Allowlist (EDLs)
The Allowlist backend makes a list of active IP address grants available via the Knocknoc server API. This allows integration with appliances or clients that can be configured to poll a URL without the need for a Knocknoc agent to be deployed. This is sometimes known as "External Dynamic List" feature within firewalls.
CommonDevices Usesupporting Cases
EDLs (+ many others)
- Palo Alto External Dynamic Lists (EDL)
- Fortinet External Connectors
- Juniper
SRXSRX, SonicWall - F5 BigIP devices (IP intelligence)
- PfSense, many others
- Custom web
applicationsapplications, scripts, git-foo implementations, etc
Usage
Overall process
LogConfigureintothe Knocknoc Server: Set up a Passive Knoc.- EDL Configuration: Configure the device to point the EDL to the Knocknoc distribution server.
- Security Policy Rule: Create a policy referencing the dynamic address and other relevant parameters to suit your
KnocknocintendedadminfirewallUI at/admin Click
Knoc configuration
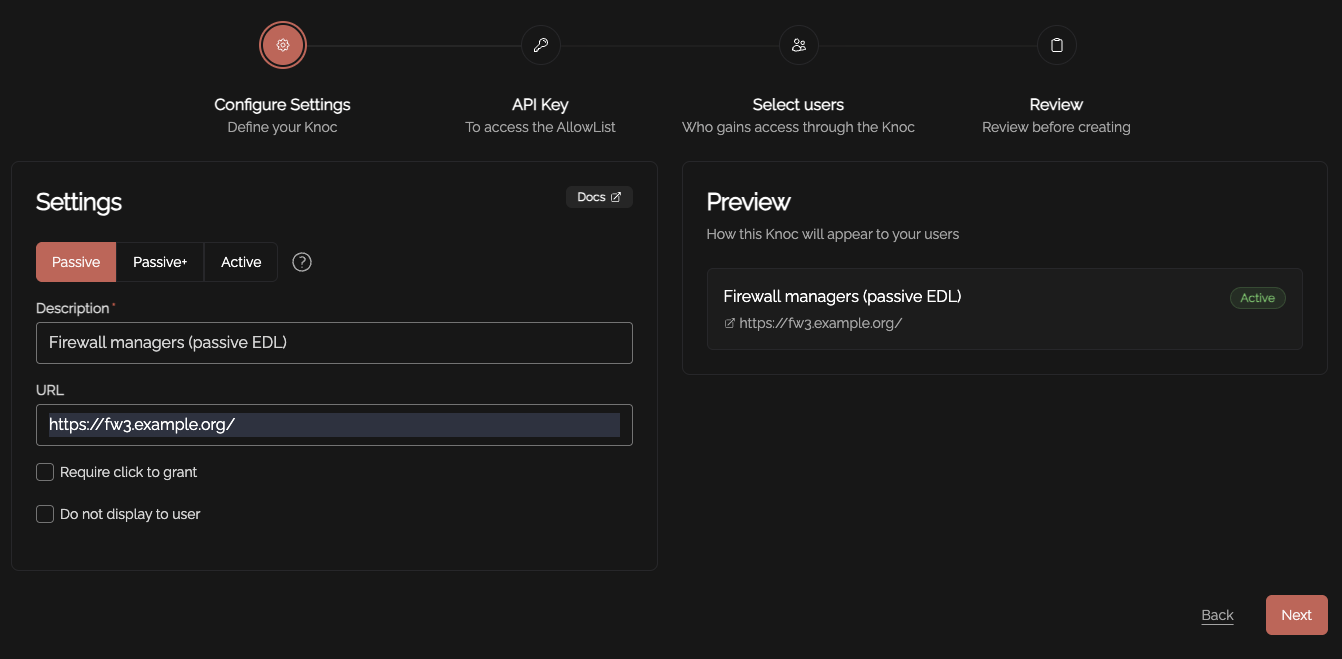
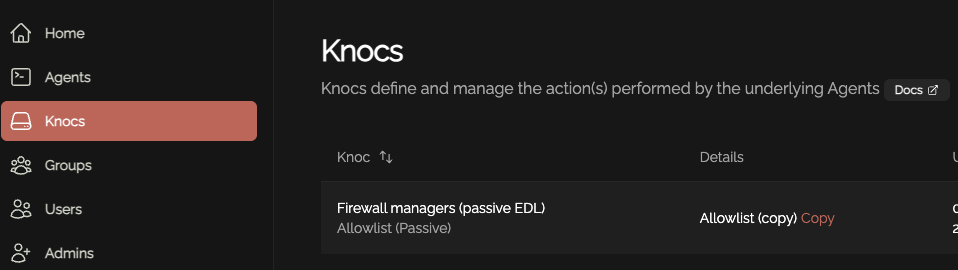
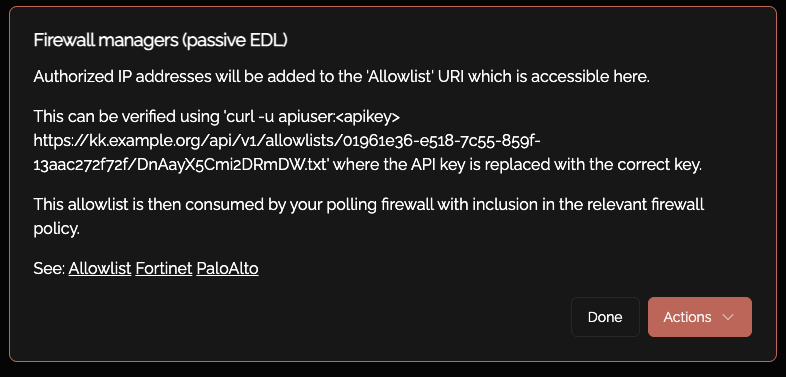
Create a Knoc under Firewalls/Appliances. Select Passive. Note that no Agent is required for this configuration as the Server is publishing/hosting the Allowlist.
