Consider Your Use Case
Knocknoc
Knocknoc can ultimately act as an authentication portal for many use cases. To simplify the setup to begin with, it helps to consider a single application to put behind Knocknoc, and build it out from there. Once you have added an application, configured and tested user and/or group authentication you can update your reverse proxy or firewall to block all traffic not authenticated via Knocknoc.
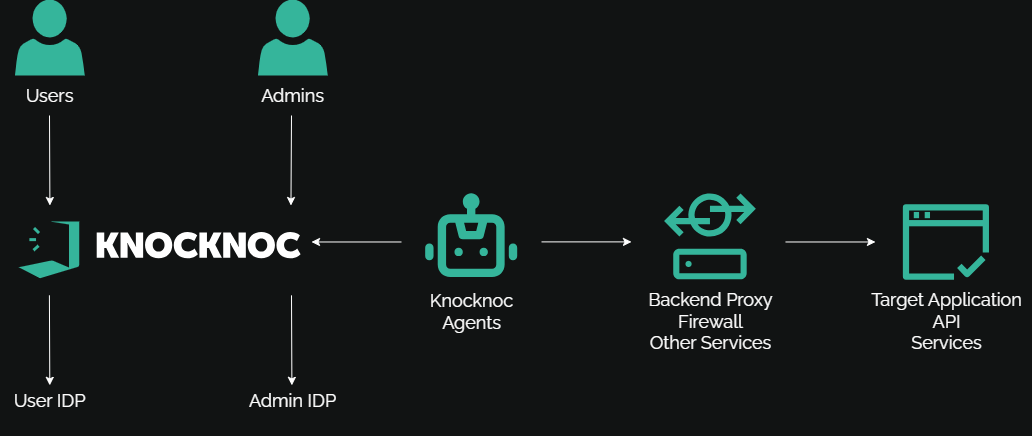
The architecture of a typical Knocknoc environment is often as follows:
Cloud or self-hosted server?
Should you deploy a cloud or self-hosted instance of Knocknoc?

The answer will depend on a few factors.
For example, if your LDAP authentication source is not on the internet, then of course you need self-hosted. A self-hosted Knocknoc server may also suit you better for various security segmentation scenarios, or even Knocknoc on the LAN, which is great for SCADA or ICS systems.
However, depending on your environmentenvironment, it may be hard to get inbound public IP access to the Knocknoc serverserver. inIn which casecase, cloud hosting would make sense. Our cloud servers are deployable in under a minute, with DNS records and inbound rules all configured for you ready to go.
Where will your agents run?
The Knocknoc agent connects out to the server over port 443/TCP (HTTPS), and maintains a secure web socket connection to manage your ACLS. The agent needs to live wheresomewhere itthat can reacheasily theaccess backendits itassociated isbackend. managing,For for exampleexample, a HAproxyHAProxy Unix socket is going to need to be on the same machine, or a firewall IPset or API might require the agent to be deployed in a control plane firewall zone. Deploying the agent is easy, and as long as you consider where in your network they live, this can strike a great balance between security and control.
Select your backends
The backend is a type of control mechanism, for example, a HAproxyHAProxy unix socket, an AWS security group script or a firewall IPset. The backend needs to be able to apply the change to your protected application instantly and idempotently. Knocknoc agents are resilient and will update ACLs on backends in a reliable fashion, however various backends have limitations. For exampleexample, an AWS security group can only have 60 entries before you need a support ticket,ticket. soPlease consider the limitations of any backends to ensure you maychoose wantthe tobest considerpossible ifsolution that suitsfor your use case.
