SAML with ADFS
The following example assumes your Knocknoc instance is located at https://demo.knoc.cloud. Wherever you see that, please substitute it for your own instance URL.
Create certificates
Create a key/certificate pair on your local machine
- Generate a new certificate and key, this can be done on a Linux host using the below command.
openssl req -new -x509 -days 3650 -nodes -subj /CN=Knocknoc/ -out user-demo-knoc-cloud.crt -keyout user-demo-knoc-cloud.key - Enter a password and note it down.
- This will be required for both sides of the connection, Windows AD FS and Knocknoc
Knocknoc SAML Config
- Login In the Knocknoc admin interface (eg: https://your-knocknoc.cloud/admin/)
- Click on Settings on the left.
- Under Public URL enter you knocknoc url. Note: do not add a / at the end of the URL.
- For the SamlMetadataUrl enter your ADFS host, adding /FederationMetadata/2007-06/federationmetadata.xml
- eg: https://your-adfs-site/FederationMetadata/2007-06/federationmetadata.xml
- For the SAMLCertFile, upload the certificate (.crt) file you created in during the Certificate creation.
- For the SAMLKeyFile, upload the key (.key) file you created in during the Certification creation.
- Click Save.
- You can verify this worked correctly by visiting https://your-knocknoc.cloud/api/saml/metadata and observing the downloaded metadata file.
Setting Up the IdP (ADFS)
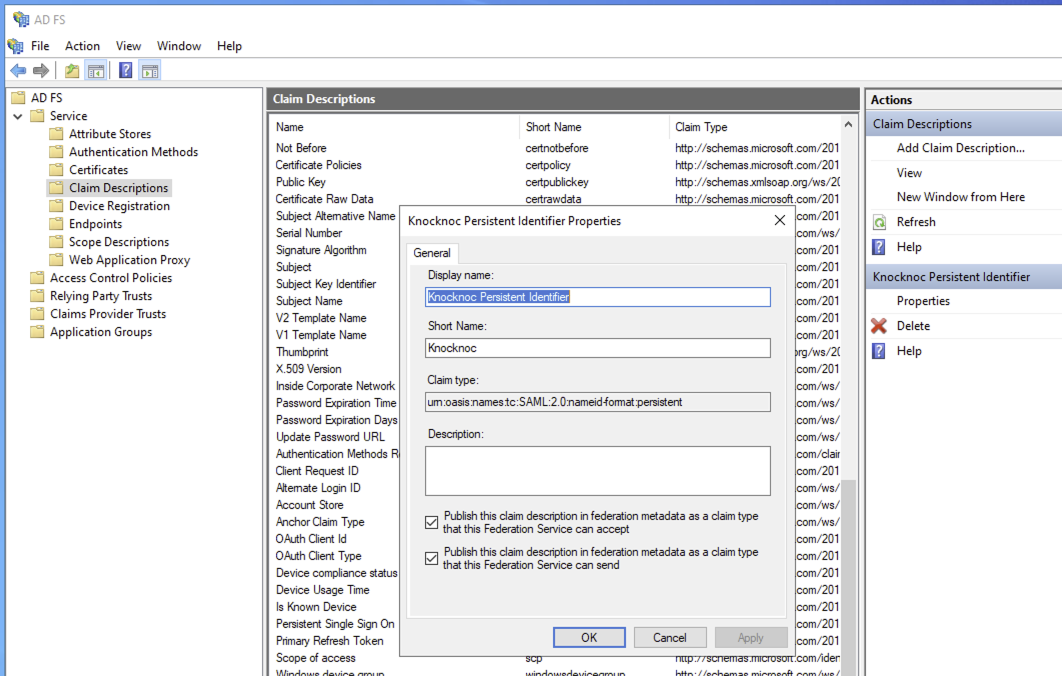
Define the Claim Description
Define the Relying Party Trust
Define the RelyingClaim PartyIssuance TrustPolicy
-
Once on the Edit Claim Issuance Policy section
- Click Add Rule
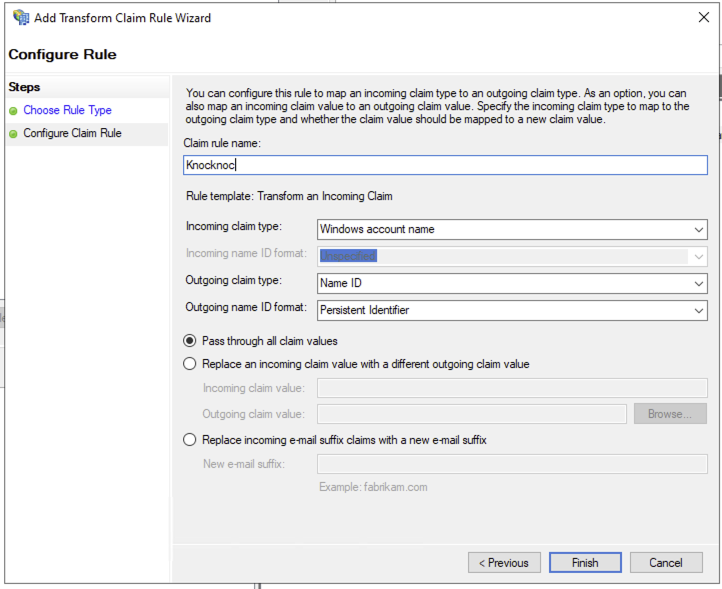
- Select Transform and Incoming Claim, click Next
- Name the rule, eg: Knocknoc
- Incoming claim type should be set to Windows account name
- Outgoing claim type: Name ID
- Outgoing name ID format: Persistent Identifer
- Click Finish and Apply
- It should appear similar to the below
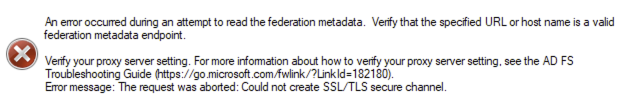
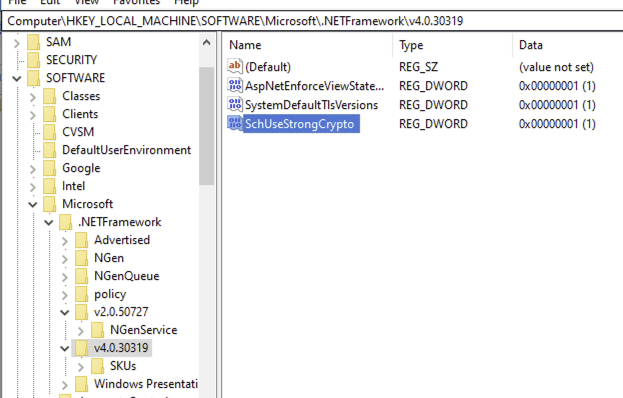
TLS errors and enabling TLS/1.2
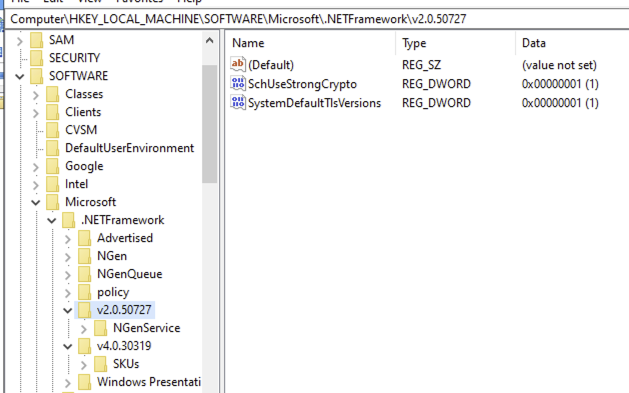
If you receive TLS/SSL errors trying to validate the metadata file, you may need to enable TLS/1.2 via your registry.
Registry configuration to enable TLS/1.2:
Assign Groups
Click "Assign users and groups"Click "None Selected" under groups.Add the user groups you wish to access Knocknoc protected services.