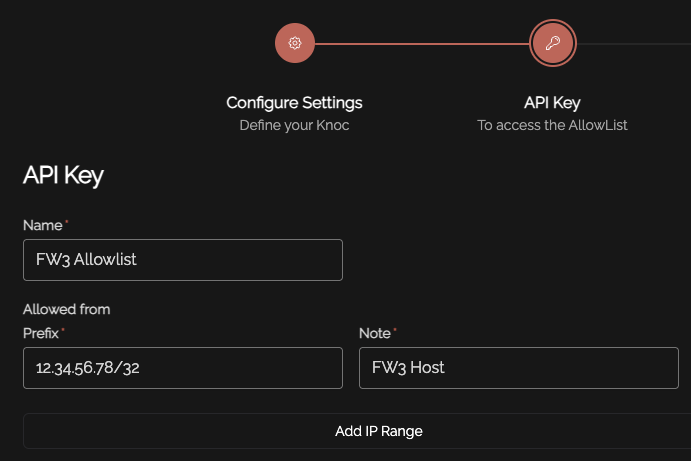
Set an API keyskey name, and createdefine aany key
Be This can be edited.
Copy the providedAPI URL.key/token Thisthat is wheredisplayed, your allowlist grantsyou will not be published.able
Copy
username:apikeypassword: <the API keysecretandcapturedstore this for future use.You now need the unique and random URI published per-Knoc, to be added to the consuming firewall/system.
Copy/paste the URL from the
Adminrelevantportal>
You ACLcan willalso appear assee the below,URI clickfor this Passive Allowlist/EDL by clicking on the copyKnoc:
You can test thisthe EDL including authentication using Curl as below:
curl https://demo.knocknoc.io/api/v1/allowlists/XXX -u apikey:secrettoken
Pros
- Any device that can poll for a list of IP addresses can integrate with Knocknoc, a good solution for unidirectional network environments or assets deep in an organisation.
- Does not require a Knocknoc agent to be installed.
- Provides an additional option for custom integrations.
Cons
Knocknoc cannot know if/when grants are applied on the target system, therefore less feedback is provided to users.- Polling is typically time-based not event based, this may see a user waiting for access after logging in - depending on the poll interval supported by the infrastructure or appliance.
Since Knocknoc only publishes the active allowlist, the client must implement revocation/deny.
See below on how these can be incorporated in to major vendors via external lists:
- Fortigate (Fortinet):
https://docs.fortinet.com/document/fortigate/6.2.0/new-features/625349/external-block-list-threat-feed-policyFortinet Knocknoc how-to or the Vendor documentation - PAN OS (Palo Alto):
https://docs.paloaltonetworks.com/pan-os/11-0/pan-os-admin/policy/use-an-external-dynamic-list-in-policy/external-dynamic-listPalo Knocknoc how-toandor thehttps://docs.paloaltonetworks.com/pan-os/11-0/pan-os-admin/policy/use-an-external-dynamic-list-in-policy/configure-the-firewall-to-access-an-external-dynamic-listVendor 1, Vendor 2. - PfSense:
https://docs.netgate.com/pfsense/en/latest/packages/pfblocker.htmlVendor docs - Sonicwall:
https://www.sonicwall.com/support/knowledge-base/what-are-dynamic-external-objects-groups-and-how-can-we-configure-it/200507105852280Vendor docs - Checkpoint:
https://sc1.checkpoint.com/documents/latest/APIs/#cli/add-network-feed~v2%20Vendor docs
Other platforms are supported, however talk to us about our native/API integrations as these offer many benefits over the time-based polling approach.
The Allowlist backend is available in Knocknoc v6.0.0.