Sophos (SFOS/XGS)
The Sophos SFOS/SGX based devices provide firewall and UTM capabilities. This replaces the previous UTM devices, which can be integrated here.
SFOS (XGS) Configuration
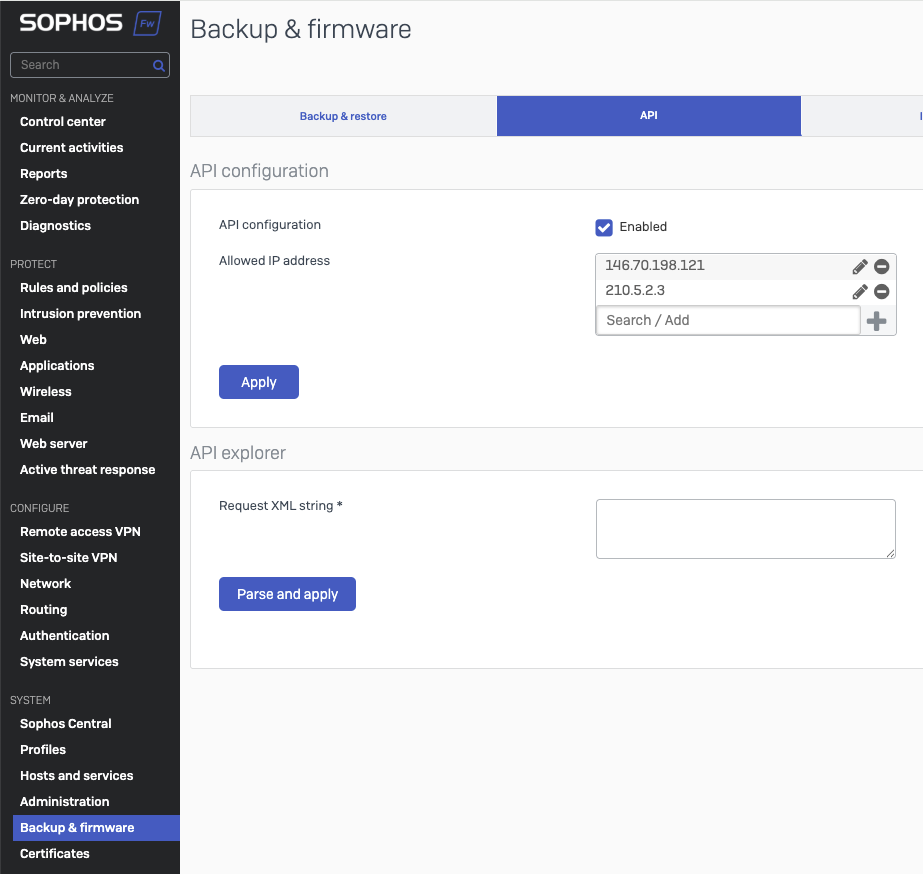
Enable the API and set permitted source IP address(s)
- Go to System -> Backup & Firmware -> API -> API Configuration
- Enable the API
- Add the Knocknoc Agents IP address to the allowed IP addresses (to use the API)