Note: Knocknoc and EntraID group names need to match for automatic user assignment. Best practice is to have at least one group per Knocknoc protected service.
SAML Configuration
Click Set up single sign on.Click SAML.In the Basic SAML section, add the links to your Knocknoc instance.Set the Indentifier (Entity ID) tohttps://demo.knoc.cloud/api/saml/metadataSet the Reply URL (Assertion Consumer Service URL) tohttps://demo.knoc.cloud/api/saml/acsLeave the Optional Basic SAML Configuration options blank at this stage and click Save.
In the Attributes & Claims sectionUpdate the Required Claim, changing the Name Identifier Format to Persistent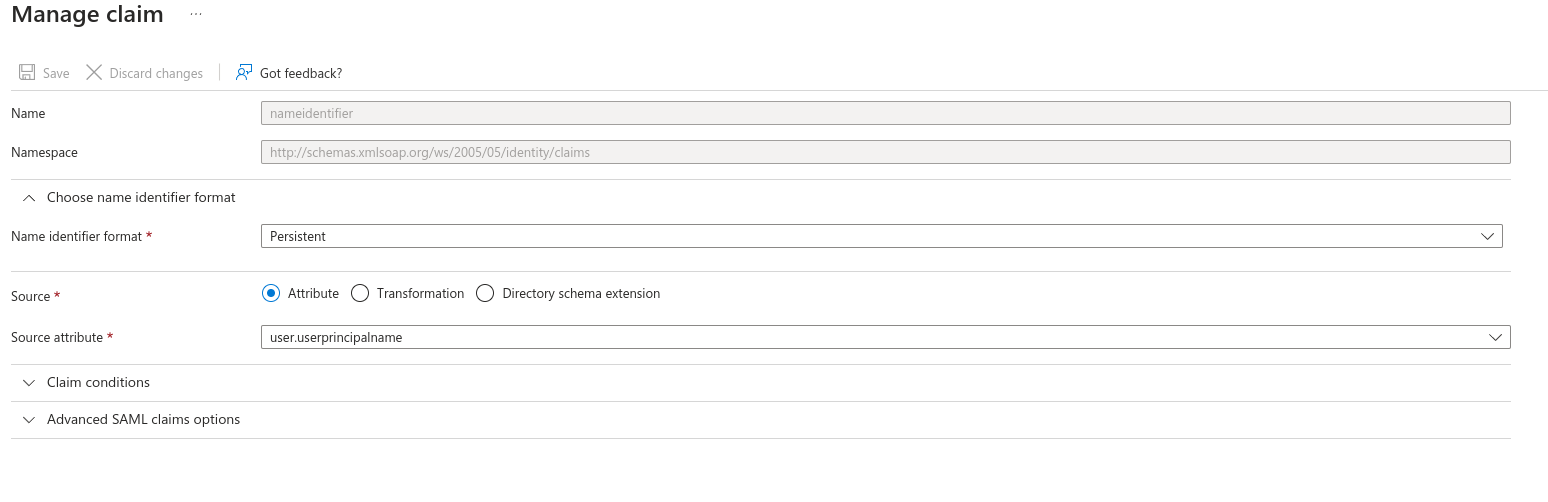
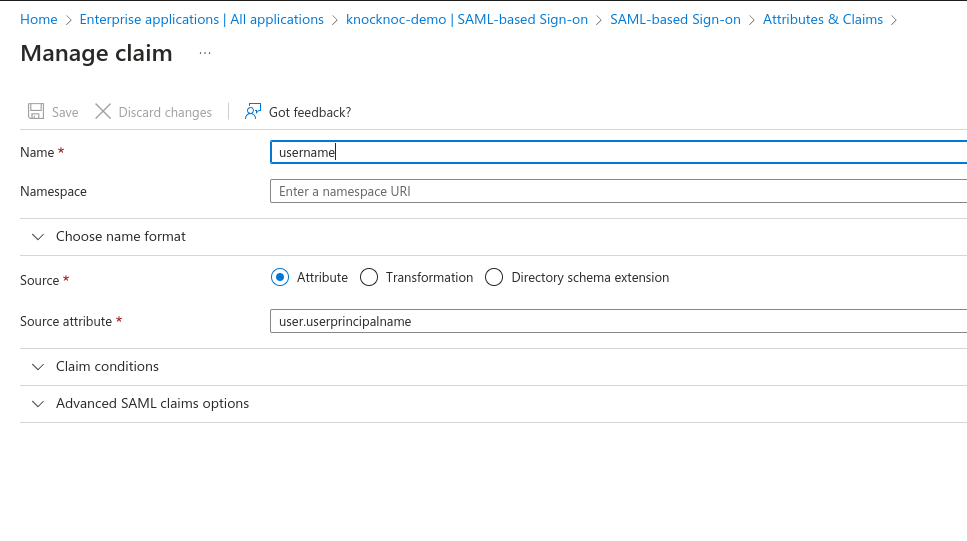
