Microsoft Entra
Overview
This integration is designed to manage named locations in Microsoft Azure Conditional Access policies via the Microsoft Graph API. It allows users to add, delete, or flush named locations related to specific IP addresses. This integration with knocknoc enables IP whitelisting within Microsoft 365. An example of a user's experience can be found below:
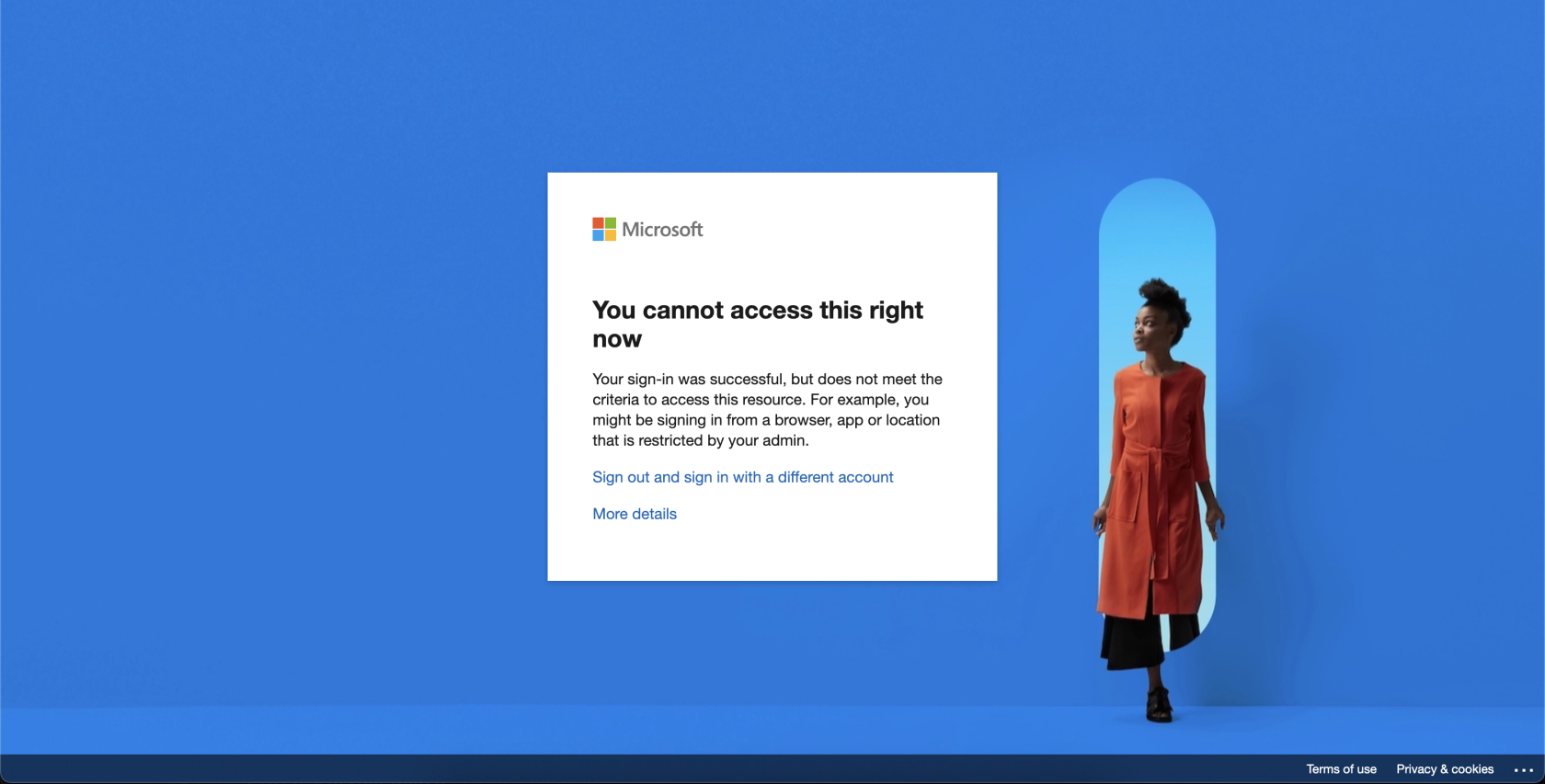
- User attempts to access Microsoft 365 services:
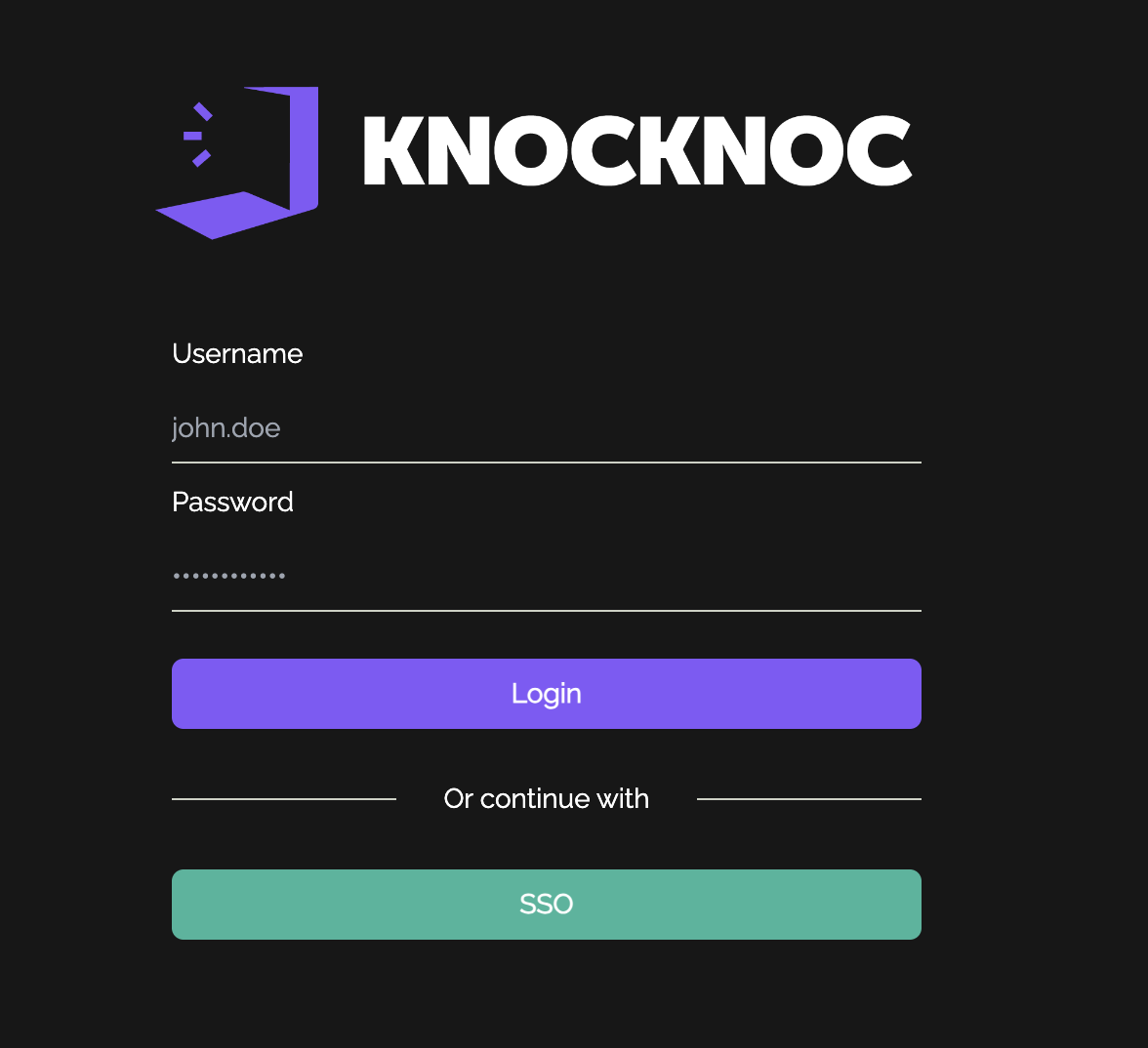
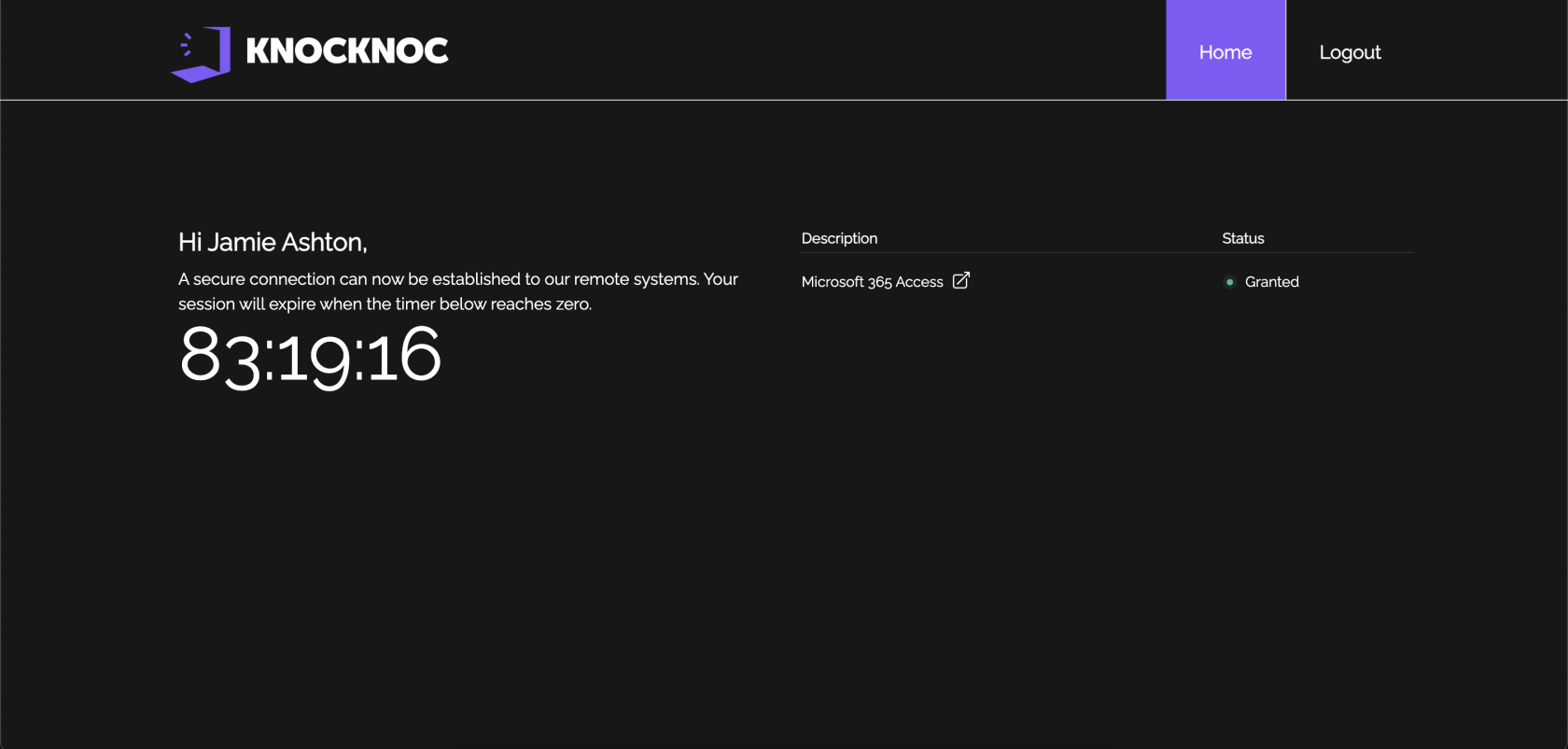
- User must authenticate with knocknoc and will see their granted ACL on the right hand side:
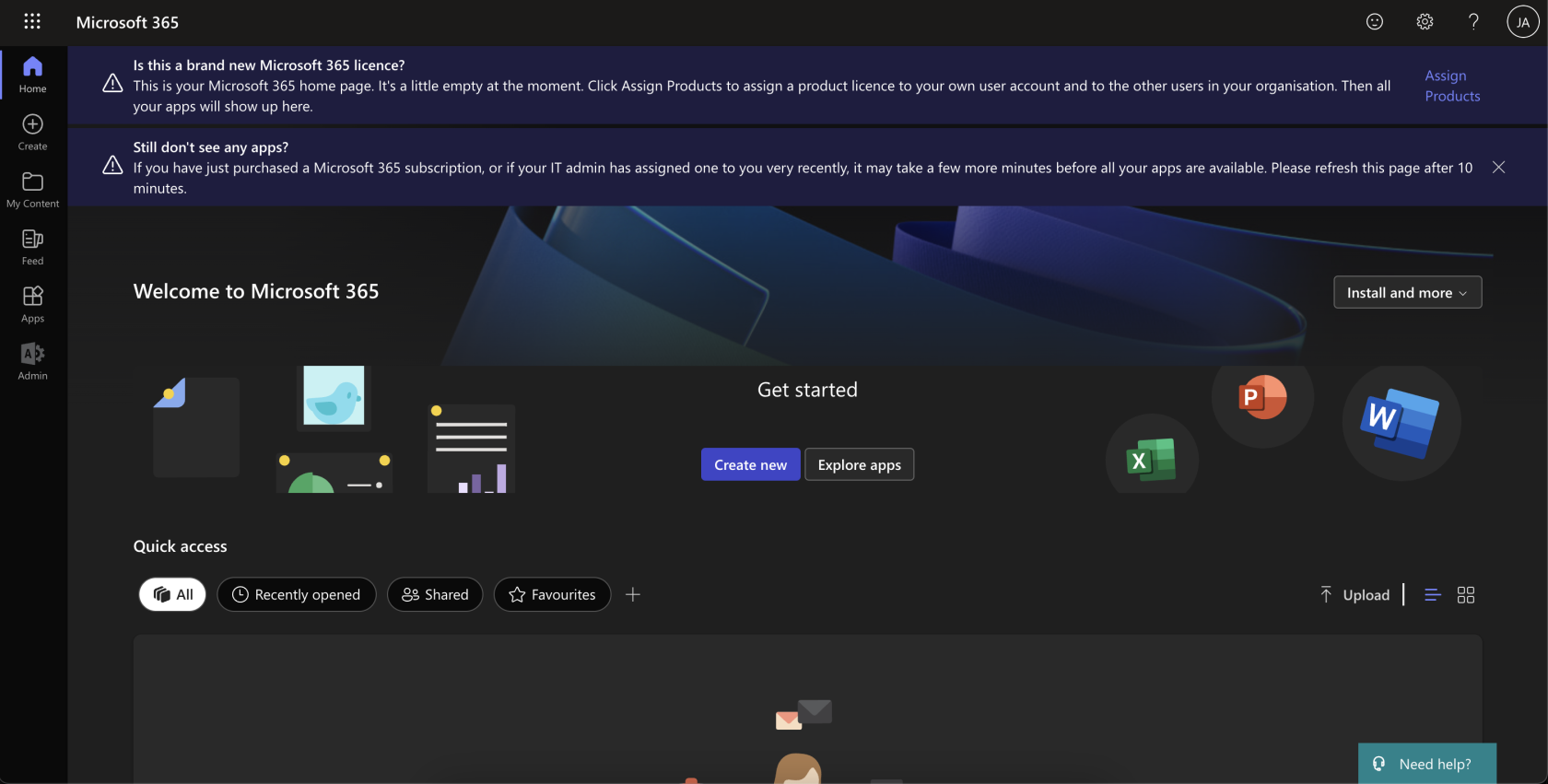
- User can now access Microsoft 365 services:
Prerequisites
Before running this script, ensure that you have the following prerequisites installed and configured:
- Powershell - Install PowerShell on your system. For Debian, follow these steps:
# Update the list of packages sudo apt-get update # Install pre-requisite packages. sudo apt-get install -y wget # Download the PowerShell package file wget https://github.com/PowerShell/PowerShell/releases/download/v7.4.3/powershell_7.4.3-1.deb_amd64.deb ################################### # Install the PowerShell package sudo dpkg -i powershell_7.4.3-1.deb_amd64.deb # Resolve missing dependencies and finish the install (if necessary) sudo apt-get install -f # Delete the downloaded package file rm powershell_7.4.3-1.deb_amd64.deb - Azure Enterprise Application: An enterprise application must be created to allow knocknoc to authenticate and change conditional access policies and named locations. Create an enterprise application, create a client secret, and copy the application's client id, azure tenant id and secret. You'll need these later.
