FortiManager
The FortiManager is used to manage multiple Fortinet devices, including Fortigate firewalls, APs, switches and more. Utilizing Knocknoc with FortiManager local-in access controls can be applied, limiting exposure to Admin login source addresses dynamically.
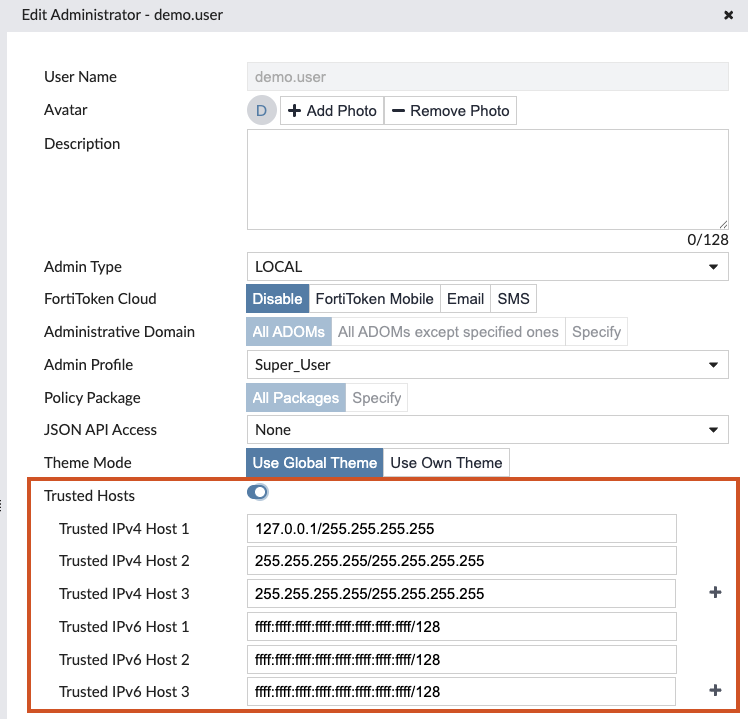
Trusted hosts (IPv4/IPv6)
Administrator users can have up to 10 IPv4 and 10 IPv6 trusted-host IP-source address restrictions, which limit login access to those IP addresses only. These are configured at creation time or when editing an existing Admin user, as below:
The first entry - Trusted Host 1 (for v4 and v6) - is intentionally not managed by Knocknoc, these should be set either to a trusted IP you control for break-glass/backup access, or to 127.0.0.1/etc as above.
Knocknoc does not manage this first entry by design, to provide a failsafe backup source address. Change the first entry from the default 0.0.0.0/0.0.0.0 (and v6) to a trusted IP address you control.
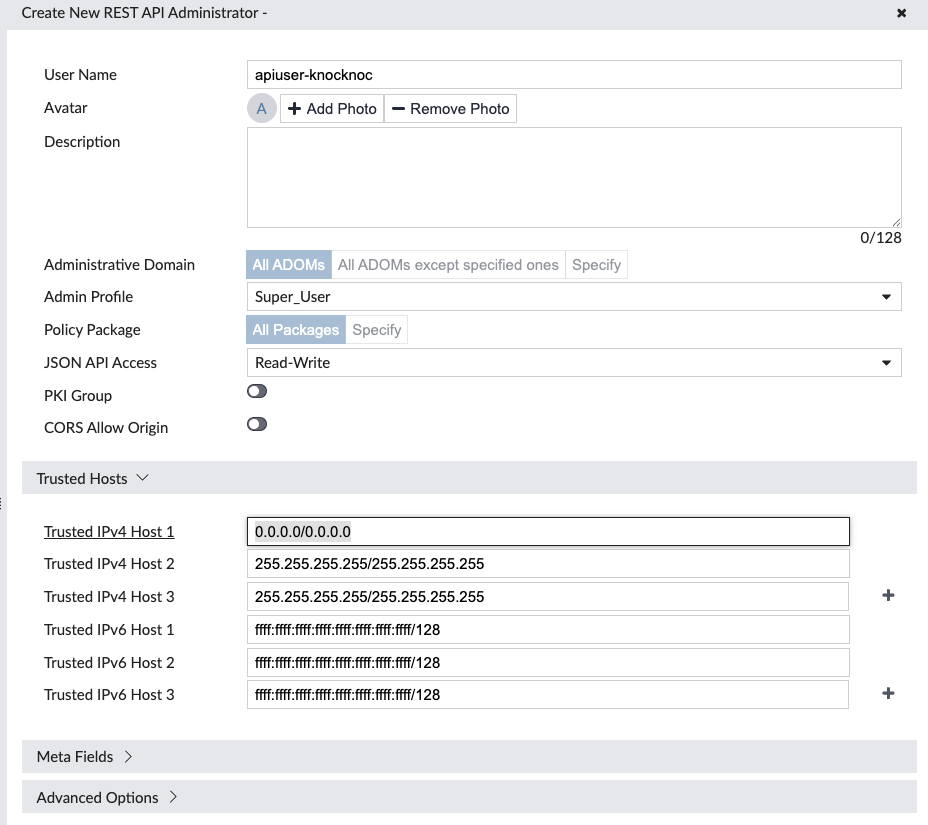
FortiManager API User
An API user must be configured for use by the Knocknoc orchestration agent, unfortunately due to FortiOS limitations this user must hold the Super_User role. Note that this API user can have their own source-IP restrictions set to reduce exposure.