- Click Apply
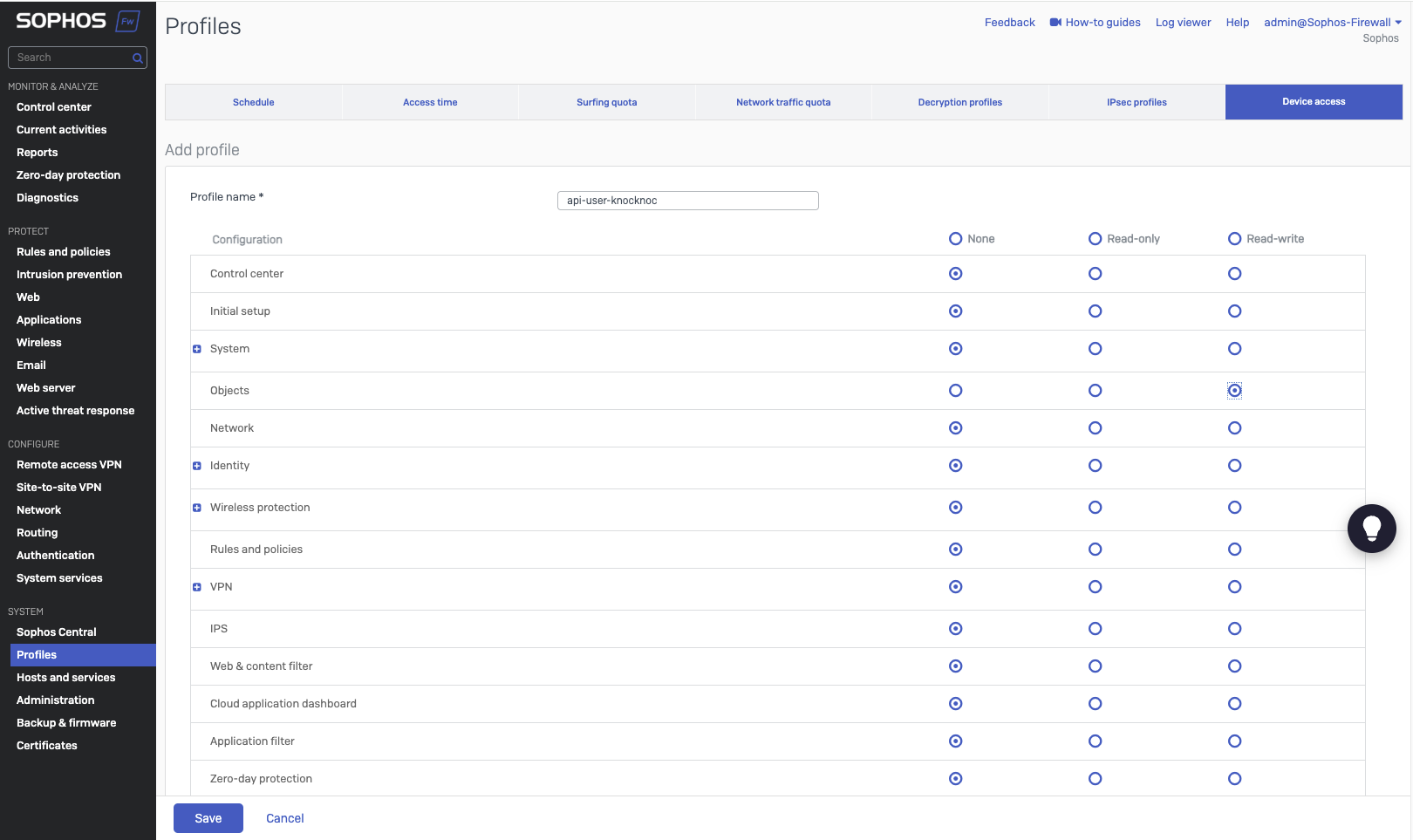
Create a restricted API user profile
- Go to System -> Profiles -> Device access
- Click Add

- Create a suitable name, eg: api-user-knocknoc
- Set all permissions to "none"
- Set System -> Objects to "Read-write"
- Save
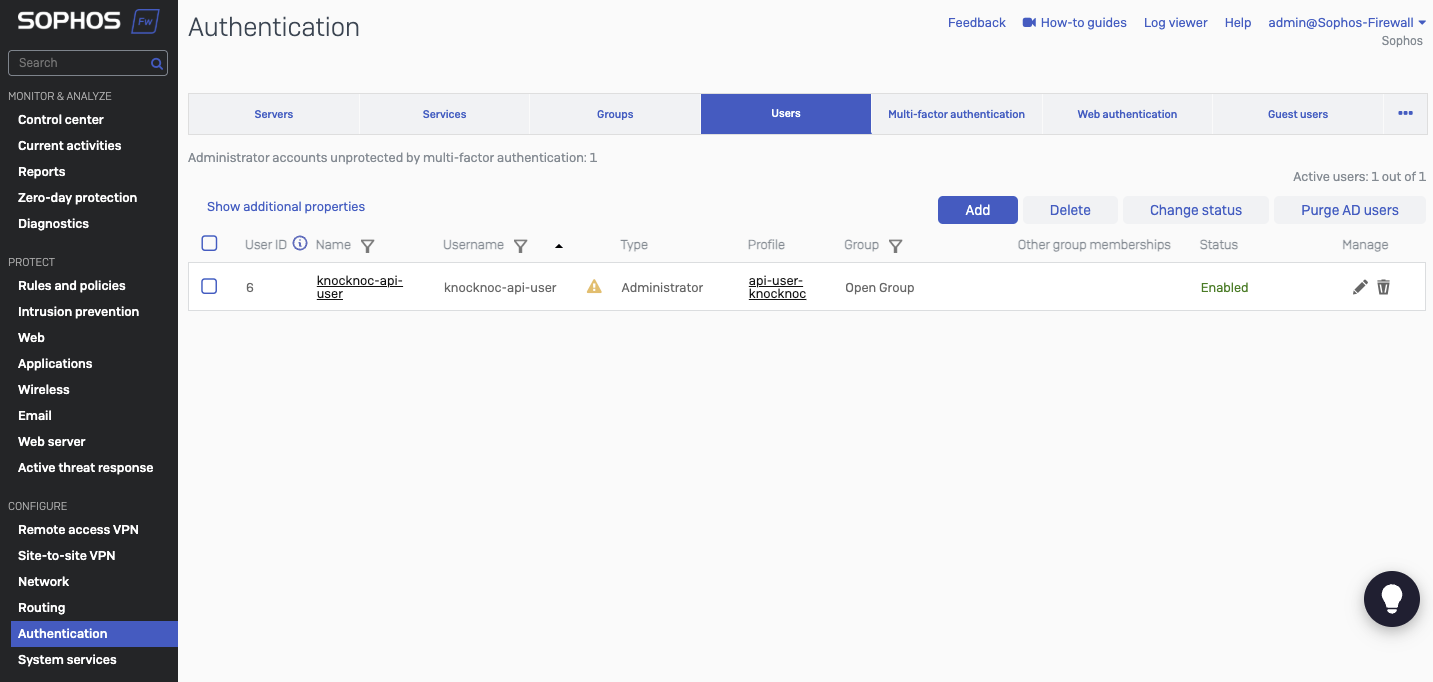
Create a user, linking it to the user profile
- Go to Configure -> Authentication -> Users
- Click Add
