device --> Certificate Management --> Certificate Profile --> Add --> Add --> CA Certificate Dropdown Menu --> Certificate File Browse --> Commit
Select the certificate profile in the EDL (same spot as EDL from prior findings)