Remove all other Claims.Add a group Claim.Select Security GroupsSelect Group ID for the Source Attribute.Check "Customize the name of the group claim" Under Advanced OptionsAdd the Name as, groups.Click save when done.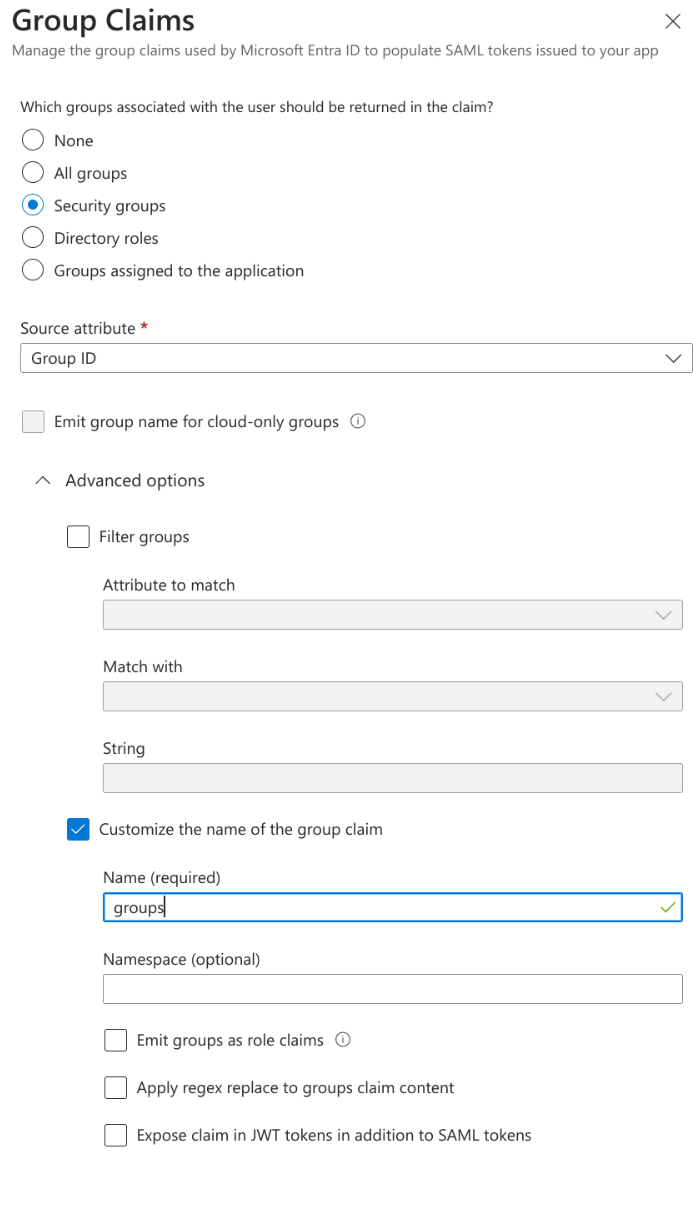
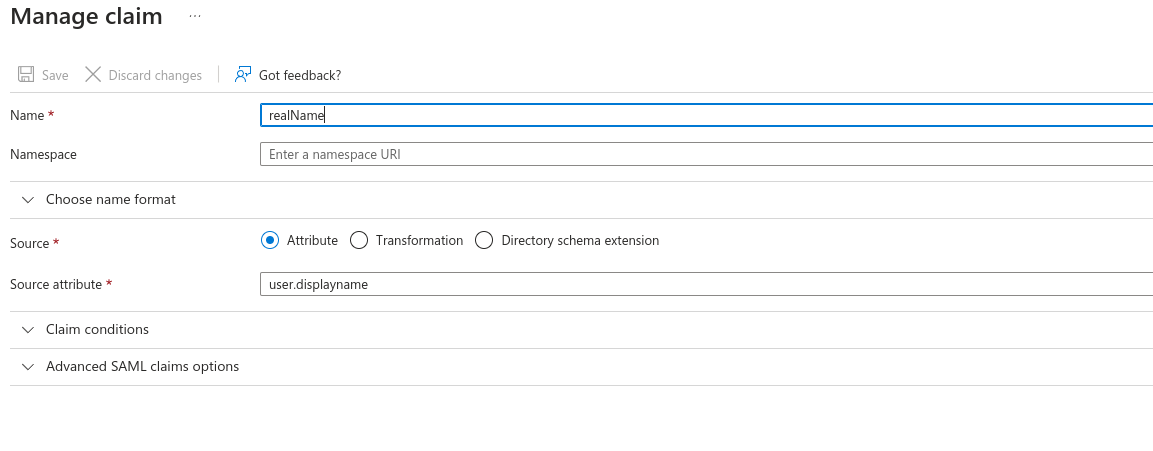
Add in a New ClaimAdd another New ClaimSet the Name as "sessionDuration"Leave Source as Attribute.Set Source Attribute to the default login duration in seconds for users logging in to Knocknoc. You can manually override this with a user attribute later for specific users.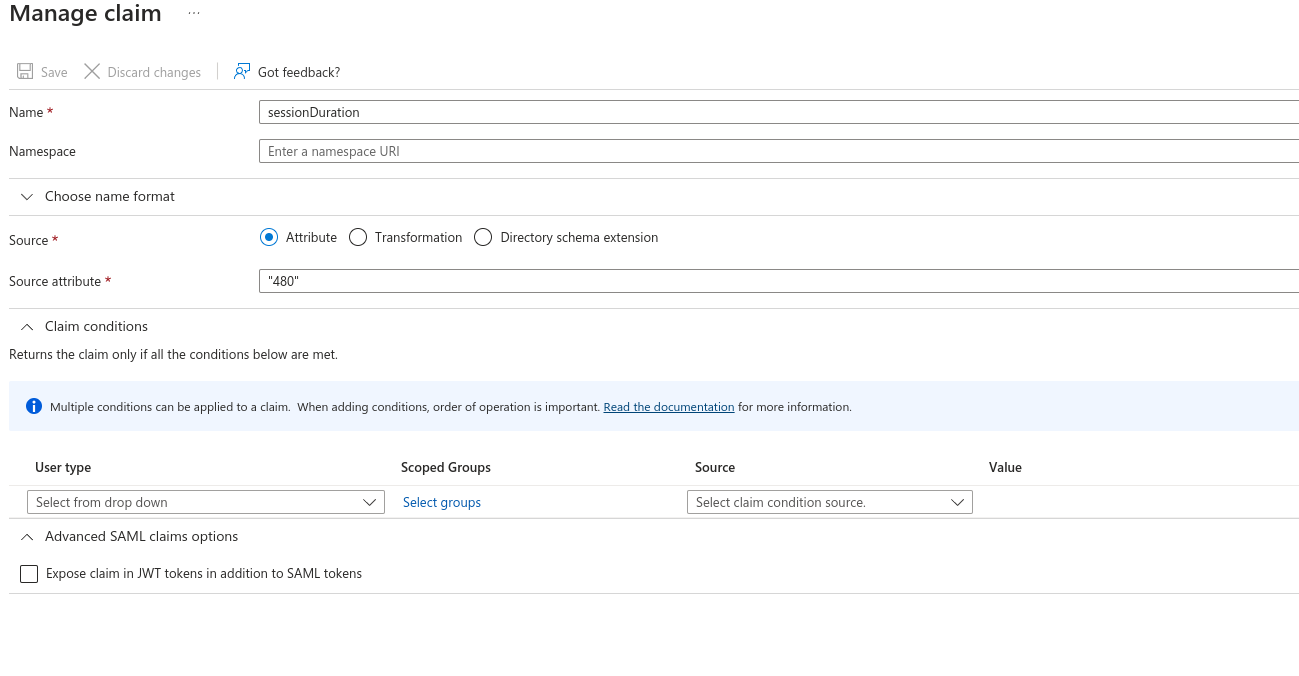
Add a third New Claim
Go to SAML Certificates sectionGenerate a new certificate and key, this can be done on a Linux host using the below command.openssl req -new -x509 -days 3650 -nodes -subj /CN=Knocknoc/ -out user-demo-knoc-cloud.crt -keyout user-demo-knoc-cloud.keyConvert the certificate to pfx using the following