- Set a username and name, eg: knocknoc-api-user
- Provide a meaningful description
- Set User-type as Administrator
- Select the "api-user-knocknoc" profile we created earlier
- Provide an email address
- Group should be "Open Group"
- Leave other defaults
- Set "sign in restriction" to either "Selected nodes" and provide the same Agent IP addresses, or depending on the firewall configuration any-node may be appropriate if access is open for other users outside the API use.
- Save
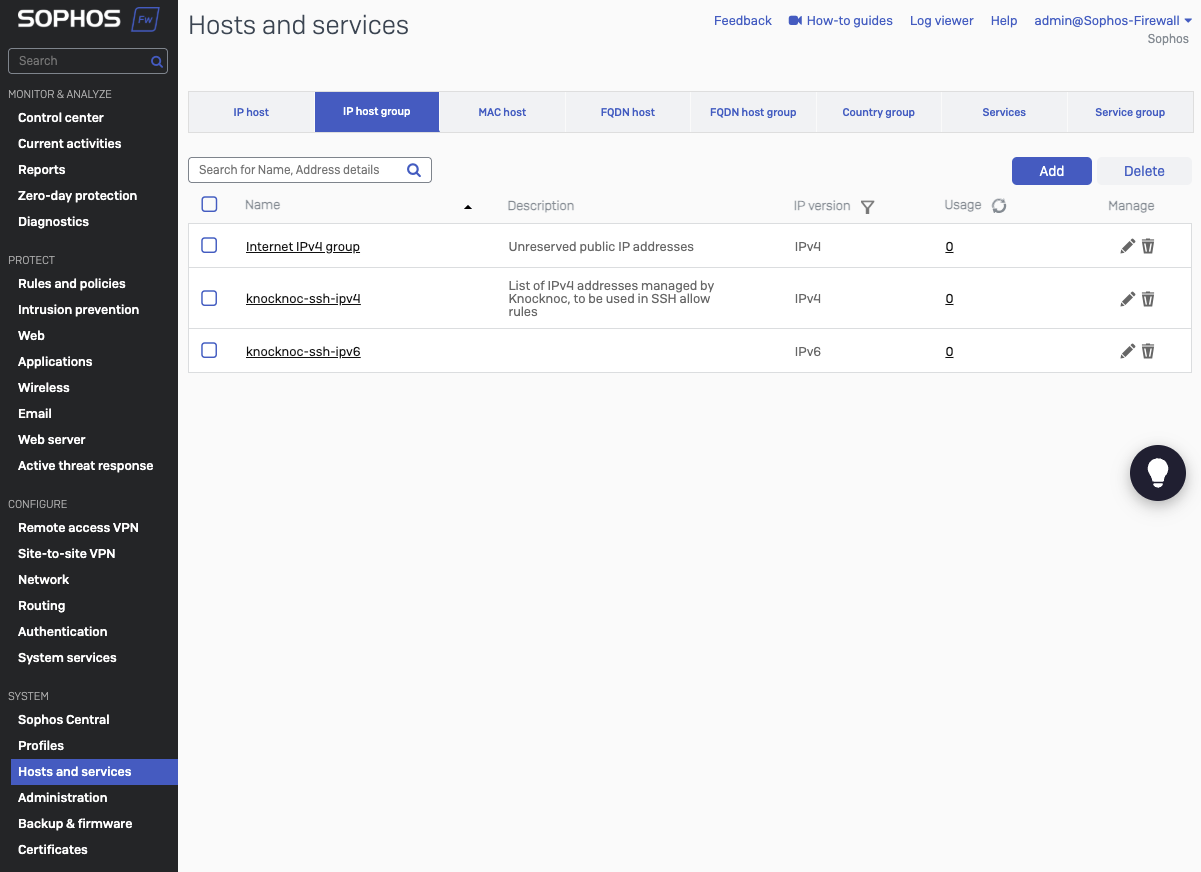
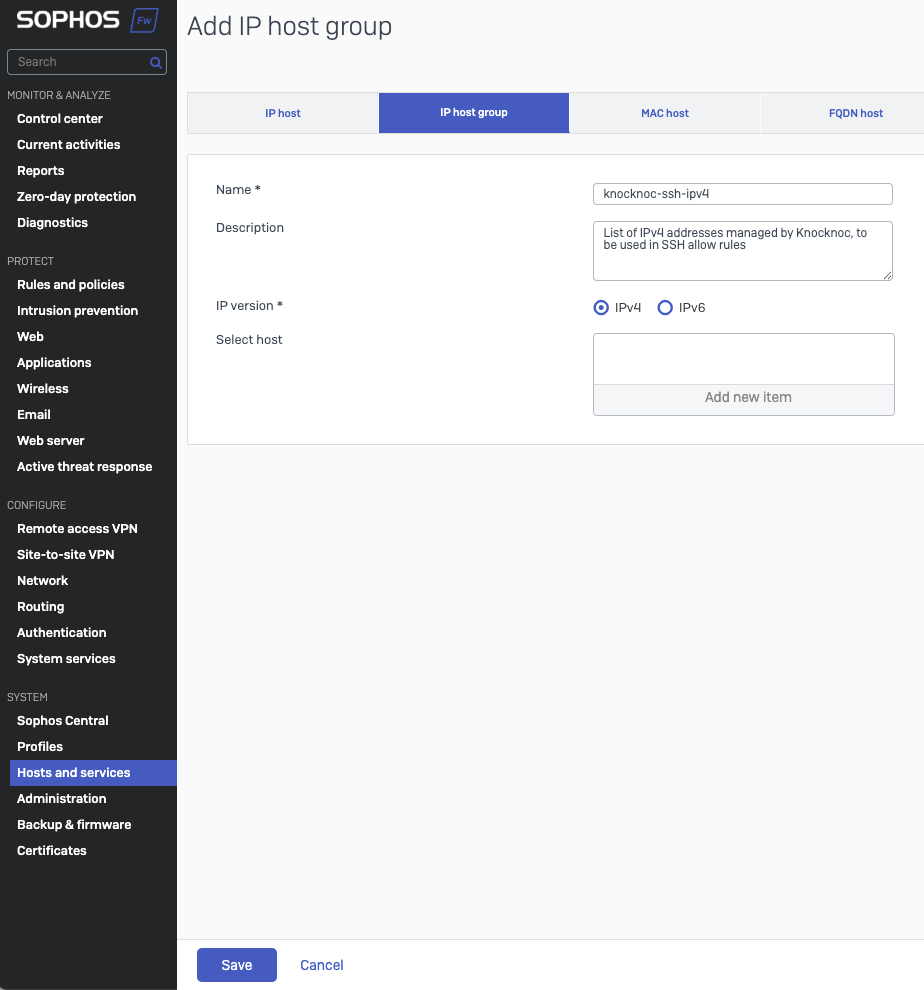
Create an IP Host Group for Knocknoc to add/remove IP addresses
- Go to System -> Hosts & Services -> IP Host Group
- Click Add
- Provide a name, this will be used later in the Knocknoc Server configuration
- Type in a meaningful description
- Select IPv4 or IPv6. Note you need to create an IP group for each v4/v6 protocol, if needed.
