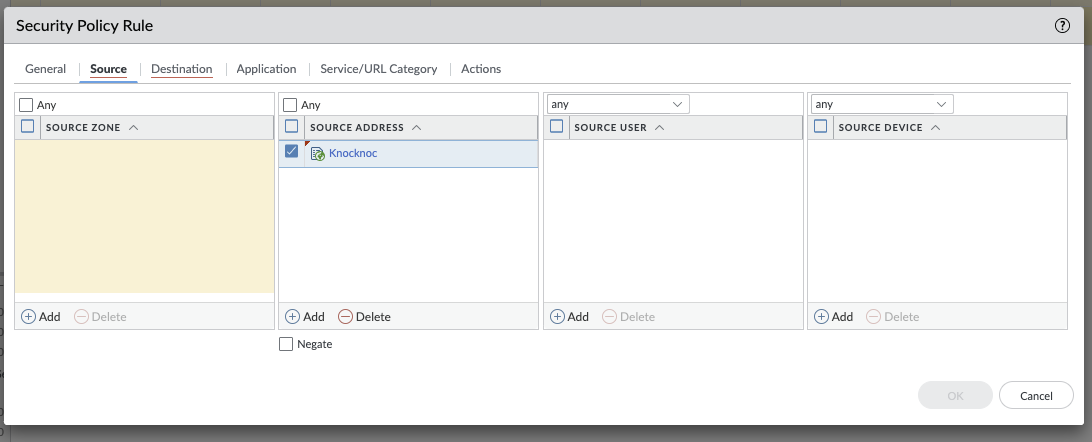
Palo Alto
BackgroundPassive, Active or a combination
Passive - Knocknoc's Allowlist features provides a very powerful integration with firewalls that support a External Dynamic AddressLists Lists.or EDLs. This feature pulls from the Knocknoc server a list of IPs of authenticated users, in the correct group/for the assigned firewall policy. The drawback of this feature is that the list can only be fetched every 30 seconds or slower.5 minutes in the case of Palo Alto.
ThisActive guide- explainsKnocknoc's howPalo Alto back-end capability utilises the Palo API to useactively orchestrate the provideddevice, scriptinserting and Junosremoving configuration snippet to automate the process of updating dynamicIP addresses onas a Juniper SRX device. The script is designed to securely execute the request security dynamic-address update command through SSH, leveraging predefined credentials and key-based authentication.
By just triggering a refreshpart of the allowKnocknoc list,Grant weprocess. This can beattake the 30 second penalty, allowing the login processtime to be smooth for users, and also not changing"commit" the configuration of the firewall. Given a refresh of the dynamic list doesn't actually change the on disk config of the device, no 'commit' command is required. This should satisfy security teams that require change control for config changes to the firewalls,device which is a Palo constraint. Newer versions of Palo can offer better speeds. If commit speeds are a problem, using the Passive approach with an Active trigger can be the fastest approach.
Passive with Active Trigger - the Passive EDL can be utilised in conjunction with an Active API hit to trigger a live refresh from the EDL. This shortens the time taken for polling, and allowscan foroutperform aActive fastrule butmanagement leastdue privilegeto waythe Commit process of dynamicthe allow-listing.Palo framework.
Full Configuration Flow
- Configure the Knocknoc Server: Set up Allowlist and
scriptPaloACLsBackend Dynamic Address FeedEDL Configuration:Set upConfigure thefeed-serverPaloandtoassociatepoint thefeedEDLwithtoathedynamicKnocknocaddressdistributionname.server. You also need to extract the server CA/chain for the Palo.- Security Policy
Configuration:Rule: Create a policy referencing the dynamic address and other relevantparameters.parameters ConfiguretoKnocknocsuitSSHyouruser:intendedanfirewallSRX user with least privilege and the correct key.policy.- Allocate ACLs: Associate users and groups to ACLs, then test.
ConfigurePalo Knocknoc Server
Agent Setup: Install anagenton a machine that can SSH to the Junos SRX management IP.Add Allowlist Backend: Setup an Allowlist backend in Backends -> Create Backend -> Type Allowlist and give it a name.Add Agent Backend: Create another Backend, Type Script, choose your Agent from Step 1, and enter/opt/knocknoc-agent/scripts/junos-reload-list.shas the script name.Create Allowlist ACL: ACLs -> Create ACL and select the Allowlist backend from Step 2. Give it a name and a URL. The users will see this name and URL.Create Agent ACL: ACLs -> Create ACL and select the Agent backend from Step 3. The ACL name is important - it will be the name of your SRX dynamic address name later.Allocate ACLs: Go to Groups, and create a group that contains both ACLs from step 4 and 5. Include any local users, SAML users will get included automatically if the group name matches.API Key: Go to API Keys and click Create API Key. Enter a name and make sure to select the allowlists.read capabilty. Be sure tosecurely savethe API key presented as it will only be displayed once. You can click the little copy icon to copy it into your password manager.
JunosAlto Configuration
Configuring the Dynamic Address Feed and Feed-Server
set security dynamic-address feed-server knocknoc url "https://apikey:<api_key>@<knocknoc_server>:<knocknoc_port>"
set security dynamic-address feed-server knocknoc update-interval 30
set security dynamic-address feed-server knocknoc feed-name knocknoc_feed path /api/v1/allowlists/xxxxxx/yyyyy.txt
set security dynamic-address address-name knocknoc_allow profile feed-name knocknoc_feed
Feed-Server Configuration:knocknoc: The name of the feed server.url: URL for the dynamic address feed, including authentication details. Use the key you saved in Step 7 above.update-interval: Frequency (in seconds) for fetching updates. (30 through 4294967295)feed-nameandpath: Specify the name of the feed and the exact API path to retrieve the address list.
