FortiOS, FortiProxy, Palo Alto, or SSL VPN
Protect your existing Fortigate or Palo investments from direct internet exposure by introducing Knocknoc.
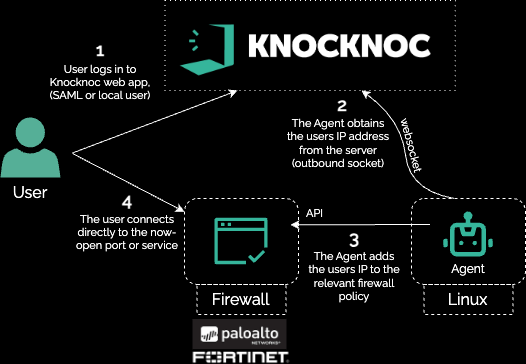
This can be achieved in multiple ways through directactive or indirectpassive firewall orchestration , effectively adding network application whitelisting only after a successful authorized user login to the network edge.
Shown below is the direct-orchestration model, where Knocknoc adds the trusted/authenticated IP address to the relevant policy on the Fortinet, exposing the VPN services to an IP address only after they have successfully authenticated.
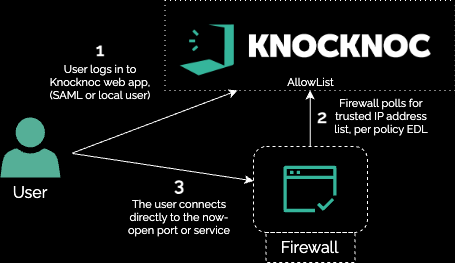
Alternatively an agentless deployment can be established using the AllowList feature:
This can be combined in a passive-allowlist model along with an API call which updates the policies (causing a live poll), giving you the best of both worlds - low privilege API access along with a polled allowlist.
This can be used to remove the attack surface of VPN services/protocols prior to centralized login or prevent asset exposure to zero-day attacks as they simply inaccessible.
If you need to urgently reduce direct exposure of your Fortigate, Palo or other appliances, please talk to us.