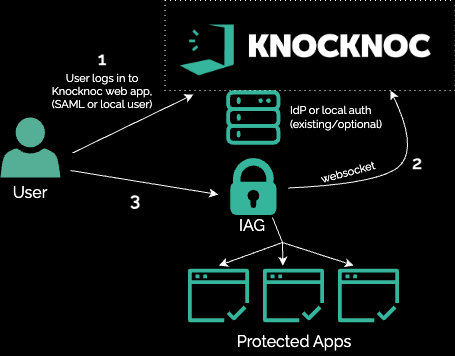
Web applications
There are various options for protecting your web application using Knocknoc
- Local Linux firewall orchestration on the host (eg: using IPSets)
- In-line firewall/control device orchestration (Fortigate, etc), via an adjacent Knocknoc Agent deployment
- HAproxy can sit in front of the web application(s) and forward authorised traffic
- Public cloud orchestration (AWS, Azure)
One major advantage of Knocknoc particularly for legacy web applications without single-sign-on or where shared passwords are forced (eg: ICS/OT network equipment, embedded systems, soho routers etc) is that SSO and MFA are quickly added to these back-ends without change.
If you have an embedded web server that only supports a single username/password, this can remain static and not be known to the connecting users. Only after the users have logged in to the IdP and conducted MFA or other policies, are they able to access the web application or service, providing you full user-level attribution and protecting the static credentials which remain unknown to the users within your configuration.
Additional token security can be added to further restrict access beyond the connecting users IP address.
Note that layer-7 filtering can be performed, allowing public/unauthenticated access to /public/ (for example) on your web application, but /internal/ can require Knocknoc authentication.
Talk to us about your needs as we have likely implemented it for other customers.