Dynamic Address Profile:knocknoc_allow:External DynamicaddressListname associated with theknocknoc_feed.
More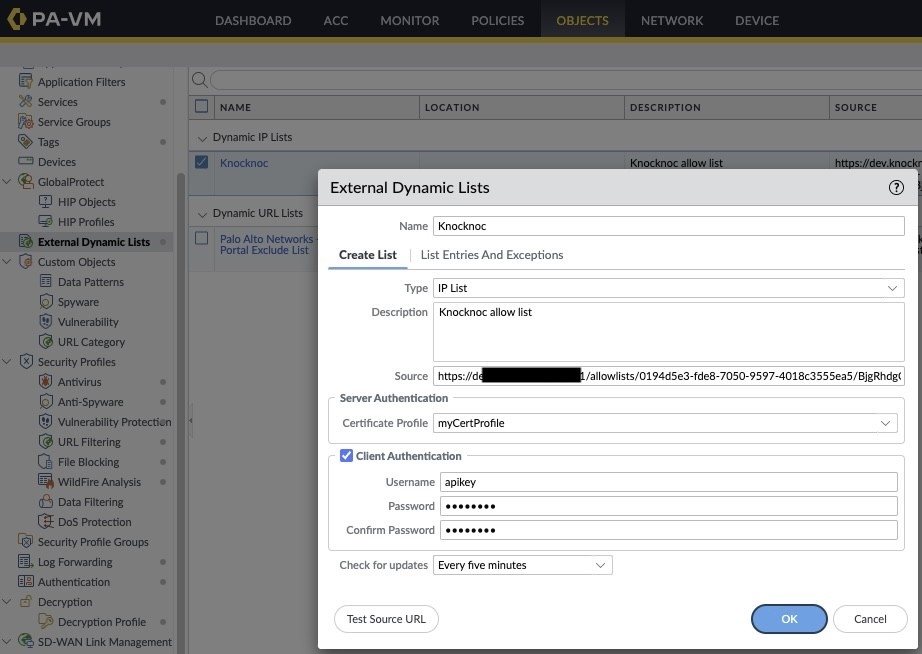
detail on these options can be found in the Juniper documentation.
Configure Least Privilege Junos User
login {
class knocknoc {
permissions [ security security-control ];
allow-commands "(request security dynamic-address update address-name knocknoc_allow)|(quit)";
}
user knocknoc {
uid 2000;
class knocknoc;
authentication {
ssh-rsa "<public-key>";
}
}
}
Custom Login Class:Name:knocknocPermissions:securityandsecurity-controlAllowed Commands: Restricts the user to only execute therequest security dynamic-address updatecommand for a specific address name (knocknoc_allow) and quit the session.
User Account:Username:knocknocUID:2000(arbitrary; adjust as needed)Authentication: Configured for SSH key-based authentication.
Replace <public-key> with the public key corresponding to the private key stored in /opt/knocknoc-agent/privkey.
Using the Dynamic Address in Firewall Rules
The dynamic list fetched using the knocknoc_allow dynamic address nameEDL can be integratedselected intowithin the Source Address section. This is effectively a securitydynamically policyupdated to allow specific traffic. Below is a configuration example based on a practical implementation.
Configuring Security Policies
set security policies from-zone Outside to-zone Inside policy knocknoctest match source-address knocknoc_allow
set security policies from-zone Outside to-zone Inside policy knocknoctest match destination-address knocknoc_192.168.84.18
set security policies from-zone Outside to-zone Inside policy knocknoctest match application junos-ping
set security policies from-zone Outside to-zone Inside policy knocknoctest then permit
Source Address:Matches the dynamic addressknocknoc_allow.Destination Address:Matches a specific address (e.g.,knocknoc_192.168.84.18) configured separately in the address-book.Application:Specifies the typelist oftrafficauthenticated(e.g.,andjunos-ping).authorised Action:Permits the traffic matching the policy.
Defining the Destination Address in Address-Book
set security address-book global address knocknoc_192.168.84.18 192.168.84.18/32
Replace192.168.84.18with the actualusers IPaddress of your resource (e.g., VPN appliance).
Script on Agent Setup
Script Location:Check the script at/opt/knocknoc-agent/scripts/junos-reload-list.sh. Knocknoc-agent includes the script from version 7.2.Secrets File:Create a secrets file at/opt/knocknoc-agent/.junossecretswith the following format:<username> <hostname>Ensure the file is secured with appropriate permissions (e.g.,chmod 600).Private Key:Store the SSH private key at/opt/knocknoc-agent/privkeyand secure it (e.g.,chmod 600).Junos Configuration:Ensure the Junos device is configured to accept therequest security dynamic-address updatecommand with appropriate permissions.
Security Considerations
Secure the secrets file and private key with proper file permissions.Restrict theknocknocuser's permissions to only the necessary commands.Regularly rotate keys and update the secrets file accordingly.
By following this guide, you can automate dynamic address updates on a Junos SRX securely and efficiently.