- Leave the 'select host' empty
Knoc Configuration
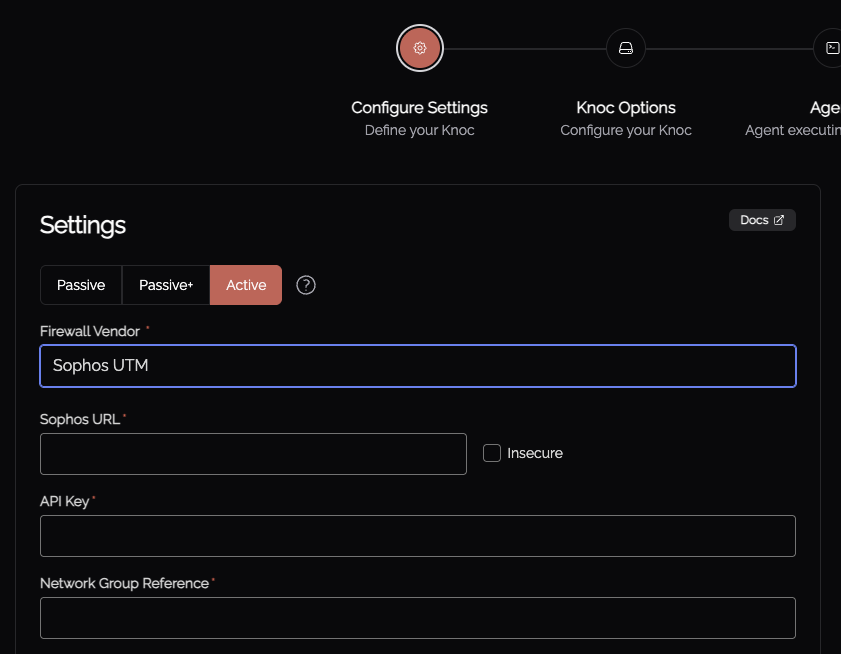
Select the "Firewalls / Appliances" Knoc configuration, selecting "Active", then "Sophos SFOS"
Enter the URL of the Sophos device (eg: https://1.2.3.4:4444/)
Select "Insecure" if the HTTPS certificate is not CA signed or in the trusted certs. Whilst this is discouraged, if you have deployed the Knocknoc Agent in a network location alongside the device this reduces the risk of MITM.
Provide the API key.
Provide the 'network group reference', also known as the Internal name. This is obtained per network group from the Knocker utility in the previous step.
Assign this to a test user or a group, and proceed to testing.
Testing it out
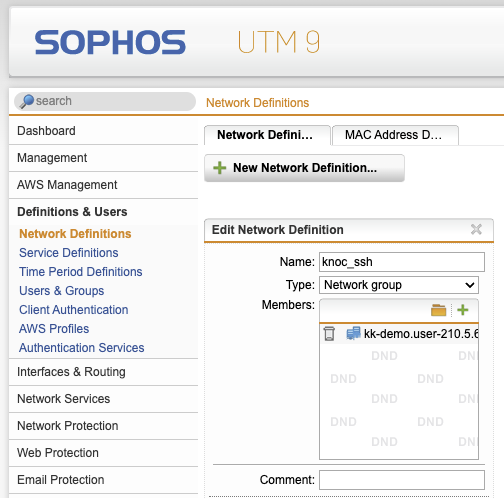
Log in to the Sophos UTM device, browse to Definitions & Users -> Network Definitions -> Network Groups.
Log in to Knocknoc as the user that has been assigned this Knoc.
Select the relevant group on the Sophos UTM device, you'll see the users IP address has been added to the network definition, along with their username.
You're good to use that group within a policy.