command.openssl pkcs12 -export -out user-demo-knoc-cloud.pfx -inkey user-demo-knoc-cloud.key -in user-demo-knoc-cloud.crtEnter a password and note it down.Import Certificate, select the pfx certificate you just created and enter the password.Then make the new certificate Active by clicking the dots on the right and choosing Make Certificate Active.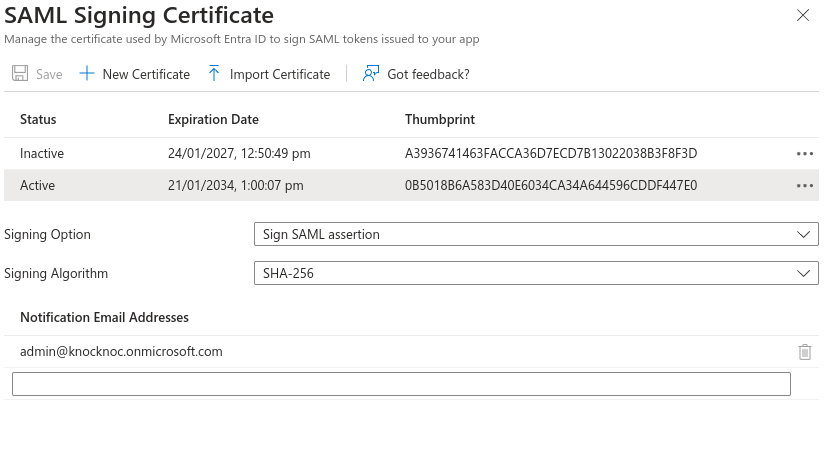
Download the federation Metadata XML.
Set Up KnocknocCopy the Login URL, this will be required for the Knocknoc SAML config.
Knocknoc SAML Config
Login In the Knocknoc admin interface.Click on Settings on the left.Under Public URL enter you knocknoc url.Note: do not add a / at the end of the URL.For the SAMLMetaDataFile, upload the xml file you downloaded from EntraID.For the SAMLCertFile, upload the certificate (.crt) file you created in during the SAML Configuration.For the SAMLKeyFile, upload the key (.key) file you created in during the SAML Configuration.For the SAMLMetadataUrl, paste the Login URL copied in Step 6 of the previous section.Click Save.
Final Testing
Assuming you granted your own user permission to one or more Knocknoc groups in EntraID, you should now be able to login to Knocknoc using SSO.
- Browse to https://demo.knoc.cloud
- There should now be an "SSO Login" button.
- Click this, if you are not already authenticated to your IdP you should now be directed to the IdP login page. Note: If you are already authenticated you'll simply be redirected to an authenticated Knocknoc session.
- If ACLs have already been added you should also see these now say Granted.
If this all works, congratulations! You've successfully run the SAML gauntlet.