Under Administrators, select "Create new" -> "API Rest Admin":
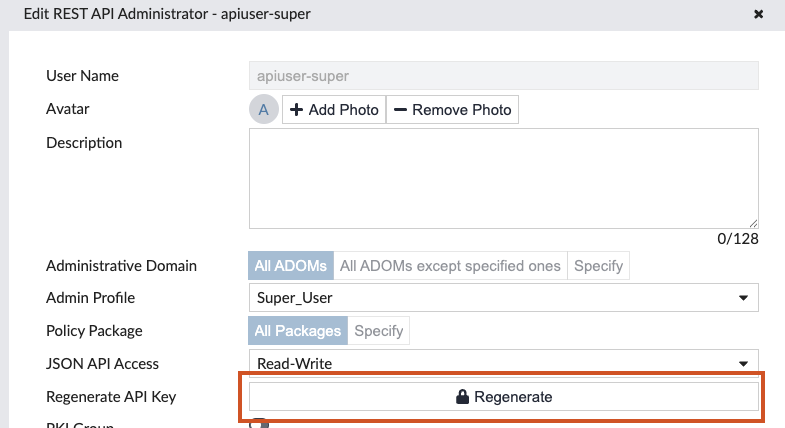
We recommend the IP restrictions are utilized to restrict access from the orchestration agent only.
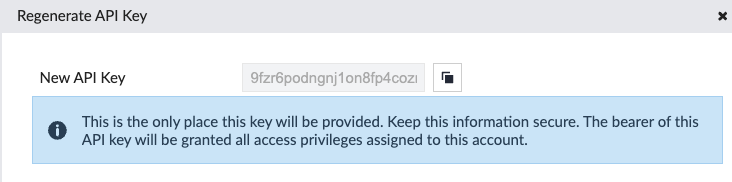
Once created, edit the user and regenerate the API key. This will be used in the next step configuring Knocknoc.
Knoc configuration
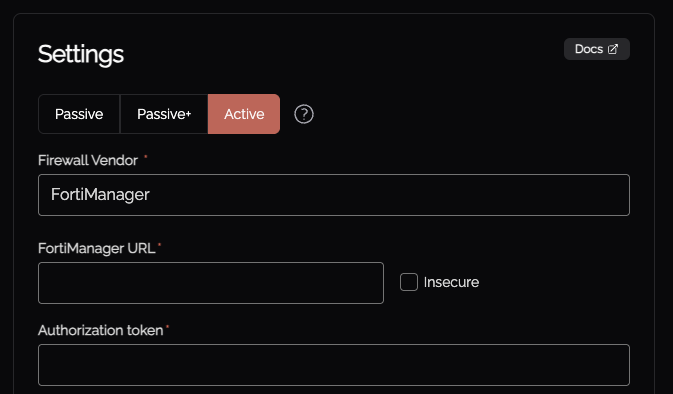
Select the "Firewalls / Appliances" Knoc configuration, selecting "Active", then "FortiManager"
Enter the URI of the FortiManager device, and the Token for the API user created above.
Assign users and groups to the appropriate FortiManager Admins within Knocknoc.
The username accessing Knocknoc must match the Admin username within the FortiManager device. Future versions will provide support for an alternative naming approach passed in via SAML.
Testing it out
Log in to the FortiManager from a trusted source (eg: the Trusted Host 1 IP address), or view as another Admin user.
Visit the Administrators, select the test user, view their Trusted Host restrictions.
Log in to Knocknoc using that username, then refresh the view in FortiManager. The users IP address should now appear in one of the entries 2-10.
Limitations
This applies the built-in FortiManager Trusted Host restriction. This is not a network-level firewall rule that prevents access to the FortiManager device itself, it only limits the source IP addresses for the selected Admin users as part of the authentication process.
This will not necessarily prevent vulnerabilities in the FortiManager platform from being exploited, as network level access can still be obtained by an attacker outside of the authentication process.