Introduction
Welcome to the Knocknoc Admin Guide.
This is an advanced guide and covers installation, administration, tuning and troubleshooting. For general access guides, here is the simplified User Guide.
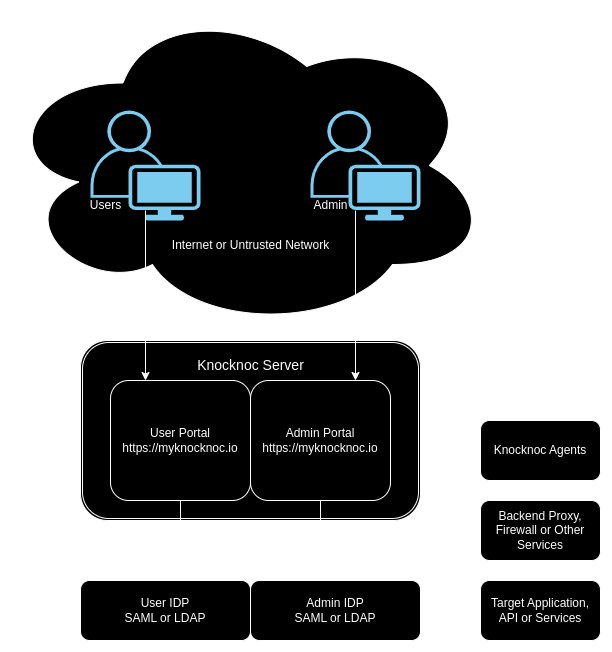
Setting up Knocknoc for the first time can appear easy, but it is important to understand how it fits into your security architecture. Knocknoc is an important component in reducing your attack surface, and allows you fine grained control over what resources each of your users can access. In most cases Usersusers are generally expected to authenticate to the target resources as well, sowith pleasethis in mind consider Knocknoc as part of a comprehensive defence strategy. In other cases, like video feeds, or SIP connections, extra authentication isn't workable, so you need to decide as part of your security strategy how to manage these risks.
Setting up Knocknoc for the first time can appear easy, but it is important to understand how it fits into your security architecture. Please have a read through the following guides, or jump straight the topic you are searching for:guides:
Getting Started
Access Control
Installing Knocknoc Server
Installing Knocknoc Agent
Configuring Backends
Authentication
The architecture of a typical Knocknoc environment is often as follows: