How Knocknoc removes attack surface
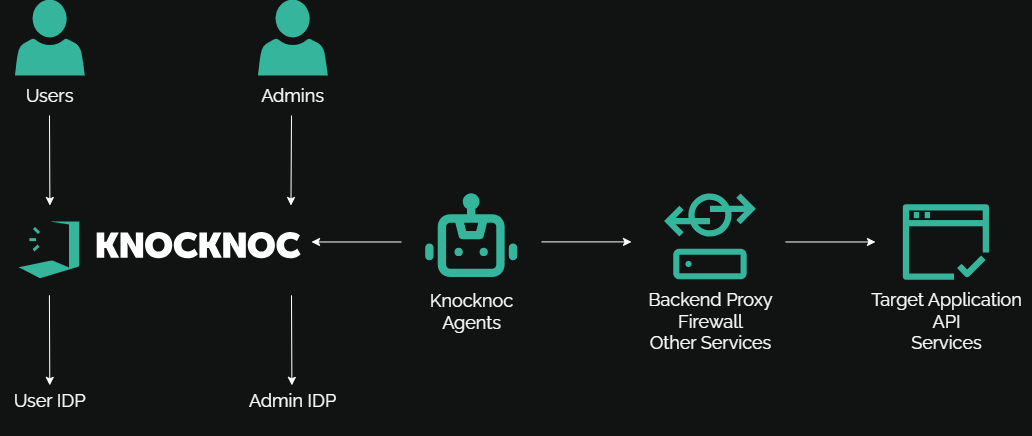
WelcomeKnocknoc enables you to remove the attack surface of systems, by enacting just-in-time network-based allow-listing.
It can operate in a number of ways - from orchestrating network access controls (eg: adding to firewall rules) whilst presenting no attack surface, through to operating as an identity aware gateway, or any combination thereof.
Knocknoc orchestrates a devices firewall by providing it the IP address of a user who has successfully logged in to a centralised portal. It is not a proxy, it is not a VPN. You host it or we host it, with support for access control layers of all types - commercial, open-source, public cloud providers and more.
A simple example is an SSH bastion host. Typically, SSH is exposed to the entire Internet, allowing any IP address to make a login attempt or otherwise access the port, daemon/service and network stack - presenting an attack surface.
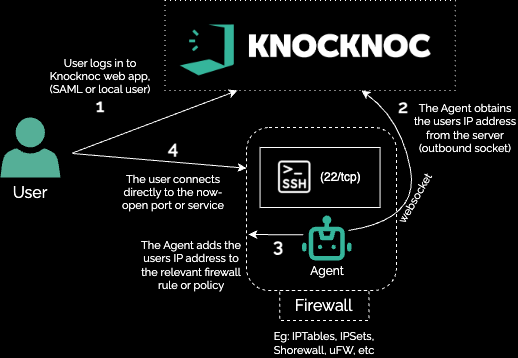
To solve this, a Knocknoc "agent" is installed on the bastion host which dynamically adds a users IP address to a firewall rule or policy, which opens SSH at the network level. It does so only after the user has centrally logged in to the Knocknoc Adminportal, Guide.which sits elsewhere. The SSH port is only made visible to the users IP address after the Knocknoc login.
This allows you to haveremove fine-grainedthe controlattack over what resources eachsurface of yourhosts usersand services (eg: SSH) very quickly, or to protect VPN services on devices like Fortinet, Palo Alto and Ivanti etc - removing their entire attack surface from the Internet.
Operating models
Knocknoc can access.be Knocknocdeployed consistsin a number of ways - talk to us about your architecture or use case.
- On-host orchestration. An Agent is installed directly on a host which securely adds IP address information to a firewall rule or policy. This could be a single host offering services, a Linux-based firewall with multiple network interfaces, or a machine running a large virtual environment (eg: Proxmox/VMWare) with numerous virtual interfaces and failover/cluster considerations.
- Adjacent orchestration. An Agent is deployed alongside infrastructure it can orchestrate, for example, the API of a
server,Fortinet or Palo Alto/Checkpoint which the Knocknoc Agent interacts with, holding tightly constrained access permissions allowing only an IP address to be added/removed from a specified policy based on API credentials. This mode can also manage public cloud provider controls/APIs, eg: AWS/Azure, Digital Ocean. - AllowList (passive) mode. A firewall can be configured to dynamically source trusted IP address information from Knocknoc. These IP lists are securely published and consumed by firewalls which support external dynamic lists. This obviates the need for a Knocknoc Agent to be deployed anywhere in the environment.
- Identity Aware Gateway. Knocknoc can also be deployed to act as an identity aware gateway. This is effectively a reverse-proxy that sits in-line between your client/users and the back-end protected system(s). Only after a central login is the users IP address permitted. This allows layer-7 filtering and access control, meaning web-requests or POSTs to /admin/ require a Knocknoc login, whereas requests to other paths do not.
- Combination. Knocknoc can be deployed in any combination of the above. The per-user license model means you can start small and simple, and increasingly reduce your attack surface over time.
Talk to us about your architecture and we'll help get you going.
Other modes include centralised orchestration, where usersas authenticate,Knocknoc Agent server is established which interacts with a number of orchestrated systems. This could be AWS, Azure, Entra, Digital Ocean and agentscloud whichproviders, updatewhilst also orchestrating adjacent firewalls or executing custom scripts. The options here are near limitless.
Security model
Knocknoc Agents connect outbound to your Knocknoc server via HTTPS and maintain a websocket connection. After a user logs in, their IP address information is then shared across this websocket, meaning the backendAgents ACLshave withno thedirect user'sattack IPsurface.
Get going
Setting up Knocknoc for the first time can appearis easy, but please have a read through the Getting Started guide as it will runruns through the install and setup process.
This guide and covers installation, administration, tuning and troubleshooting. For general access guides, here is the simplified User Guide.
For new admins we recommend checking out the Consider Your Use Case and Understanding Access Control pages to understand how Knocknoc fits into your security architecture.
Defence in Depth
In most cases, users are expected to authenticate to the target resources as well, with this in mind consider Knocknoc as part of a comprehensive defence strategy. In other cases, like video feeds, or SIP connections, extra authentication isn't workable, so you need to decide as part of your security strategy how to manage these risks.