Microsoft Azure NSG
Overview
This integration isallows designedfor IP addresses to managebe nameddynamically locationsmanaged in Microsoftwithin Azure ConditionalNetwork AccessSecurity policiesGroups via(NSGs), which are used by default as the Microsoftinner Graphfirewalls API.protecting Itvirtual allowsmachines. usersOther toAzure add, delete, or flush named locations related to specific IP addresses. This system can also be used to directly limit access to servicesassets (eg:PaaS outlooketc) versusare teamsmanaged versususing portal)separate through various conditional access policies, as opposed to a blanked policy over Microsoft 365 as a whole, which helps reduce exposure in the event of credential or token loss.Knocs.
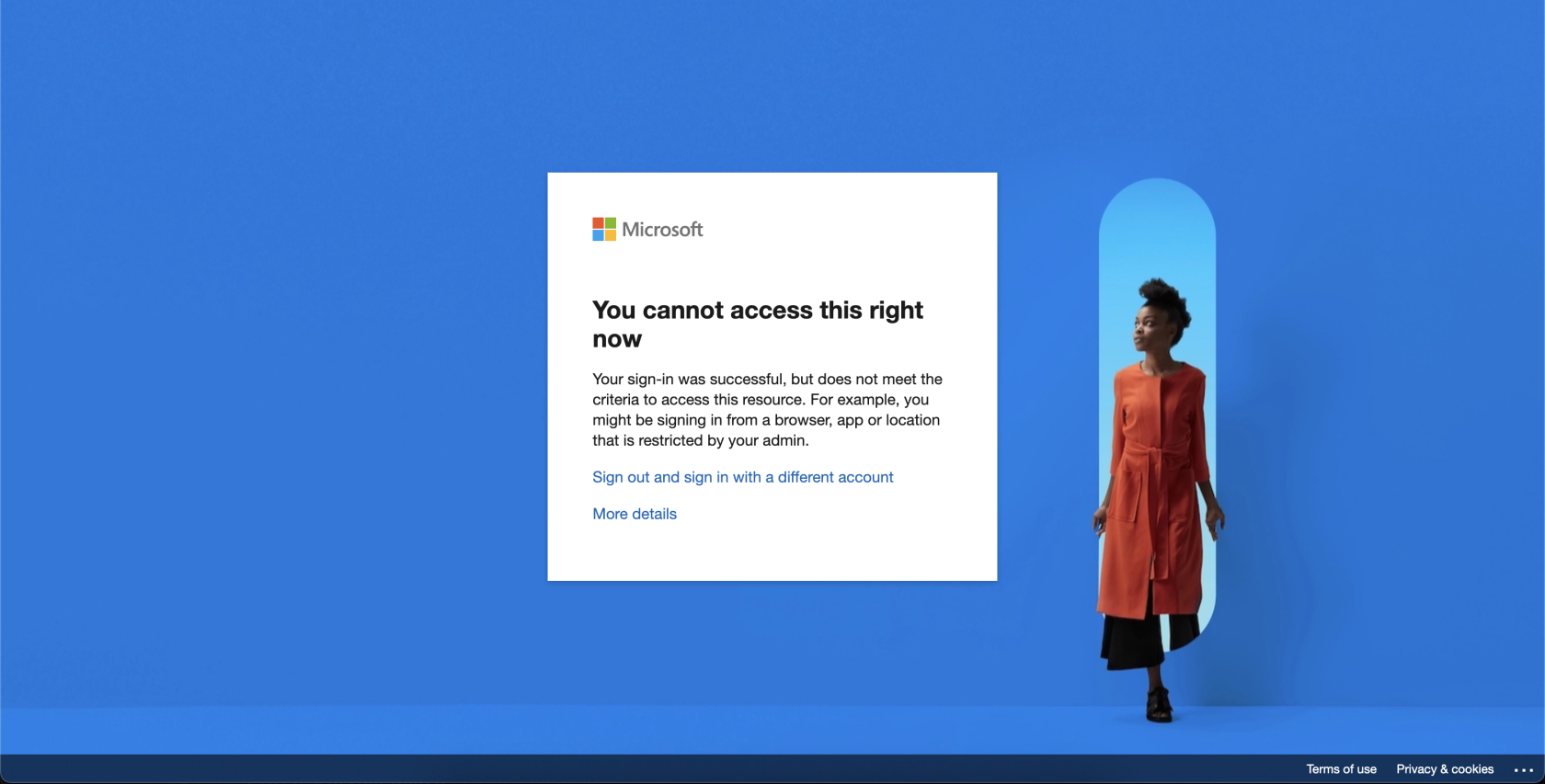
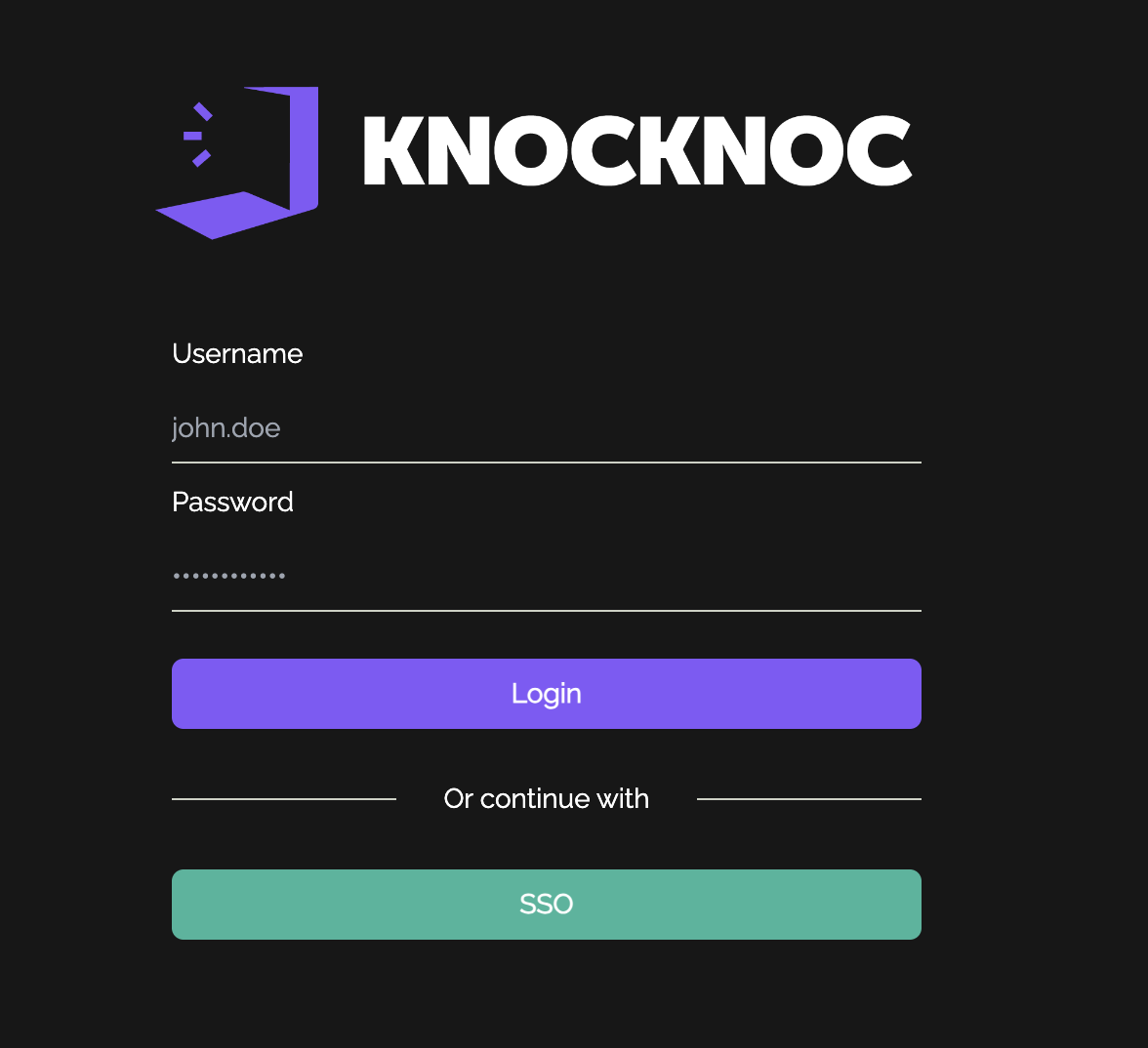
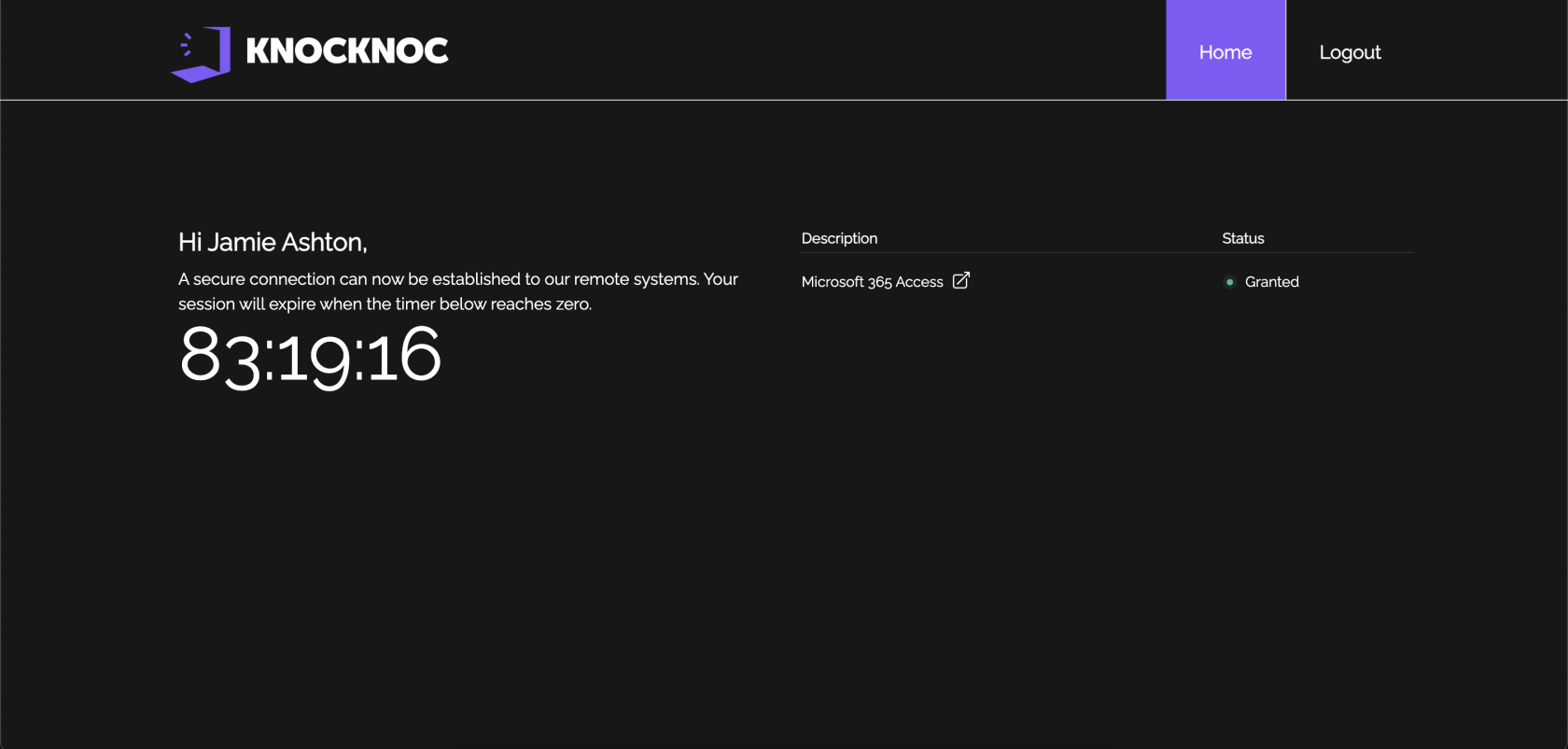
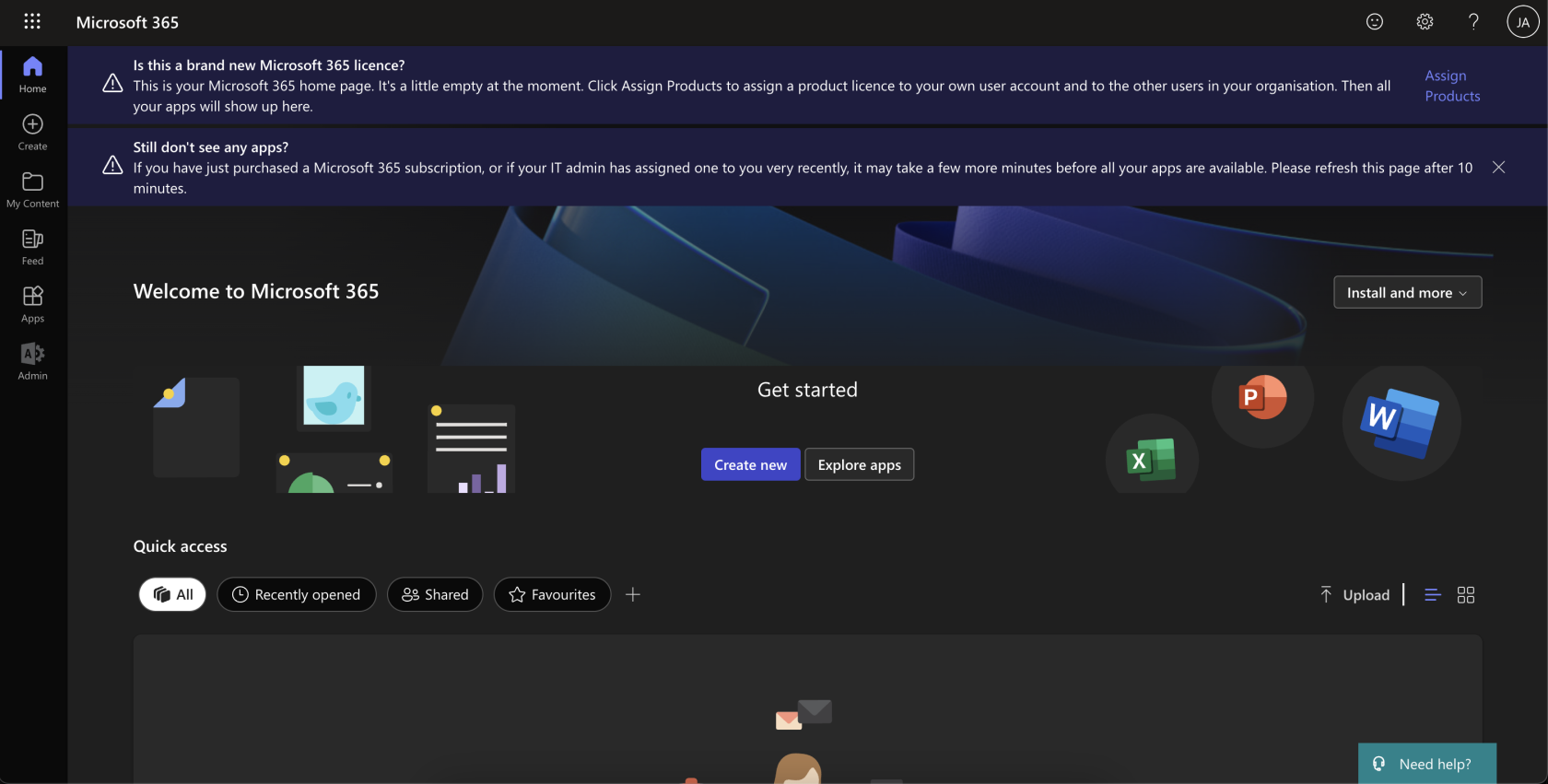
An example of a user's experience can be found below:
User attempts to access Microsoft 365 services:User must authenticate with knocknoc and will see their granted ACL on the right hand side:User can now access Microsoft 365 services:
Prerequisites
BeforeThis running this script, ensure that you haveutilizes the followingAzure prerequisitesCLI binary, which must be installed andon configured:the Agent machine.