-
Microsoft Graph API Permissions: Ensure that the application has the necessary permissions to access the Microsoft Graph API, particularly for managing conditional access policies and named locations. These can be found below:
API NameClaim valuePermissionTypeGranted throughGranted byMicrosoft GraphUser.ReadSign in and read user profileDelegatedAdmin consentAn administratorMicrosoft GraphPolicy.ReadWrite.IdentityProtectionRead and write your organization’s identity protection policyApplicationAdmin consentAn administratorMicrosoft GraphPolicy.ReadWrite.FedTokenValidationRead and write your organization's federated token validation policyApplicationAdmin consentAn administratorMicrosoft GraphPolicy.Read.ConditionalAccessRead your organization's conditional access policiesApplicationAdmin consentAn administratorMicrosoft GraphPolicy.ReadWrite.PermissionGrantManage consent and permission grant policiesApplicationAdmin consentAn administratorMicrosoft GraphPolicy.ReadWrite.ConditionalAccessRead and write your organization's conditional access policiesApplicationAdmin consentAn administratorMicrosoft GraphPolicy.ReadWrite.AuthenticationMethodRead and write all authentication method policiesApplicationAdmin consentAn administratorMicrosoft GraphPolicy.Read.PermissionGrantRead consent and permission grant policiesApplicationAdmin consentAn administratorMicrosoft GraphPolicy.ReadWrite.AuthenticationFlowsRead and write authentication flow policiesApplicationAdmin consentAn administratorMicrosoft GraphPolicy.ReadWrite.ApplicationConfigurationRead and write your organization's application configuration policiesApplicationAdmin consentAn administratorMicrosoft GraphApplication.ReadWrite.AllRead and write all applicationsApplicationAdmin consentAn administratorMicrosoft GraphPolicy.ReadWrite.ConsentRequestRead and write your organization's consent request policyApplicationAdmin consentAn administratorMicrosoft GraphPolicy.ReadWrite.ExternalIdentitiesRead and write your organization's external identities policyApplicationAdmin consentAn administratorMicrosoft GraphPolicy.ReadWrite.SecurityDefaultsRead and write your organization's security defaults policyApplicationAdmin consentAn administratorMicrosoft GraphPolicy.Read.AllRead your organization's policiesApplicationAdmin consentAn administratorMicrosoft GraphPolicy.ReadWrite.CrossTenantAccessRead and write your organization's cross tenant access policiesApplicationAdmin consentAn administratorMicrosoft GraphApplication.Read.AllRead all applicationsApplicationAdmin consentAn administratorMicrosoft GraphPolicy.ReadWrite.AuthorizationRead and write your organization's authorization policyApplicationAdmin consentAn administratorMicrosoft GraphPolicy.ReadWrite.FeatureRolloutRead and write feature rollout policiesApplicationAdmin consentAn administratorMicrosoft GraphPolicy.Read.IdentityProtectionRead your organization’s identity protection policyApplicationAdmin consentAn administratorMicrosoft GraphPolicy.ReadWrite.TrustFrameworkRead and write your organization's trust framework policiesApplicationAdmin consentAn administratorMicrosoft GraphPolicy.ReadWrite.AccessReviewRead and write your organization's directory access review default policyApplicationAAn administrator - Conditional Access Policy/Policies: Knocknoc needs to be able to distinguish between policies it can amend and policies it cannot. Therefore, knocknoc looks for a prepending "knocknoc_" ahead of the name of the ACL. For example, a conditional access policy might be named "knocknoc_financedepartment" with specific rules around applications and services that group can access. These must be created PRIOR to configuring anything in the knocknoc admin portal.
-
Credentials File: Ensure that a credentials file is present at
/opt/knocknoc-agent/etc/entra-credentials.shwith the following content:entra_clientid="" entra_tenantid="" entra_clientsecret=""You will need to input the necessary ClientID for your Azure Enterprise Application, your Azure Tenant ID and your application's client secret.