Powershell -Install the LATEST version of PowerShell on your system. You can check the latest version and instructions for your architecture here:https://github.com/PowerShell/PowerShell/releases/latest
For Debian, follow these steps:# Update the list of packages sudo apt-get update # Install pre-requisite packages. sudo apt-get install -ywgetazure-cli #DownloadUpdate it. # If thePowerShellversionpackageisfilesignificantlywgetbehind, you may need to install from Microsoft (see below) az upgrade # If you have any errors running, you may need to install from Azure directly # do this if you get warnings or errors # #sudo apt remove azure-cli #rm -rf ~/.azure #curl -sL https://github.com/PowerShell/PowerShell/releases/download/v{latest-version}/powershell_7{latest-version}.deb_amd64.debaka.ms/InstallAzureCLIDeb################################### # Install the PowerShell package| sudodpkgbash-i powershell_{latest-version}.deb_amd64.deb # Resolve missing dependencies and finish the install (if necessary) sudo apt-get install -f # Delete the downloaded package file rm powershell_{latest-version}.deb_amd64.deb
Permissions in Azure
To interact with the Azure EnterpriseNSG Application:- Anvia enterprisethe applicationAPI must- beyou createdneed to allow knocknoc to authenticate and change conditional access policies and named locations. Create an enterprise application,first create a clientservice secret,principal and copyassign the application'slimited client id, azure tenant id and secret. You'll need these later.Note: If you are also using Entrapermissions, as yourshown IdP,below:
Create surea thiscustom isrole clearly(for definedlimited inNSG theedit nameaccess)
-
enterpriseGo
applications.toForAzureexample,Portal:yourhttps://portal.azure.comIdP app might be called "knocknoc-saml", and your ACL app might be called "knocknoc-conditionalaccess." -
MicrosoftSearchGraphforAPI“Subscriptions”Permissions:andEnsureselectthatyour subscription. -
In the
applicationlefthasmenu, click “Access control (IAM)”. -
Go to the
necessary“Roles” tab and click + Add > Add custom role. -
Basics tab:
-
Name:
Knocknoc NSG Edit -
Description:
Can read and edit rules in a Network Security Group.
-
-
Permissions tab:
-
Click + Add permissions
to -
In the search box, type:
networkSecurityGroups -
Add these permissions:
-
Microsoft.Network/networkSecurityGroups/read -
Microsoft.Network/networkSecurityGroups/securityRules/read -
Microsoft.Network/networkSecurityGroups/securityRules/write -
Microsoft.Network/networkSecurityGroups/securityRules/delete
-
-
Click Add
-
-
Assignable scopes tab:
-
Click + Add assignable scope
-
Select your resource group, or subscription if broader access
theisMicrosoft Graph API. For knocknoc to work as intended, two graph API permission are required:
fine. -
Review
+Keeping these permissions as restrictive as possible reduces your attack surface significantly, and prevents a major breach increate theeventcustomthatrole.your
application -
Create a dedicatedService applicationPrincipal andin setAzure ofPortal
1. Go to the Azure Portal
More
- Visit: https://
learn.microsoft.com/en-us/graph/api/conditionalaccessroot-post-namedlocations?view=graph-rest-1.0&tabs=httpportal.azure.com
2. Search for “App registrations”
- In the top search bar, type
App registrationsand select it.
3. ConditionalClick Access“+ Policy/Policies:New registration”
- Name:
knocknoc-nsg-updater(or anything you prefer) - Supported account types: Leave as "Single tenant"
Knocknoc(default) - Redirect URI: Leave blank (not needed for non-interactive apps)
Click Register
4. Go to “Certificates & secrets”
- Click + New client secret
- Give it a name like
nsg-automation - Set expiration (e.g., 6 or 12 months)
- Click Add
Copy the generated secret value immediately — you won’t be able to distinguish between policiesretrieve it canlater.
5. andFind policiesApplication it(client) cannot.ID
-
looksIn
fortheaOverviewprepending "knocknoc_" aheadtab oftheyournameappofregistration:-
Copy the
ACL.Application (client)ForIDexample, -
conditionalAlso
access policy might be named"knocknoc_financedepartment"with specific rules around applications and services that group can access. These must be createdPRIORto configuring anything incopy theknocknocDirectoryadmin(tenant)portal.ID
a -
6. Assign the Custom Role (Knocknoc NSG Edit)
-
Go to your Resource Group (or subscription) where the NSG lives.
-
Click Access control (IAM).
-
Click + Add > Add role assignment
-
Choose:
-
Role:
Knocknoc NSG Edit(or your custom role name) -
CredentialsAssignFileaccess to:EnsureUser,thatgroup,aorcredentialsservicefile is present (it is installed by default when the knocknoc-agent is first installed) at/opt/knocknoc-agent/etc/entra-credentials.shprincipalwith the following content:entra_clientid="" -
YouSelect:willFindneedandto input the necessary ClientID forselect your registeredAzureappEnterprise Application, your Azure Tenant ID and your application's client secret.(nsg-updater)
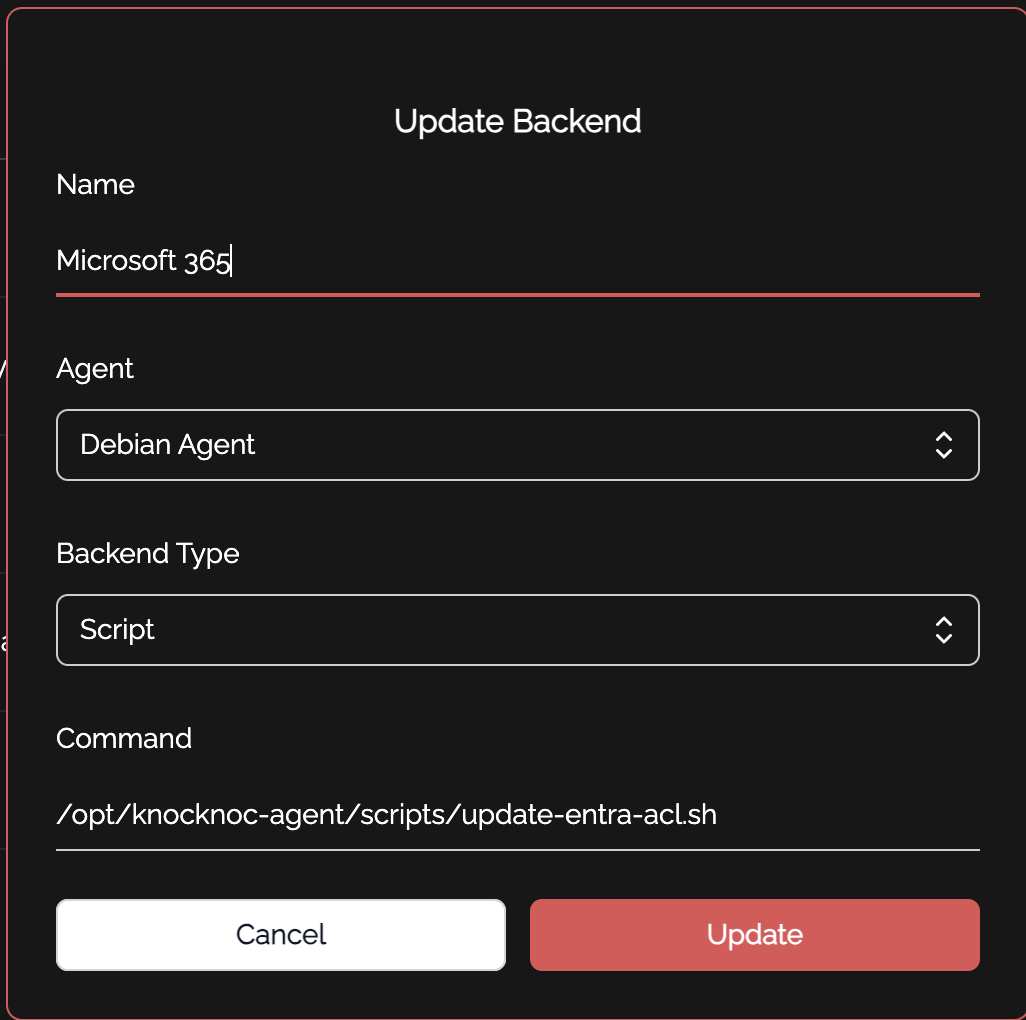
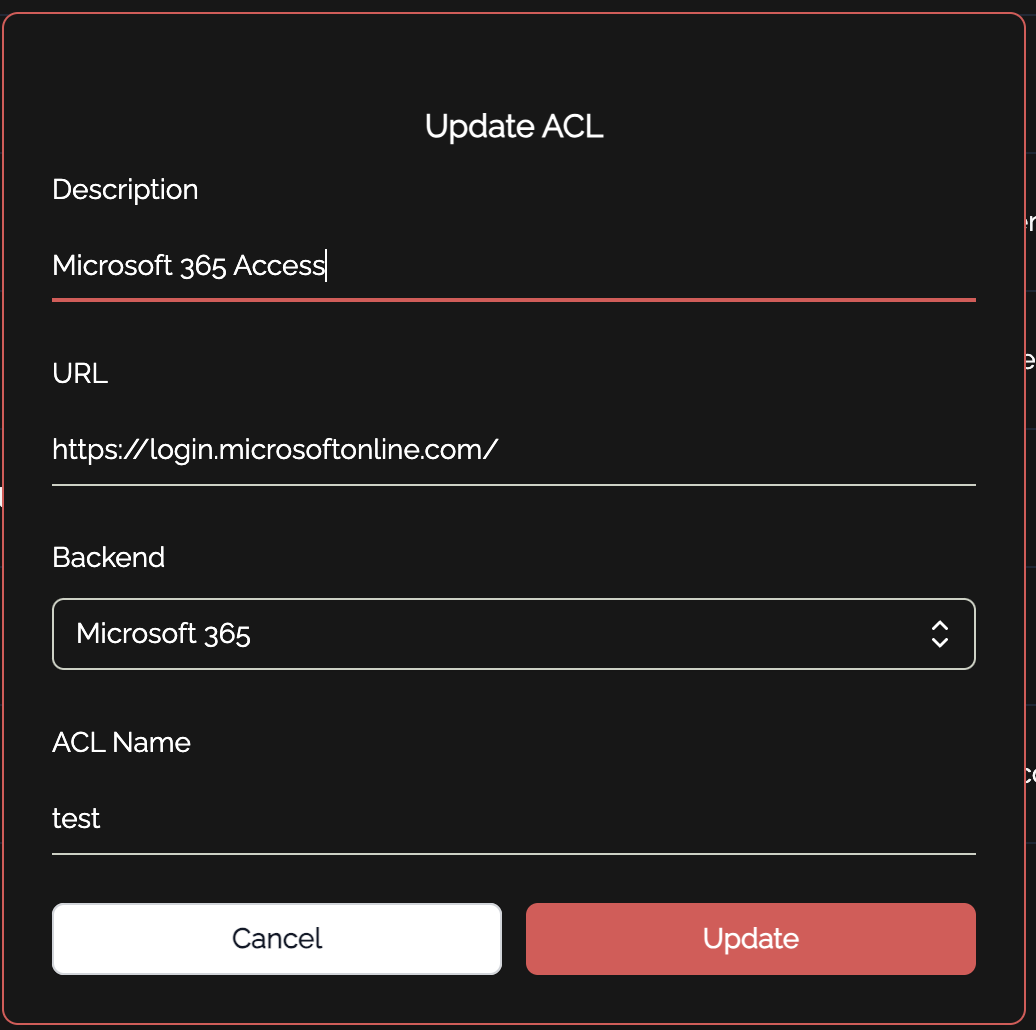
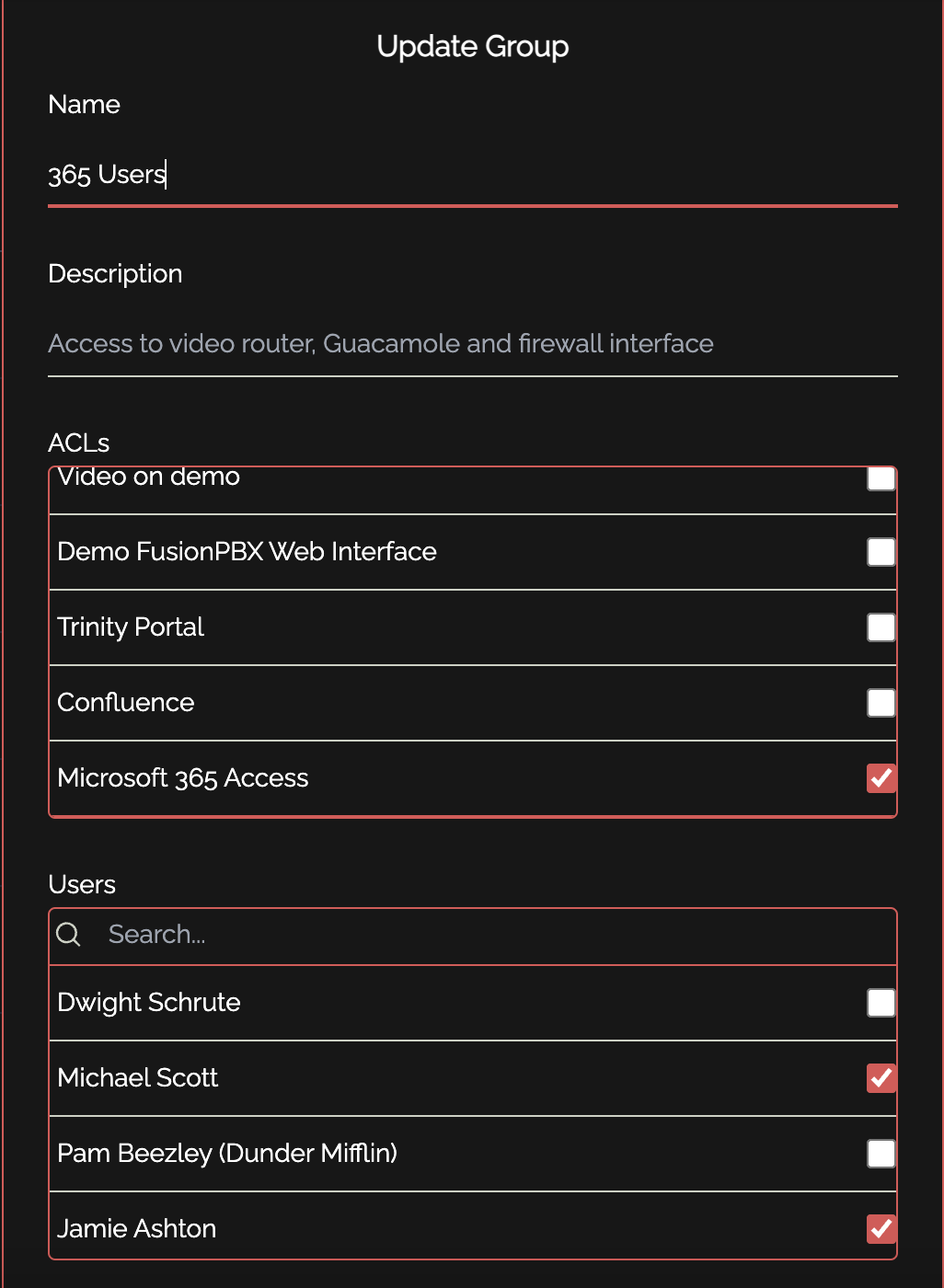
entra_tenantid="" entra_clientsecret=""Admin Portal ConfigurationTo get this integration working in your knocknoc admin portal, there are a few simple steps to follow:Create a new backend for Microsoft 365. This is how knocknoc interacts with the scripts to make changes to conditional access policies. The shell script is located at/opt/knocknoc-agent/scripts/update-entra-acl.shby default:Create one or more ACLs in knocknoc. These correspond to your various "knocknoc_acl" conditional access policies you made in entra earlier. You can add as many of these as you want, but make sure they are unique!You also want to make sure your description is clear in showing the user what they are being given access to. For example, if this particular ACL is controlling access to the admin portal, you might have a description such as "Microsoft 365 Admin Portal." You must also place a URL, where they will be redirected to if they click on the ACL in their user portal. This should also be relevant to the service in which the ACL is granting access to.The final step is to assign the ACL and relevant users to a group:
AndClickyou're done! This is all that is required to enable integration between knocknoc and Microsoft 365 for conditional access policies. If you get stuck, reach out and we will gladly assist.Save -